- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Educational Resources
- :
- Tip Of The Week
- :
- Blocking the connection before final rule match: C...
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Blocking the connection before final rule match: CPEarlyDrop
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
DeletedUser
Not applicable
7
5
65.9K
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
2018-10-17
04:23 PM
Somehow missed this in the discussion of the Unified Policy Column-based Rule Matching discussion, but encountered it recently when testing IPS. The drop log Access Rule Name is CPEarlyDrop and the log points to sk111643 Early drop of a connection before the final rule match which covers it well. The explanation pasted below is from the SK and this is also mentioned in ATRG: Unified Policy. Think it explains it pretty well. Check out the SK for more info.
The Unified Policy may contain filter criteria that cannot be resolved on a connection's first packet, such as Application or Data. Therefore, on some connections the final rule match decision is reached only on the following data packets.
However, the Rule Base may decide to block the connection at an early stage without a final rule decision, if all potential rules of the layer for a specific connection have a Drop or Reject action. This drop will issue a log with Rule Name "CPEarlyDrop" and hits will be counted for all the potential rules.
Layer potential rules are a list of rules that have matched the connection so far, according to filter criteria that were resolved for arrived packets (IP, port, VPN tunnel etc). Consider the following policy:
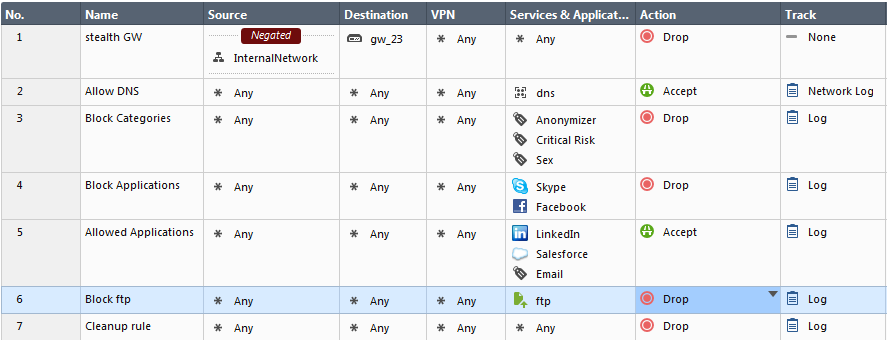
When the FTP connection is opened, the potential rules that match the first packet criteria are (4,6,7). The reason is because the Skype application is searched on any port, but the final conclusion for Skype matching can be determined only on data packets. Nevertheless, since all potential rules have a Drop action, the connection will be blocked on the first packet, even though the final decision of the rule-base was not made.
The Unified Policy is Smart (my comment).
5 Comments
About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


