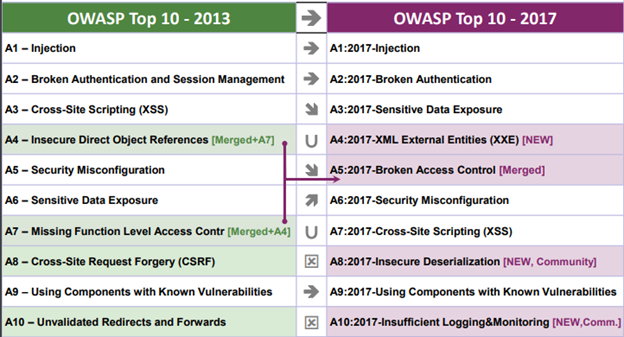
I am often asked to comment about the changes in the release of OWASP top 10 that was summarizing 2017 and as you can see not much has changed, mostly cosmetic priority and an item merge and three new items that were added mostly due community request, i.e. due survey answers by security experts and IT professionals:
Community items:
I think it is a good approach to ask the “hive mind” on their view on priority issues and add it to the top 10, as the top 10 is a reliable pointer to priority resources to the upper management. Letting CISOs an expert add to the list allows setting a best practice standard for the board meetings.
An even more innovating approach by OWASP was to add to the short list an item which is about preventing the damage as opposed to preventing the attack:
A10:2017-Insufficient Logging&Monitoring [NEW,Comm.]
“Exploitation of insufficient logging and monitoring is the bedrock of nearly every major incident.
Attackers rely on the lack of monitoring and timely response to achieve their goals without being detected.”
I can’t agree more with this statement, we at Check Point promote prevention as a core value.We do prevention with a layered holistic approach. As of the many attack vectors and different exploit scenarios with a mobile workforce and a flexible perimeter that includes SaaS applications and cloud infrastructure, a layered approach should micro-segment your network and hold attacks from moving laterally inside the network.
Having an automated fast response forensic report as we educate the industry using SandBlast agent.
Augmenting the Incident Response’s forensic investigation with automated fast response forensic report proved crucial in many real-life scenarios to contain the attack and prevent the attacker from using the beachhead created to achieve the target and create damage.
A8:2017-Insecure Deserialization [NEW, Community]
Another input from the industry survey was about insecure deserialization.From Oracle’s documentation: “To serialize an object means to convert its state to a byte stream so (the -GN) way that the byte stream can be reverted back into a copy of the object.”. I have some mixed thoughts about this item, as often the safe approach taken is to not allow any serialized objects. As a security advocate and product creator, one of my major tools is to create fast updates to the product in case there is a new attack vector we were not considering, which can be done with object serialization.
Trusting a maliciously crafted serial object can lead to Remote Code Execution. To prevent this developer should be educated about the dangers of serialized objects. “The only safe architectural pattern is not to accept serialized objects from untrusted sources or to use serialization mediums that only permit primitive data types.”. As we often see vulnerabilities in misplaced trust as of bad trust assumptions, OWASP advises “Implementing integrity checks such as digital signatures on any serialized objects to prevent hostile object creation or data tampering”.
OWASP decision to raise awareness and educate developers about this common vulnerability is very much in place.
A4:2017-XML External Entities (XXE) [NEW]
Another attempt to raise developer awareness is for XXE vulnerabilities as “By default, many older XML processors allow specification of an external entity, a URI that is dereferenced and evaluated during XML processing.”.
See easy explanation on the OWASP page:
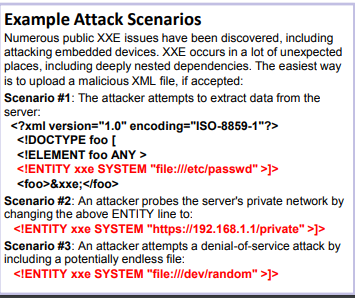
This vulnerability can be a good data collection point in a reconnaissance stage to understand the network topography an adversary is attacking. Giving an attacker an internal view into your network structure allows a more stealth attack after scanning for the servers.
Educating the developers and automatic vulnerability testing is very important, and a good advice is to move to using lex complex file formats like JSON is always important but OWASP suggestion of using virtual patching will allow you another layer of protection.
Happy vulnerability hunting,
Gadi




