- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Threat Prevention
- :
- Re: Usercheck Block Page is Insecure/Private
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Usercheck Block Page is Insecure/Private
- Application Control & URL filtering is enabled
- HTTPS Inspection is also enabled. Outbound Certificate is deployed in the organization and No SSL error, thanks to that. Can see HTTPS outbound certificate on browsing Internet.
- When trying to access a blocked http://website_A, block page appears.
- When trying to access a blocked https://website_A, Connection is insecure / private message appears and when selected to proceed Block page appears. Certificate on the block page is not same as HTTPS Outbound certificate. Extracted the certificate from browser and installed the same. Still at every other blocked https://website_X , connection is not secure prompt is shown before proceeding manual to block page
Customer is getting the Connection is not secure prompt before usercheck block page. Customer is quite cautious towards compliance and even the HTTPS Inspection Outbound certificate has been created with sha 256 algo.
As per customer HTTPS Usercheck Block page is not compliant as per there organization policy because it gives prompt for page being not secure
how to solve the same?
Dameon Welch Abernathy help here ![]()
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please check if the UserCheck URL is changed to https. By default, it is http:
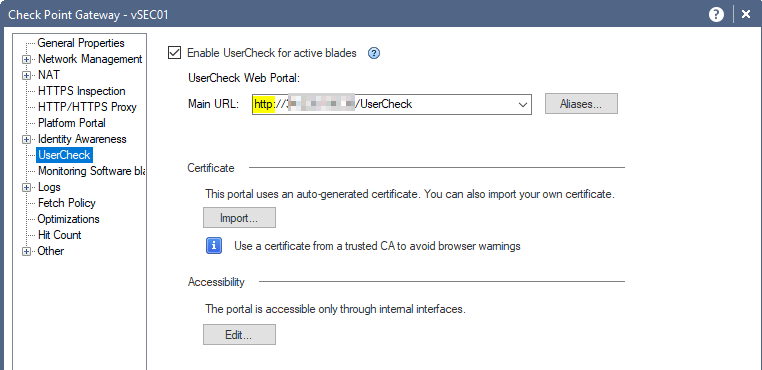
Additionally, make sure that once the https is enabled, the Root CA issuing the certificate is added to your clients' Trusted Root CAs IN ADDITION to the actual certificate for that of the UserCheck portal.
Otherwise, validation of the Issuing CA's certificate will fail.
You may find this of interest or help:
…possible reason you are keep getting the “untrusted” messages in the browsers is due to your CheckPoint Management Server’s certificate not being included in the Trusted Root CAs.
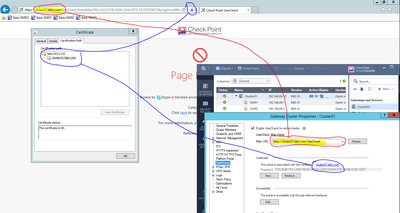
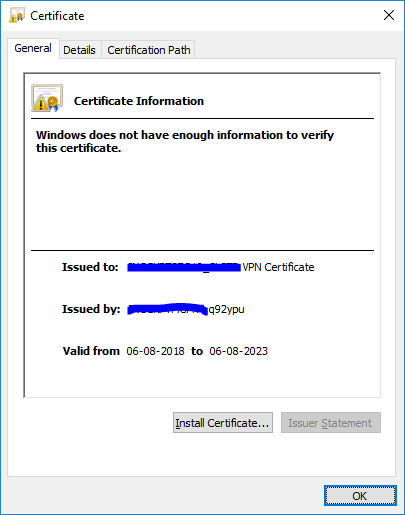
"This portal using an auto-generated certificate. You can import your own certificate" is actually referring to the VPN cert.
When browser sees the VPN cert, it is trying to verify who has issued it and if it can trust the issuer.
The VPN cert is issued not by the gateway, but by the Management Server.
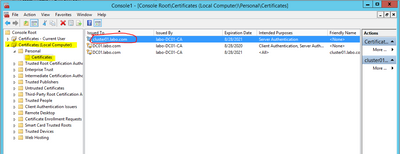
For you not to see warnings for UserCheck and VPN, three certificates must be installed in each computer’s Trusted Root CAs:
- SSL/HTTPS Inspection certificate
- Cluster’s VPN certificate
- Management Server’s Root CA certificate
See the screenshots below:
- Working VPN Cert:
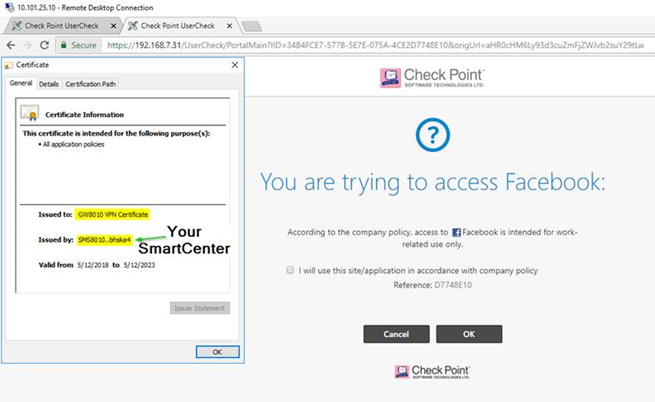
2. Exporting VPN Cert using Chrome
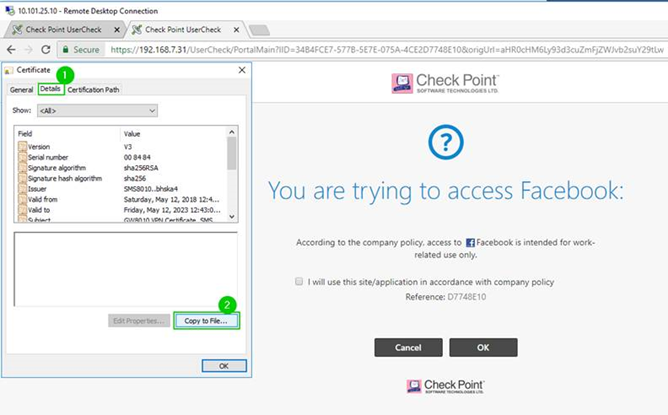
3., 4. Exporting VPN Cert Using Chrome continues
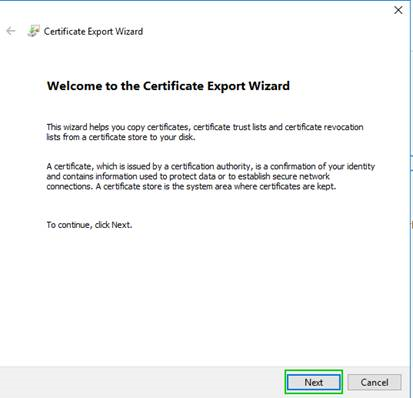
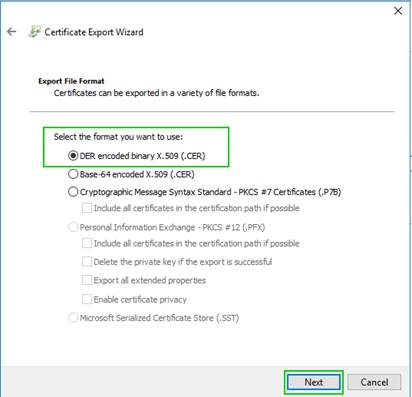
5. Saving VPN Cert
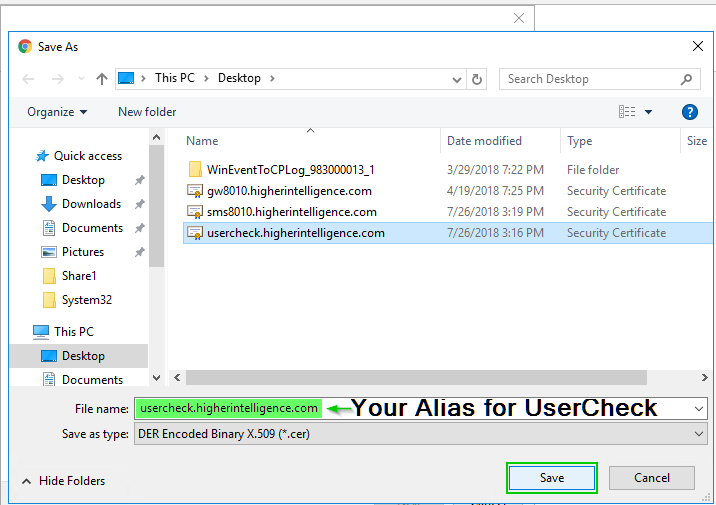
6. Navigating up the Certification path (In “General” tab, we are still looking at the VPN Certificate, but in Certification Path, we are moving to the Root)
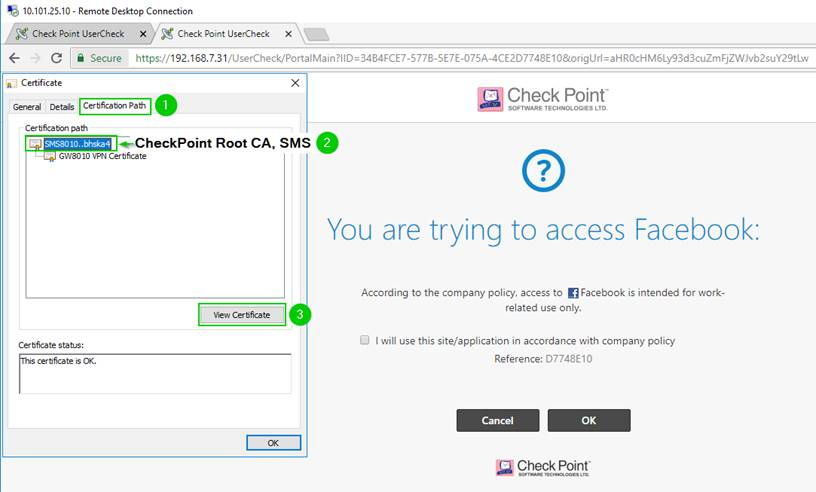
7., 8. Root CA Certification export continues
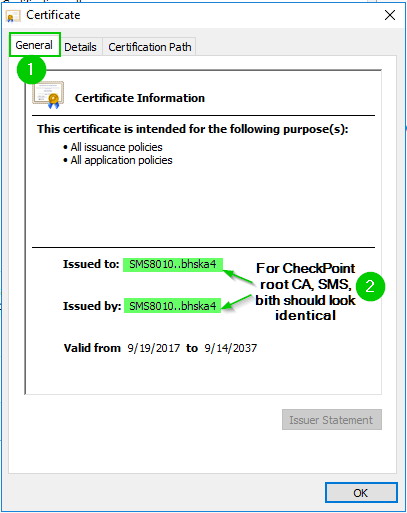
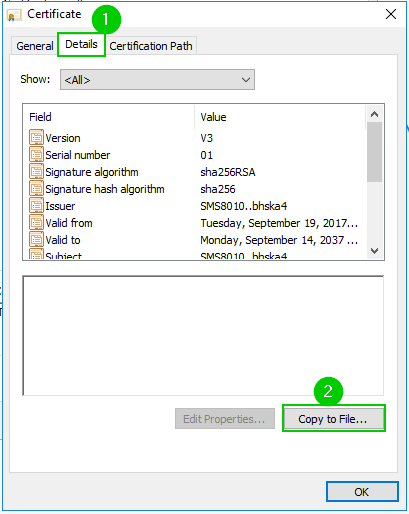
9., 10. Root CA Certification export continues
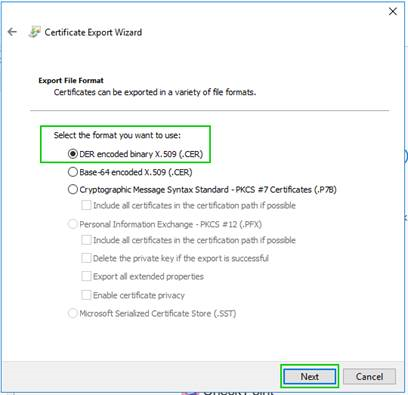
11. Saving CheckPoint Management Root CA
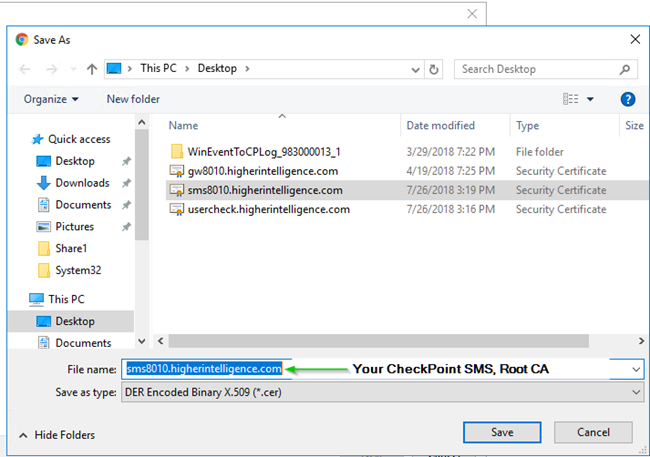
12. All three certificates must be present in Trusted Root CAs on every computer to avoid certificate warnings with UserCheck and VPN.
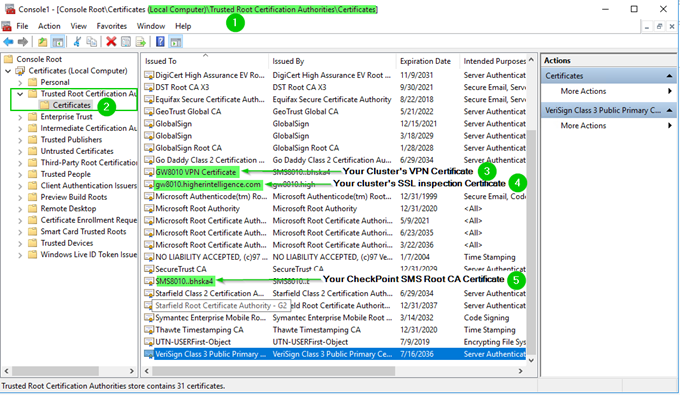
Cheers,
Vladimir
11 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You have to configure the certificate used for Usercheck.
See my comment here:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Agreed to the thread shared.
I also did generate the certificate through openssl, with DN name to match the IP address; as with cluster hostname it was giving me prompt that you'll face ssl error.
In the end it still doesn't work with the imported certificate for usercheck.
My obervations:-
- When trying to access a blocked https://website_A, Connection is insecure / private message appears and when selected to proceed Block page appears. Certificate is the one i created through open ssl and imported in Cluster
- Also at every other blocked https://website_x, connection is not secure appears before proceeding manual to block page
I tried this before, will give it another shot.
Also would you recommend using SHA256 certificates; and Cluster performance cautions i should take?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If the CA that signed that certificate isn't trusted by the browser, you'll still get the error.
That's the issue you need to fix ![]()
There's nothing wrong with using SHA256--no specific precautions are required that I am aware of.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm generating 2 certificate's through openssl (SHA256), one for HTTPS Inspection and other for Usercheck block page.
HTTPS inspection works fine but the Usercheck Block page doesn't work as expected.
As said earlier, My obervations:-
- When trying to access a blocked https://website_A, Connection is insecure / private message appears and when selected to proceed Block page appears. Certificate shown on Block page is the one i created through open ssl for Usercheck Block Page
- Then at every other blocked https://website_x, connection is not secure appears before proceeding manual to block page
"If the CA that signed that certificate isn't trusted by the browser, you'll still get the error.
That's the issue you need to fix "
Have made both certificates CA as "Trusted Root Certification Authorities". Still getting ssl error for Usercheck Block Page ![]()
I did all this before, will give it another shot.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How did you generate the certificate for UserCheck with OpenSSL?
- If you generated it as a self-signed certificate (which is what I suspect), then the browser must be configured to accept this self-signed certificate as valid. You follow the same steps you followed to get your organization to trust the HTTPS Inspection certificate. You can validate this on your own PC by clicking on the "Install Certificate" button as shown in your screenshot.
- If you signed the certificate with a certificate authority the browser already trusts, then no configuration should be required.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please check if the UserCheck URL is changed to https. By default, it is http:

Additionally, make sure that once the https is enabled, the Root CA issuing the certificate is added to your clients' Trusted Root CAs IN ADDITION to the actual certificate for that of the UserCheck portal.
Otherwise, validation of the Issuing CA's certificate will fail.
You may find this of interest or help:
…possible reason you are keep getting the “untrusted” messages in the browsers is due to your CheckPoint Management Server’s certificate not being included in the Trusted Root CAs.
"This portal using an auto-generated certificate. You can import your own certificate" is actually referring to the VPN cert.
When browser sees the VPN cert, it is trying to verify who has issued it and if it can trust the issuer.
The VPN cert is issued not by the gateway, but by the Management Server.
For you not to see warnings for UserCheck and VPN, three certificates must be installed in each computer’s Trusted Root CAs:
- SSL/HTTPS Inspection certificate
- Cluster’s VPN certificate
- Management Server’s Root CA certificate
See the screenshots below:
- Working VPN Cert:

2. Exporting VPN Cert using Chrome

3., 4. Exporting VPN Cert Using Chrome continues


5. Saving VPN Cert

6. Navigating up the Certification path (In “General” tab, we are still looking at the VPN Certificate, but in Certification Path, we are moving to the Root)

7., 8. Root CA Certification export continues


9., 10. Root CA Certification export continues


11. Saving CheckPoint Management Root CA

12. All three certificates must be present in Trusted Root CAs on every computer to avoid certificate warnings with UserCheck and VPN.

Cheers,
Vladimir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Vladimir Yakovlev & Dameon Welch Abernathy.
Such detailed explanation, it becomes really helpful to everyone.
The certificate issued by the Management to the Gateway (Server Certificate) also contains IP address as a Alternate Subject Name.
I was able to drill down the issue with our Customer regarding this.
Customer changed the Gateway Cluster Object's IP address which changed the Platform & Usercheck Portal's Main URL.
Browser's opened Block Page on the new URL and the certificate didn't match the URL w.r.t. Alternate Subject Name.
Hence the error ERR_CERT_COMMON_NAME_INVALID (Chrome)
We can renew the certificate and update other interface IP also (if required)

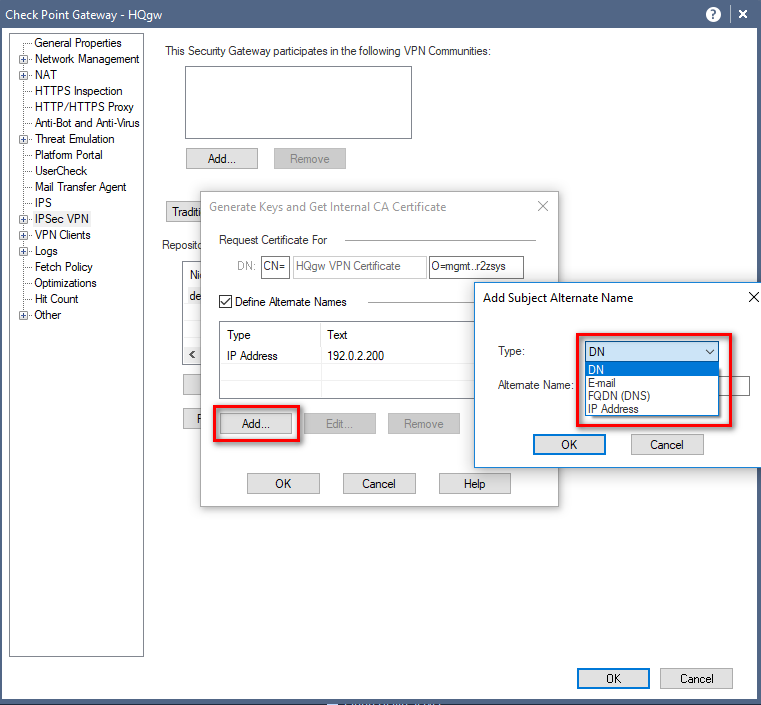
Once certificate was renewed and published to user's, No error prompt in browser's faced by user's.
Note:- When creating a Certificate from Organizational Internal CA then also it important to mention the Subject Alternate Name.
Sorry for such late reply ![]()
Additional Reference :- UserCheck redirects to HTTPS even when UserCheck Portal is configured as HTTP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Speaking of late replies:)
Just run into this thread with similar situation: UserCheck portal has different IP address from main portal. Thanks to your reply I was able to re-issue the cert with second IP in SAN to solve the issue.
Cheers,
Vladimir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello
I have the question, maybe you can help me
My client deploys the Captive Portal for PCs external to those of the organization in a wireless network, there is some way to download and install the certificate automatically when trying to connect to the captive portal?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I was able to do it, but i searched a bit before finding it
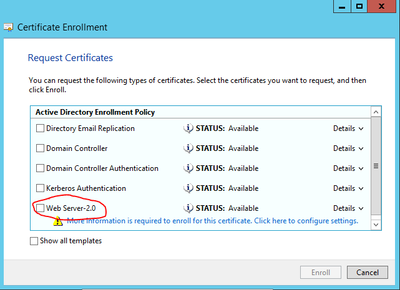
From Windows, certificate authority and generate a dedicated WebServer template.
-> That can be exportable with Private key
-> One that i can change the "Issued To"
-> I've then made a request via MMC -> Local Computer
And it works in a domain environment.
Everybody if is trusting the domain (which is normal by default in Windows domain as it was issued by the domain CA) will work like a charm
Kind regards,
David.D
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Few years later, but anyway, in case anyone is looking for solution:
The short answer, if the users are external to your organization and the certificate is self-signed is a no.
What you are asking is to install an unsanctioned by user untrusted CA.
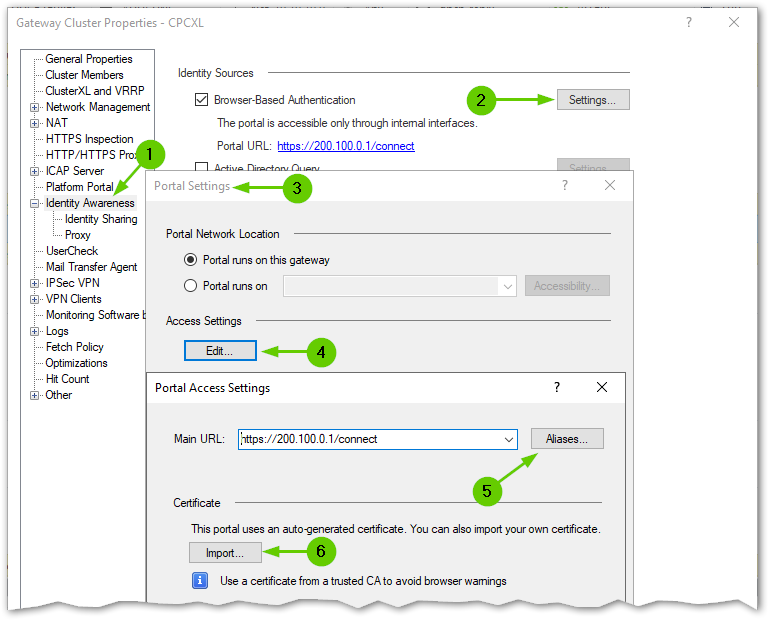
To make this work properly, generate CRL for publicly trusted CA, get the paid certificate and import it in Portal Access Settings for Browser-Based Authentication.
Use this for references on how to create CSR:
How to generate the Wildcard certificate (SAN) CSR for Multi-Portal sk170395
Upcoming Events
Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter