Please check if the UserCheck URL is changed to https. By default, it is http:
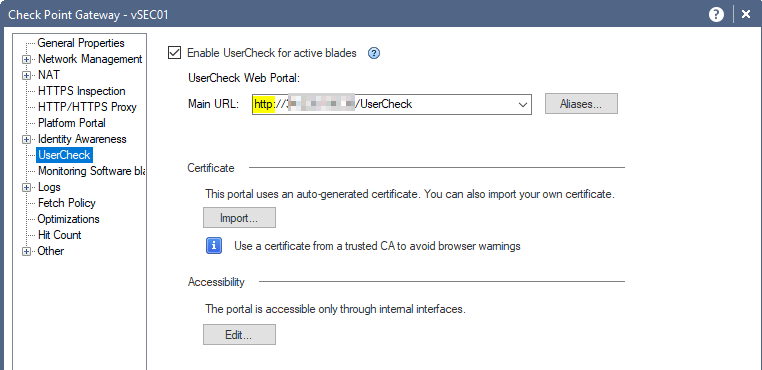
Additionally, make sure that once the https is enabled, the Root CA issuing the certificate is added to your clients' Trusted Root CAs IN ADDITION to the actual certificate for that of the UserCheck portal.
Otherwise, validation of the Issuing CA's certificate will fail.
You may find this of interest or help:
…possible reason you are keep getting the “untrusted” messages in the browsers is due to your CheckPoint Management Server’s certificate not being included in the Trusted Root CAs.
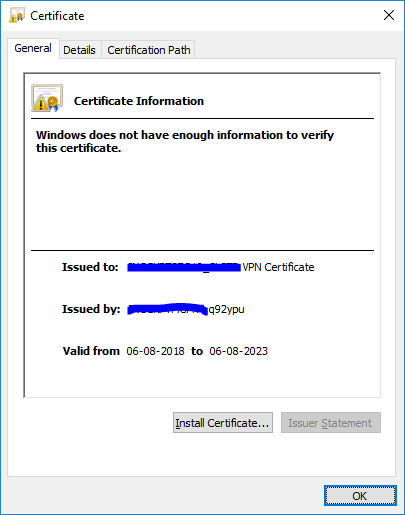
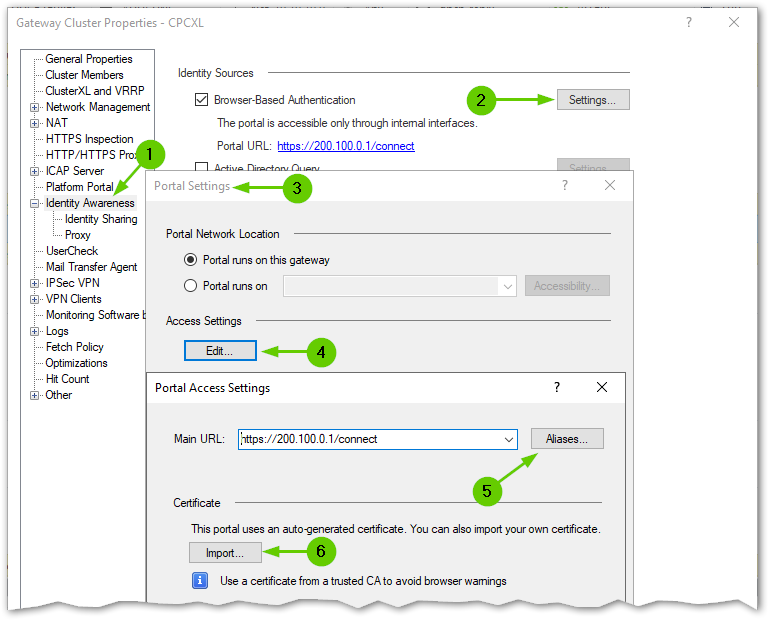
"This portal using an auto-generated certificate. You can import your own certificate" is actually referring to the VPN cert.
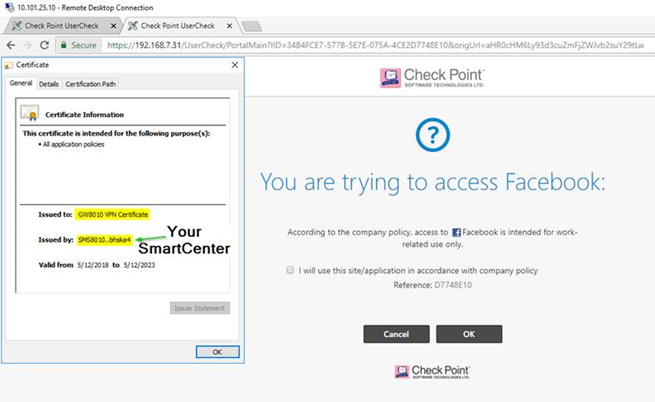
When browser sees the VPN cert, it is trying to verify who has issued it and if it can trust the issuer.
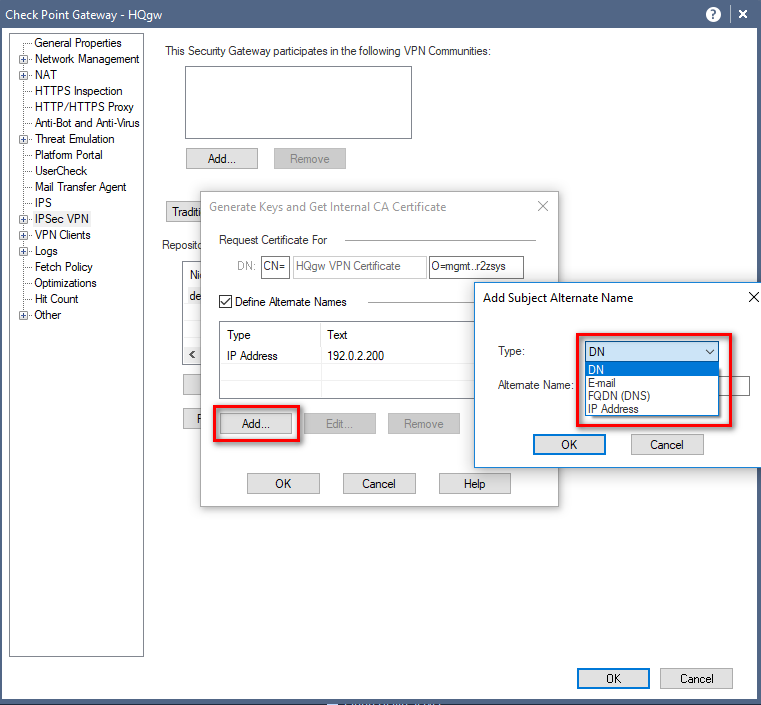
The VPN cert is issued not by the gateway, but by the Management Server.
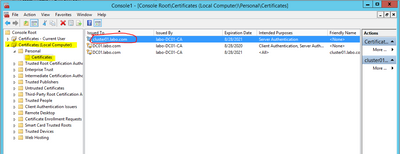
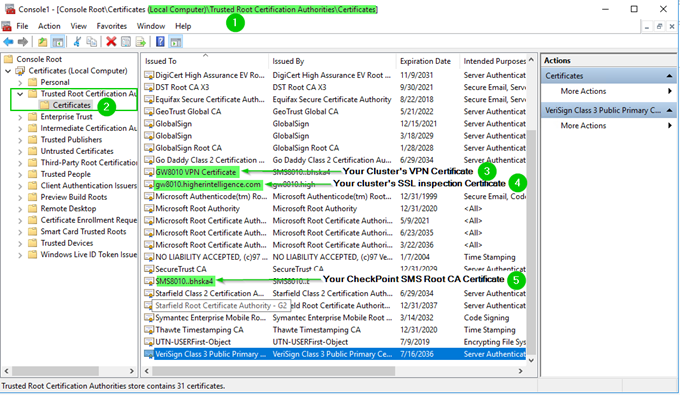
For you not to see warnings for UserCheck and VPN, three certificates must be installed in each computer’s Trusted Root CAs:
- SSL/HTTPS Inspection certificate
- Cluster’s VPN certificate
- Management Server’s Root CA certificate
See the screenshots below:
- Working VPN Cert:
2. Exporting VPN Cert using Chrome
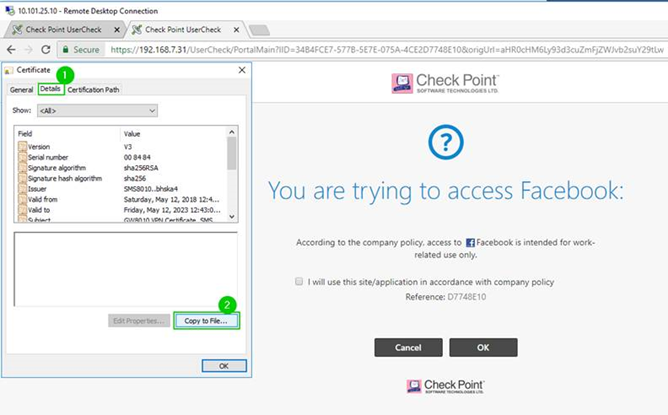
3., 4. Exporting VPN Cert Using Chrome continues
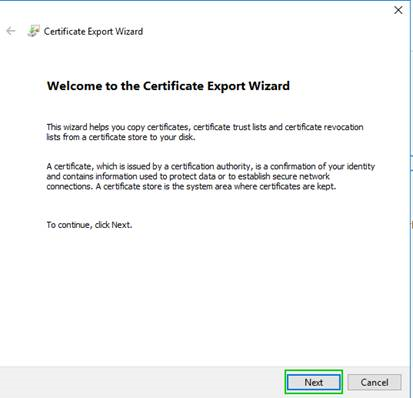
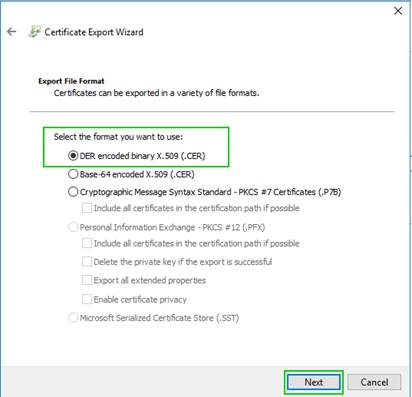
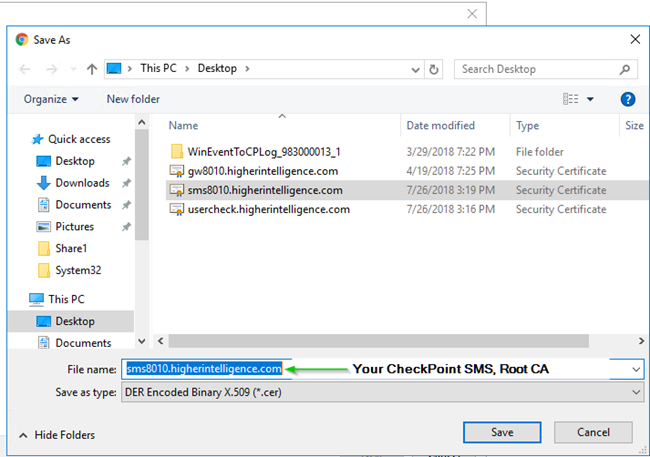
5. Saving VPN Cert
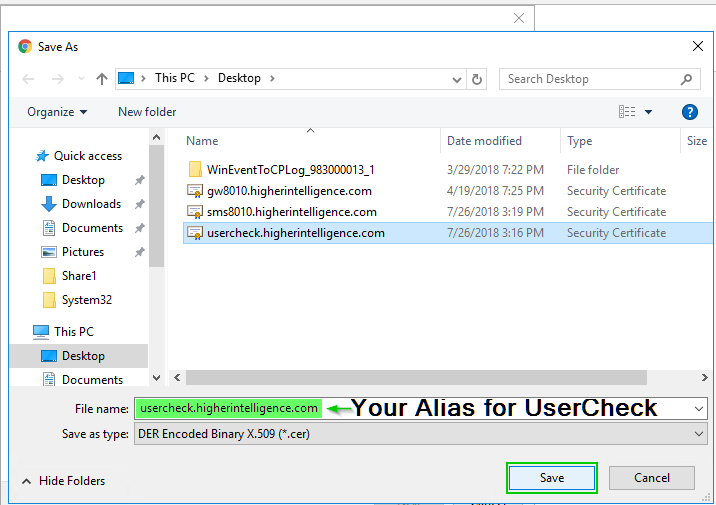
6. Navigating up the Certification path (In “General” tab, we are still looking at the VPN Certificate, but in Certification Path, we are moving to the Root)
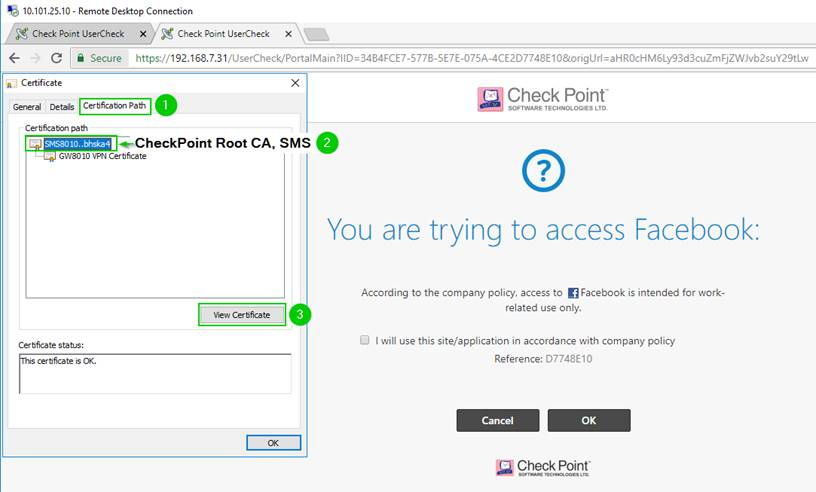
7., 8. Root CA Certification export continues
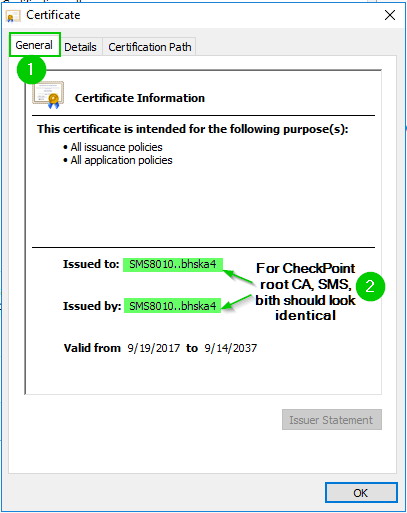
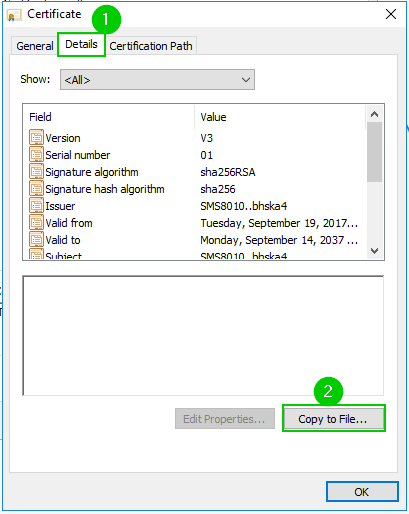
9., 10. Root CA Certification export continues
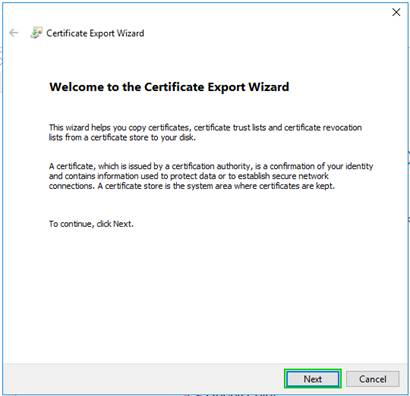
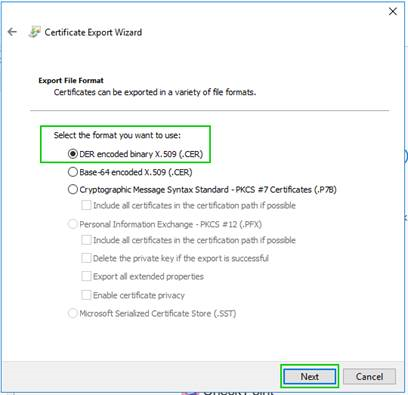
11. Saving CheckPoint Management Root CA
12. All three certificates must be present in Trusted Root CAs on every computer to avoid certificate warnings with UserCheck and VPN.
Cheers,
Vladimir