- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Threat Prevention
- :
- Re: TechTalk: Advanced Threat Prevention Best Prac...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
TechTalk: Advanced Threat Prevention Best Practices
Keeping threats from impacting your organization doesn’t have to be challenging! Join Threat Prevention Expert Nick McKerral to learn how to implement Threat Prevention Best Practices using Check Point Infinity:
- Learn how to activate the IPS, AB, AV blades in R80.10
- Learn how to activate and utilize Threat Emulation and Extraction to protect web and email
- Learn all about Check Point’s new inline threat extraction capabilities
- Learn about Sandblast Agent with browser based Threat Emulation, Extraction, Anti-phishing, domain credential protection capabilities, and more!
Watch the recording: Video Link : 5863
Answers to questions we did not get to during the session will be summarized and answered below.
- Tags:
- techtalk
7 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey Everyone,
Thanks for attending today and sorry we didn't get a chance to get to your questions. There were a lot! I'm going to try and address them all here but I might need to take a few days to get to all of them. Here we go!
- In Staging mode .. does it impact the CPU utilization more then the Prevention mode? - No, the signatures in staging mode are the same, they just have their action overridden to be detect only. It's important to make sure any new IPS signatures introduced in your environment are not going to cause a disruption before they're placed in a prevention state. That being said, not all signatures need to be in prevent, sometimes it's better to just be aware of the alert rather than block it outright. In addition, you may have signatures that don't match any hosts/services/processes in your network. Maybe they don't need to be activated, potentially freeing up resources for other things.
- I like to know general question. does the traffic flow from access control policy, then jump to threat prevention layer? if so which blade will get first check. IPS then AV then AB etc? - I like this question, it comes up a lot. The short answer is we inspect a lot of the content in parallel using different inspection contexts, however one signature match may trigger before the other, completely dependant on how many packets in the session that have streamed into the gateway, and whether it's enough to make a decision. For example AB could trigger before App Control if we're matching a known malicious IP, whereas IPS could trigger before DLP depending on if we have enough of the session to match a known IPS signature. I'm overly simplifying here, but we have tons of material that goes into a deeper explanation. Here's some reading on how packets flow through Check Point: Check Point Security Gateway Architecture and Packet Flow ,Infinity NGTP architecture , Check Point Threat Prevention Packet Flow and Architecture
- Where do we modify aggressive aging and other options here? - Aggressive again has moved to a new section called "Inspection Settings" which is part of our Shared Policies menu. In Shared Policies you'll find the setting for Geo Policy, HTTPS Inspection and Inspection Settings.
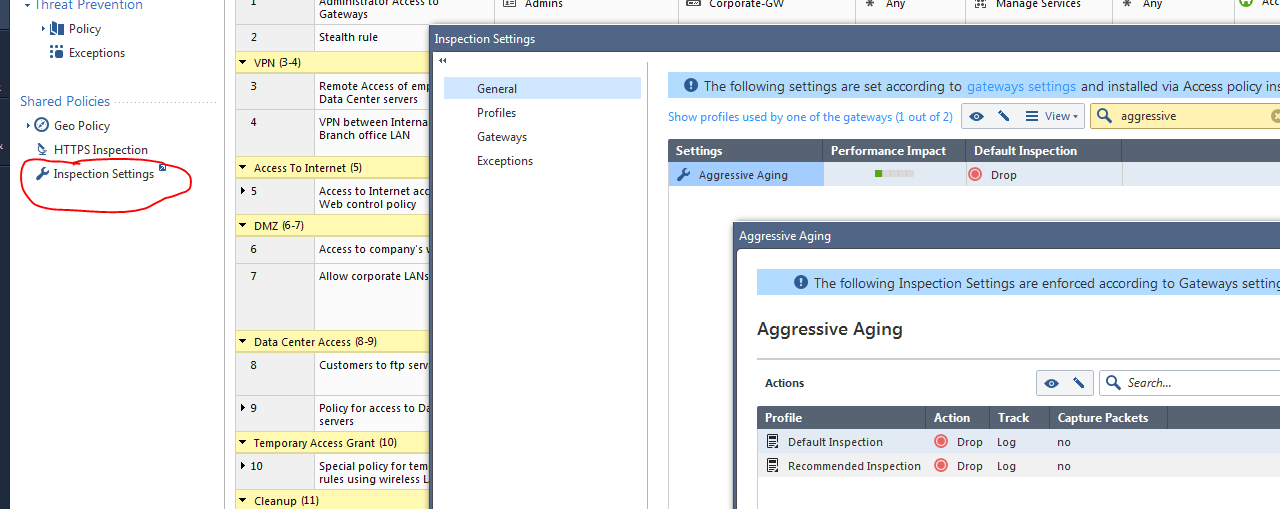
- Now i realised that some of the IPS protections in R77.30 are not in R80.10. As security engineers how can we make sure that these protections are configured correctly? - We still have our two IPS pre-made profiles, Default Inspection and Recommended Inspection. Default inspection has fewer IPS signatures activated, and most signatures are in detect mode and not prevent. Recommended has more signatures activated and much more moved into prevention. Look at the services that you're protecting first, then going off one of our default profiles (I recommend starting with the recommended profile) add in additional vendors, services, protections as necessary. Keep in mind that IPS no longer needs to be all or nothing. You can activate protections at the zone, subnet, host, user, group, src, dst, etc. level now, which means you can get much more aggressive in what you activate and how you tune your IPS. My recommendation to get started: turn on recommended, override the defaults to detect only, baseline the environment for false positives, and build up exclusion lists, and then switch to protect mode. Adding signatures as required. Then make sure you regularly check your staging signature and logs and get staged signatures moved to production so that your protection capabilities don't fall behind. IPS requires a lot of care and feeding if you want it to provide you with the best protection and least disruption. If you don't think you have the cycles to manage it, I would look into leveraging a managed service to have someone keep on top of it.
- Which vendor(s) are supplying the underlying a/v engine? - I've been told we get our AV intelligence from a few different engines, those sources also rotate in and out depending on whether we see them providing enough protection value. Our Threatcloud has intelligence that comes from internal check point resources, external threat feeds, industry partnerships, all sorts of places. On the gateway, if you enable "deep packet inspection" in your AV profile, which is not enabled by default, then there is a OEM version of the Kaspersky AV engine available for on premise scanning. As long as you have a connection to Threat Cloud, you can choose to use this engine in conjunction with all our other indicator sources.
- Does TE still scan SMTP if you don’t have the Gateway configured as an MTA? - Yes it does! Unfortunately I didn't have the time to get into email during the presentation, there was a lot to cover. However TE can scan SMTP traffic, or you can also setup a MTA to inspect mail traffic as well. Scanning SMTP alone requires the traffic to be unencrypted, and we can't apply our threat extraction technology to a SMTP stream, so for true threat prevention, we would normally recommend using the MTA configuration. However a easy option to get *some* visibility into mail based threats would be to turn on SMTP scanning in the TE policy and see what you can see.
- Could we get more information on UserCheck? What exactly does it do? What does it require? -
Use Check Point UserCheck to actively engage and educate users as they access the web to identity potential policy incidents as they occur and remediate them immediately. Users are an integral part of the web security and control process. The best practice is to engage and educate users as they use the web to identity potential policy incidents as they occur and remediate them immediately. Check Point UserCheck, a feature of many of our different inspection modules, enables an organization to implement two way communication between IT and the users, saving valuable IT administration time while improving user productivity and overall security. Usercheck is a core component that's included in Check Point R80. You can learn more about it in the Next Gen Security gateway guide for R80.10. Located here: Next Generation Security Gateway R80.10 (Part of Check Point Infinity)
- How about traffic hidden behind https ? - This is an important question. I would say these days most traffic is hidden behind HTTPS, therefore if you aren't performing some kind of HTTPS inspection, you're missing a lot of the threats that are coming into your environment. There are a couple ways to attack that challenge. First, you could enable HTTPS inspection on your Check Point gateways. This is a component of your shared policies in R80, or of the HTTPS inspection policy in R77.30. If enabling HTTPS inspection isn't possible in your environment, then I would look at prioritising your endpoint security posture by installing a solution like Sandblast Agent, or Sandblast Mobile. These solutions provided browser and host based protection that can inspect threats even if the traffic is encrypted. In a perfect world, I would focus on deploying both HTTPS inspection and endpoint protection, keeping threats as far from the user as possible. As our industry grows and we adopt new technology like TLS 1.3 and applications that utilize pinned certificates, it may become more difficult to intercept and inspect encrypted traffic, making your endpoint protection an even more critical component of your overall network security architecture.
That's all I have time to answer today, I think I got to 1/4 of the questions. I will post the rest of the questions along with my response in this thread over the next few days.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Next set of questions:
9. We currently have automatic email alerts setup to alert us whenever a critical alert is generated by threat emulation. The email always states that threat emulation detected a malicious file, even when the file is prevented. How can we fix this so that the email alert shows the file was prevented? - I would suggest opening a ticket with Check Point TAC; However, if I had to guess I think you're running into the issue described in SK 115252 Threat Emulation logs show "Detect" for e-mail attachments instead of "Prevent" when Threat Extracti... The recommended fix to this solution is to upgrade to R80.10
10. Is there any default protections that should be turned-on in Prevent mode - My personal opinion, is that nothing should be turned on in prevent mode until it's been validated that it's not going to cause a disruption in the environment. This means that if you aren't currently running AV, AB, IPS, TE, TX, your first step should be activating those blades in detection first. Validate through your logs that they're not falsely flagging any business or mission critical processes, and then switch the protection over from detect to prevent. After that, I would use AV, AB, and TE in prevent, and I would continue tuning my IPS to a combination of prevent and detect signatures, based on confidence and based on what your logs are telling you.
11. How does the growth of SSL affect the ability to run threat? - If you're not inspecting encrypted traffic then you're missing threats in your environment. You can use Check Point HTTPS inspection (or MTA mode for mail), or you can use a third party SSL/TLS interception device, like a A10 or F5 (usually advantageous if you have more then one device/appliance/service that requires visibility into encrypted traffic). One way to get around needing to inspect encrypted traffic on the wire, would be to run something like Sandblast Agent on your endpoints, which will intercept files downloaded via the web and send the files for emulation.
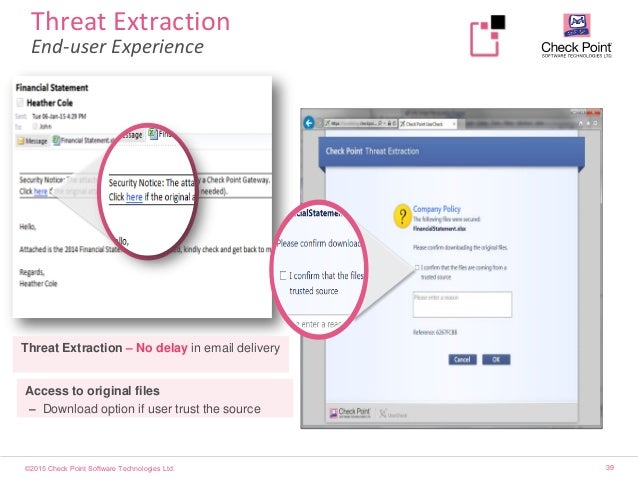
12. how does threat extraction used for attachment in email and does it emulated the file in linux enviroment or not?) - If you have MTA mode enabled on either you Check Point gateway or on a Sandblast Appliance, then we can perform Threat Extraction on email. We will swap the original attachment with a cleaned version of the attachment, and include a header on the email indicating that the file was cleaned by Check Point and that the original file (if benign) is available by clicking an embedded hyperlink in the email. It looks like this:
13. Hi - where i can get an real-world indicator file? - Indicator files are something that you need to create, you can find the instructions on how to make them in the Threat Prevention Admin guide. Threat Prevention R80.10 Administration Guide
14. What is the privacy impact for those files sent to cloud sandbox ,especially in some environments that has HIPPA and PCI compliance ? - Check Point doesn't store any files in our cloud sandbox, all we store are the hashes and the verdicts, when files are transmitted to our cloud they're done over an encrypted connection between the gw (or client if SBA) and our cloud, then the file is detonated in a virtual environment and after detonation the file and the environment are destroyed. Check Point can provide you with a cloud security document as well that goes into more detail around how we handle and treat files in the cloud. With that being said, if privacy is an issue preventing you from using the service, we also have a range of appliances that can provide the same functionality on premise instead of using the cloud service. https://www.checkpoint.com/downloads/product-related/ds-sandblast-appliances.pdf
15. If you have Threat Prevention running as per the demo, are you able to exclude (certain) VPN Community traffic from being checked? - Yes, you define what is being inspected in your protected scope, you can exclude traffic coming from sources you don't want to inspect (like VPN).
16. What is the scope of collaboration between threat emulation on a GW level and on the Endpoint level ? - If files are being inspected in the same location (for example both in the cloud, or both on a Sandblast Appliance) then they will have a common set of threat indicators and it will speed up the verdict of files seen by both the GW's and the clients. You can also send the logs from both to the same location to provide you with a centralized view of all your threat events.
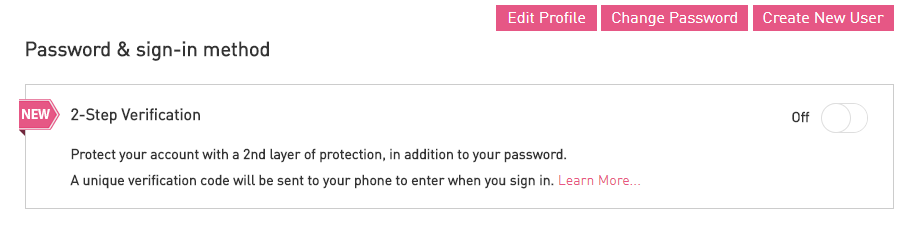
17. 2fa for usercenter ;p? - Log into usercenter, click on "My Profile", and enable it on your account.
18. Threat Emulation - when you check mark in Hold mode, is it impact performance? - There isn't an impact to the Gateway or Sandblast appliance, but there will be an impact to the user. They won't have access to the file until it has completed emulation.
19. I saw there were SBA views/reports in the demo Smart Event environment. We have SBA, but I don’t see those views in my Smart Event. Is there something else I need to add/ enable to see them? We've created some new views/reports for SBA. You can download the templates from this SK article: How to support SandBlast Agent in R80.10 SmartEvent
20. Not sure if this was seen in the field much, but we had to change the policy often to warn the user but allow them to go through to the site as some sites were falsely detected as phishing. Is there a way to advise of false positives or is it just the "send a report and continue" - I would click the "send a report link", or open a ticket.
21. What performance impact does threat emulation has on SecureXL - Traffic that matches any SecureXL templates will still be accelerated, but HTTP traffic (which is what you'll be inspecting with threat emulation) will not be accelerated since it needs to go through Active Streaming (CPAS). ATRG: SecureXL
22. What happen if we have SAML authentication and same password used at different login ? If they're typing their password in on a site that requires it, you can just add the site to your list of protected domains in Zero Phishing configuration.
23. what about the indicator-file and facebook.com? - I just created that as an example, you can put a variety of indicators in the indicator file (domains, IP's, hash values, etc.) When a user attempts to access a resource that matches an indicator you can prevent or detect and log the incident.
24. If I enable url filtering and block the category, It should be blocking the webpage in the first place. any other benefit of using sandblast? - URL filtering is great at blocking known threats, Sandblast is there to block the unknown, the stuff that hasn't been seen before.
25. Do you have any information regarding monitoring the performance of the cloud emulation pods? - At the moment we don't have a way for customers to monitor the emulation pods, this is something that Check Point monitors internally. If you are using Sandblast Appliances, you can monitor their performance of the appliance with SmartView monitor, CPVIEW, and the tecli command.
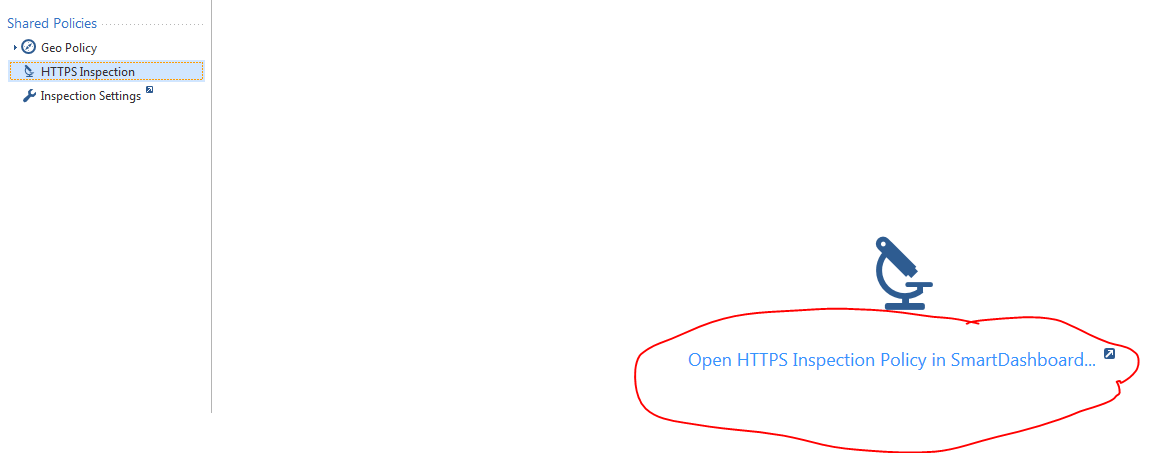
26. When HTTPS inspection policy console will included in the R80.10 SMS?? - It's been included since R80.0. You can access the HTTPS inspection policy under the shared policies section in the security policies tab.
27. and sorry, when the Endpoint console will included too - Endpoint is included now, however it doesn't support Sandblast Agent yet. The current plan is to unify Endpoint management and R80 in the next release (R80.20).
28. is it possible to use threat prevention on a system that only has an active IPS subscription or is an addition subscription reqd? - You require a NGTX subscription to use Threat Emulation/Threat Extraction.
29. can you state if scanning the body of emails work and if there are any recommendations on this - I assume you're asking about scanning the body of emails for malicious links? We can scan the body of emails for links to malicious files now. I would recommend also enabling AV, AB, IPS protections which should detect and prevent any attacks that may result of a user clicking a link and getting directed to a malicious site. Sandblast won't scan or test the website itself (for phishing or browser exploits), it only looks at file. which is why you need to activate all the protections to provide you with complete security.
30. what’s is the expected performance hit if we enable ALL IPS settings? 20% 50%, is there a hardware limitation that impacts this the most? cpu, memory? - There are a lot of factors here that can make an impact on performance. The best way to determine the expected performance hit for your environment and your appliances is to use the Performance Sizing Utility. The Check Point Performance Sizing Utility
Thanks again everyone for attending and thanks for all your questions!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,![]()
This Q & A, really helps, this is the way, we can improve and excel community knowledge towards to the particular product and its relevant version. Keep it up and do share more so overall efforts we can reduce and attract more people towards this, also, what are the best practices and what we can do as per the current scenario all can implement accordingly. Thanks Again. ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Unfortunately it seems that not all the questions were answered 😕
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Some of the questions were duplicates for sure and/or answered privately.
If there's a particular one we missed, let us know.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sure, my question was:
We have a customer with SBA, who wants to use the plugin also.
Unfortunately, it doesn't work properly and all of the users get error messages when downloading files.
So we wanted to deactivate it via GPO until the tests are finished, but it seems not to be possible - SBA Plugin completely ignores the GPO setting - which is a huge drawback in an enterprise deployment and maybe should be addressed.
It seems that the only way to disable it, is to edit the EPS MGMT Server via GUIdbedit (ep_orgp_te_policy_tbl -> browser_extensions_enabled).
After we did this, it's now disabled for everyone.
Is it possible to enable the plugin only for a group of users, until all the tests are finished and ready to be deployed to all users, without having to deinstall the plugin for 1k users, in order to leave it for the 5 that need to test?
Thanks & BR
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Amir,
Sorry that your question got missed. If you want to disable web download protection you can disable it in the the Sandblast Agent Threat Extraction and Emulation policy in SmartEndpoint. Your policy probably looks something like this:

If you change protect web downloads with Threat Extraction and Emulation to "Do not use Web download protection" it will disable that functionality in the browser plugin. (Note: for the policy to take effect you will need to relaunch the browser, I've noticed in some cases Chrome is setup to run in the taskbar, so simply closing the browser may not be enough, you may also need to restart the taskbar process as well.
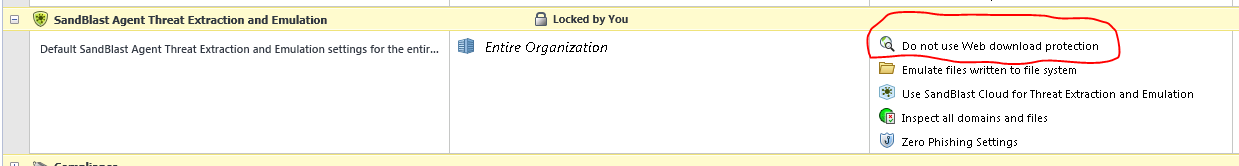
So this will disable the web download protection for all users (it doesn't disable the plugin though so Zero Phishing and Domain credential protection should still work).
Next you'll want to create a test group where the browser plugin is enabled. I would create a new Virtual Group called SBA Test users.
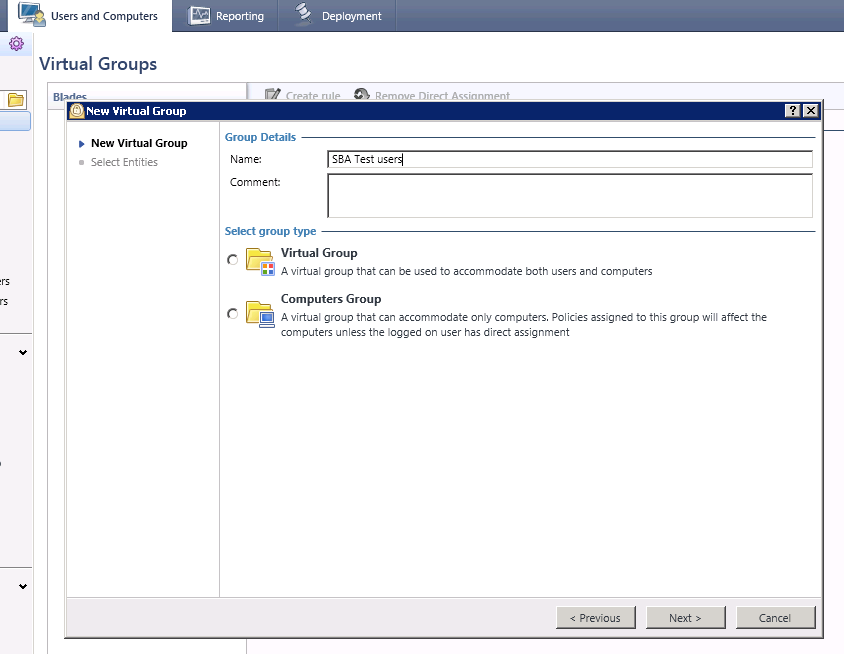
Add in the users you want to participate in the test group.
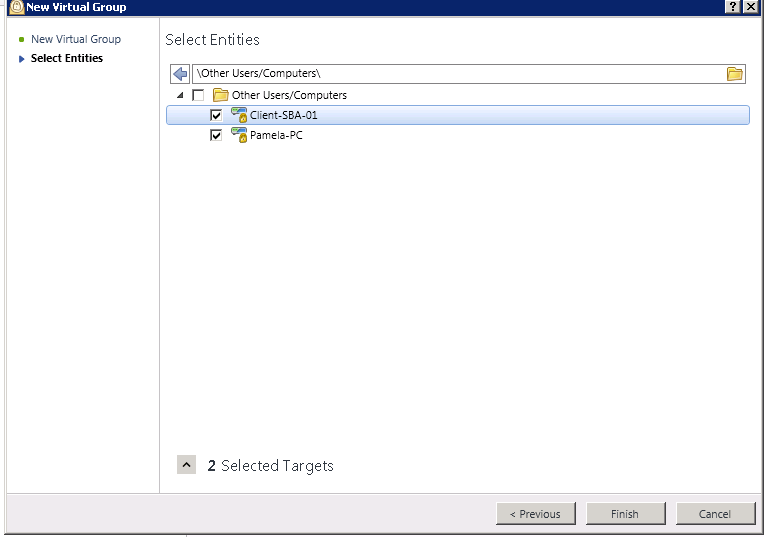
Then create a new Sandblast Agent Policy for those users
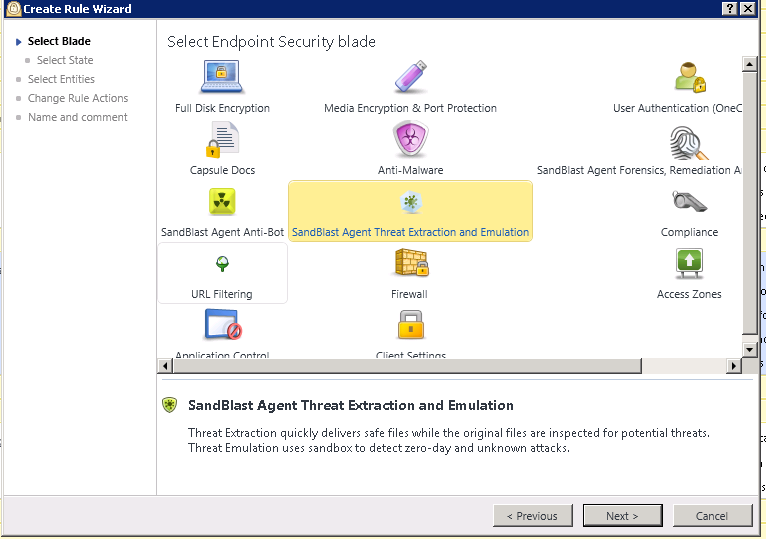
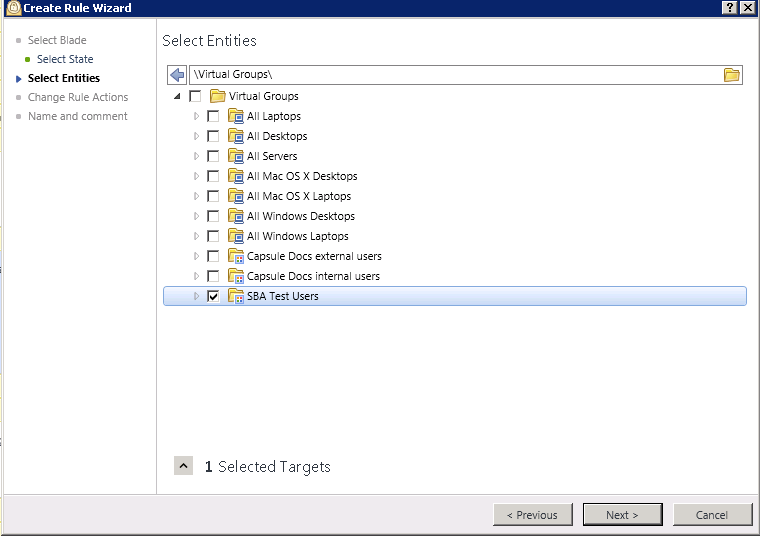
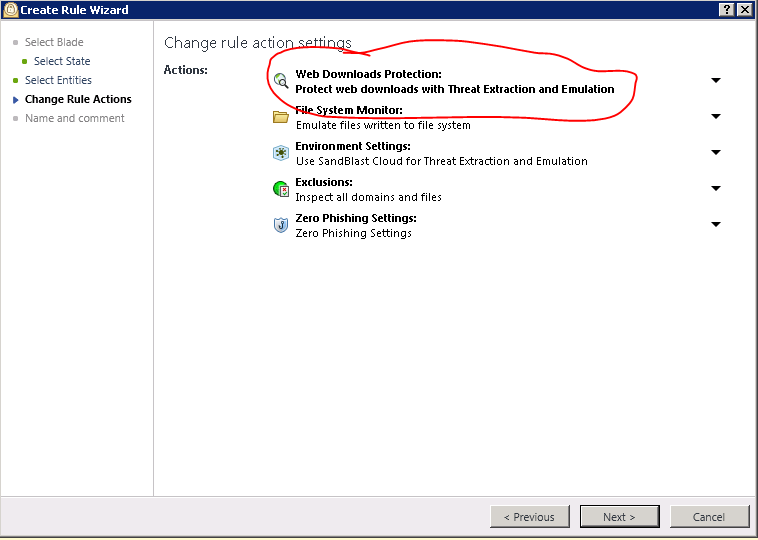
Make sure you enable web downloads protection in their policy
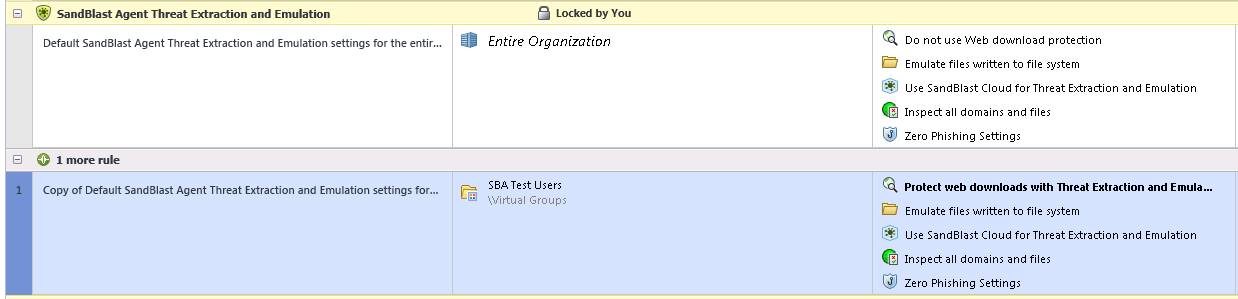
Now your policy should look like this, for everyone in the organization you won't be using the web download protection and for the users in the SBA Test users virtual group web download protection will be enabled.
Hope this helps. If you still run into issue with web downloads not working properly, please make sure you open a ticket with TAC so they can troubleshoot the issue with you.
-Nick
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


