- CheckMates
- :
- Products
- :
- Quantum
- :
- Threat Prevention
- :
- Re: R80.40 Threat Prevention IPS Protected Scope o...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R80.40 Threat Prevention IPS Protected Scope or Source / Destination
Hi
I am trying to create a threat prevention policy where traffic from
(DMZ -> Inside networks) and (Inside networks -> DMZ) ----- IPS Profile in Detect mode
(DMZ+Inside -> Internet) and (Internet -> DMZ+Inside) ----- Same IPS Profile in Prevent mode
I can do that using hidden columns of source and destination in Threat Prevention Policy and also creating objects for inside, DMZ and internet (Negated cell of inside networks)
and by also cloning the existing IPS profile and changing all actions to detect mode
but isnt there a better and cleaner way of doing this using scopes and not having to use Source, Destination columns, and also avoid cloning or duplication of Current IPS profile
Thanks
Kind Regards
- Labels:
-
IPS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Wolfgang for screenshot, but you have done this as Exception? (Is it because of detect action?)
instead of a rule
Internal Zone is a zone object?
Thanks
Kind Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
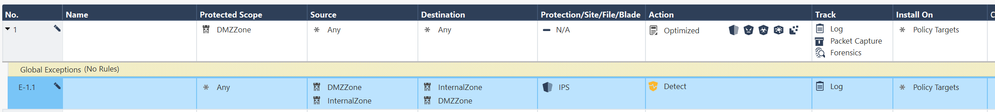
Rule 1 has DMZzone as protected scope, this means all connection to and from DMZzone are protected with the optimised TP-profile with all enabled blades (IPS, AVIR, ABOT, TE, TP).
Rule E-1.1 is an exception of rule 1. For all connections between DMZzone and INTERNALzone and vice versa the IPS blade works only in detect mode.
There is no need to create a new profile with all IPS protections set to detect. Yes, DMZzone and INTERNALzone are zone objects. But this is shown only as an example. You can replace them with your network or group objects to fit your needs.
To secure all connections you can set the protected scope in rule 1 to any or you can set to DMZzone and INTERNALzone to match your described configuration accurately.
Wolfgang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Usually, an IPS Profile in Detect mode is only used in the first IPS deployment phase - as the load on the GW will be the same if detect or prevent is on, Detect makes not much sense in production, taking ressources but doing logs only. Cleanest way is to group the DMZ and internal networks and use them in a rule as you wrote above. Cloning of the IPS policy is needed, too.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you G_W_Albrecht, Yes business has been in detect mode for a week now but they cannot afford to loose even a pico second of drops and want to be very cautious