- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Quantum (Secure the Network)
- CloudGuard CloudMates
- Harmony (Secure Users and Access)
- Infinity Core Services (Collaborative Security Operations & Services)
- Developers
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Infinity Portal
- Products Announcements
- Threat Prevention Blog
- CheckMates for Startups
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
May the 4th (+4)
Roadmap Session and Use Cases for
Cloud Security, SASE, and Email Security
SASE Masters:
Deploying Harmony SASE for a 6,000-Strong Workforce
in a Single Weekend
Paradigm Shifts: Adventures Unleashed!
Capture Your Adventure for a Chance to WIN!
Mastering Compliance
Unveiling the power of Compliance Blade
CPX 2024 Content
is Here!
Harmony SaaS
The most advanced prevention
for SaaS-based threats
CheckMates Go:
CPX 2024 Recap
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Threat Prevention
- :
- Re: IPS isn't work.
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
IPS isn't work.
Hello community!
Looks like my IPS isn't work.
I have a cluster on border of my network with internet.
I enable https inspection and IPS blade, update IPS signatures database and try to test with checkme.
So, IPS information from security gateways:
[Expert@FW1_name:0]# ips stat
IPS Status: Enabled
Active Profiles:
Optimized
IPS Update Version: 635241547
Global Detect: Off
Bypass Under Load: Off
[Expert@FW2_name:0]# ips stat
IPS Status: Enabled
IPS Update Version: 635241547
Global Detect: Off
Bypass Under Load: Off
Honestly i don't know why FW2 have not Active Profiles but ok, i have two checkme tests and both tests was fully Vulnerable...
Regarding sk115236 i expect as minimum that Browser exploit section will be secure. Because my Active IPS profile include signature Cross-Site Scripting Scanning Attempt in "Prevent mode".
One more interesting thing that in sk115236 for Malware Infection test recommended enabling "D-Link 850L Router Remote Unauthenticated Information Disclosure" signature. But i didn't find this signature in list at all...
At the moment, I have familiarized myself with a huge number of problems related to IPS database updates, checkme checks, etc., but I have not been able to figure it out.
I'll add additional screenshots for help analyze situation.
Gaia version is R80.40 on management server and FWs
18 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R80.40 is out of any support next April - better contact CP TAC !
CCSE CCTE CCSM SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
From the output it seems the Optimized profile is active.
What does your HTTPS inspection policy look like, importantly which direction was it enabled for?
From demo console the protection is there:
https://advisories.checkpoint.com/defense/advisories/public/2017/cpai-2017-0850.html/
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Wrong way around you made the internet now more safe 😄
HTTPS inspec rule:
Source: Internet Dest Server: HTTPS inspect. This is good
-------
If you like this post please give a thumbs up(kudo)! 🙂
If you like this post please give a thumbs up(kudo)! 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Im not 100% clear on what exactly the issue here is...forgive me if this sounds like a dumb question, but are you saying that specific IPS protections are not working properly? Seems like inspection is taking place.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think yes, because:
1) IPS blade is active
2) Databases updated (But i don't know why signature "D-Link 850L Router Remote Unauthenticated Information Disclosure" doesn't exist in IPS protections list)
3) Signatures (for example Cross-Site Scripting Scanning Attempt in prevent mode)
4) HTTPS inspection works
5) Policy is installed
But all tests displays Vulnerable (Browser exploit also), but if we believe to sk115236 test result should be secure as minimum....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I agree, that sk would be a good test. Let me check those protections in the lab later and will send screenshots of what they show, as Im on latest R81.20.
Best,
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
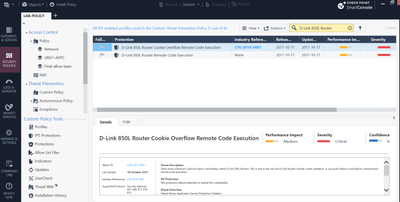
This is what I see in my R81.20 jumbo 45 lab.
Best,
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
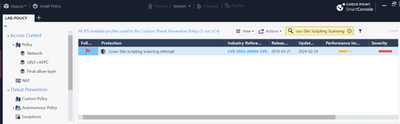
And i have same picture i think. I just can't see action sections on your screenshot.
Interesting that you also don't have signature
D-Link 850L Router Remote Unauthenticated Information Disclosure
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I dont see that one, no. Action for cross-site scripting one you mean?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you asked for cross-site scripting, thats prevent, for sure.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I've reproduced the missing protection in my lab and am currently testing to see if sk179644 is a fix, need to await the next IPS update to confirm.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I actually did the same in one of my labs, lets see.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
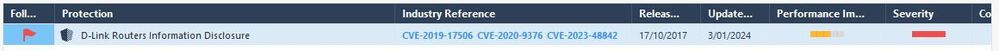
Updated to IPS package version 635241667.
Note the protection appears to have been updated & renamed simply to “D-Link Routers Information Disclosure” hence the issue with trying to find it.
Will request the CheckME documentation be amended accordingly.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To clarify do you see logs for any of the CheckMe communication at all?
The traffic definately traverses the gateway without interception by a VPN / Proxy / SWG other than Check Point?
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Malware infection is not really related to the IPS blade. Is more for Anti-virus / Anti-bot blade.
-------
If you like this post please give a thumbs up(kudo)! 🙂
If you like this post please give a thumbs up(kudo)! 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear Lesley,
Please correct me if I'm wrong. As i know IPS in this case should work first and block download of this Malware before Anti-Virus, because IPS work with traffic flow (doesn't wait while file will buffered like Anti-Virus).
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 3 | |
| 1 | |
| 1 |
Upcoming Events
Thu 02 May 2024 @ 10:00 AM (CEST)
CheckMates Live BeLux: How Can Check Point AI Copilot Assist You?Thu 02 May 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - Keine Kompromisse - Sicheres SD-WANThu 02 May 2024 @ 10:00 AM (CEST)
CheckMates Live BeLux: How Can Check Point AI Copilot Assist You?Thu 02 May 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - Keine Kompromisse - Sicheres SD-WANAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
Facts at a Glance
User Center