- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
CheckMates Fest 2025!
Join the Biggest Event of the Year!
Share your Cyber Security Insights
On-Stage at CPX 2025
Simplifying Zero Trust Security
with Infinity Identity!
Zero Trust Implementation
Help us with the Short-Term Roadmap
CheckMates Go:
What's New in R82
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Threat Prevention
- :
- Re: IPS Bypass
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
IPS Bypass
IPS inspection requires additional CPU and memory resources to handle the incoming packets. If your CPU utilization is under heavy load IPS inspection will be disabled.
From CheckPoint:
Special IPS Bypass mechanism automatically disables all IPS protections (by placing them under exception), when it detects that the certain CPU utilization and memory utilization thresholds have been reached, and restores the IPS protections when the utilization decreases to a safe level.
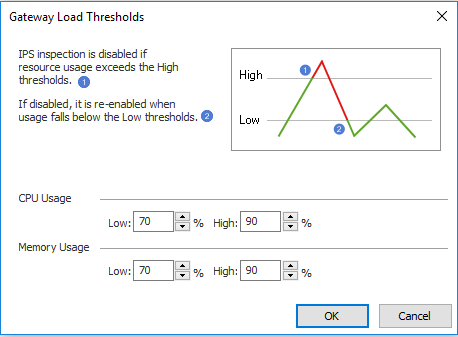
The IPS Bypass mechanism measures spikes on specific CPU core. Meaning, it may be enabled if one of the CPU cores / CoreXL FW Instances that handles IPS, has reached the configured trigger for Bypass. IPS Bypass trigger is measured as a CPU reading above the High threshold and 9 readings above Low threshold. The IPS Bypass feature is enabled if any CPU core is under heavy load (it uses the busiest CPU core - requires continued load for 10 seconds to enter bypass). It is not measured as average of all active CPU cores.
The bypass settings is under gateway properties:
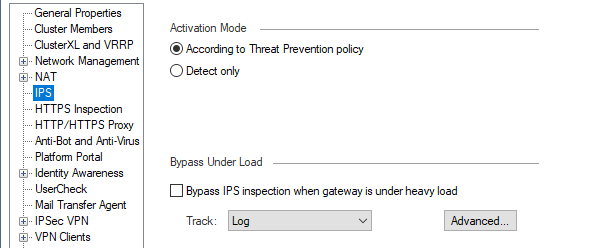
If you have it enabled there will be a checkmark under "Bypass IPS inspection..".
The thresholds can be seen under "Advanced" button.
To check your logs to see if IPS bypass did occur you can open Logs & Monitor and use this filter (choose last 7 days):
blade:IPS NOT(action:(prevent OR block)) OR "IPS Bypass Engaged" OR "IPS Bypass Disengaged"
This is very interesting specially if you have an appliance that have IPS enabled and not powerful enough to handle all the traffic. The above log filter will show when IPS bypass was engaged and then disengaged. By the timestamp you will see the timespan that you were not protected.
From CheckPoint:
Does this mean that when the Security Gateway is stressed absolutely, no IPS code is active?Almost. Meaning, that all the IPS protections are under a global exception.
What would have happened on an appliance that did not have IPS bypass enabled but were under heavy load?
Is "IPS bypass enabled" a way for attackers to successfully run an attack by first making your firewall sweat and then run an attack knowing that your IPS protections will not be enforced during heavy load?
- Tags:
- ddos
- ips bypass
- shodan
7 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
IPS bypass feature is created for customers who value connectivity more that security and cannot afford running full security checks in case of heavy load slowing down their business applications. This is a pure risk management subject and needs to be considered and treated as such.
Now, to your questions:
Q: What would have happened on an appliance that did not have IPS bypass enabled but were under heavy load?
A: FW will run high CPU and may cause some degradation on customer facing application, such as slow responsiveness, re-transmissions, etc.
Q: Is "IPS bypass enabled" a way for attackers to successfully run an attack by first making your firewall sweat and then run an attack knowing that your IPS protections will not be enforced during heavy load?
A: Theoretically yes, but considering dynamic nature of the bypass, a supposed attacker need to have inside information about particular settings and thresholds and even the fact of it being enabled. This makes such an attack tricky and not really practical.
I certainty understand your concern about elevated security risks with this feature enabled. As already mentioned, this is a risk management decision. Some customers might chose availability before security in some particular critical situation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm not sure if IPS bypass feature is enabled by default on 1400-series appliances. IPS enabled on those might have big impact concerning security when IPS bypass is enabled and you have an appliance which is not sized well (it happens). I also believe that not everyone is aware of the trade off between security and availability when IPS bypass is enabled on weaker appliances.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Enis Dunic, this feature is by no means enabled by default. It is part of GW object properties or Threat Prevention Policy and nothing else.
I personally would not define enabling IPS bypass as a "big security impact". IPS protections are about so-called "known bad" and unless you are relying exclusively on IPS for virtual patching of outdated systems, rarely represent the first line of defense.
Also, IPS bypass is not a novelty, it exists from R76 release. The related SK: How to tune the "Bypass under Load" IPS settings was originally created in 2011.
I do agree the point about risk management is important. At Check Point, we encourage our customers to exercise due diligence when creating and maintaining security policies for their need.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yeah that makes sense since it's an object property, then someone must have enabled it. I might have confused you when I use both IPS and IPS bypass enabled in same sentence. What I meant was that just IPS will have sometimes high performance impact on the appliance and then combined with the IPS bypass enabled will lead to "big security impact" for the time that IPS bypass is engaged.
Thanks for good answers. You make a big difference here on this community ![]() (You are everywhere man).
(You are everywhere man).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am happy to help, no problem
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Tuning this is extremely difficult in complex environments, that said letting risk management asses really doesn't apply from my perspective. Taking into account which in the traditional sense is more about server overload; then compromise attacks. With the amount of scanning on the internet today, and how quick it is to find an attack surface from wholesale houses like this is a topic that requires re-work from not only Checkpoint but the industry as a whole.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
IPS Bypass Under Load was unusable on a modern Check Point gateway except maybe a Quantum Spark. As originally designed if any one core went over the CPU threshold, IPS was turned off on all cores which basically means IPS is constantly off in the real world. However in R81.10 Jumbo HFA 110+ and R81.20 Take 26+ (and I assume R82) the calculation is based on the average CPU load of *all* cores instead which must cross the CPU threshold to start a bypass:
PRJ-46941,
TPP-3290
UPDATE: IPS bypass triggers will now be activated based on the average CPU load exceeding the high threshold, as opposed to the previous implementation, where a single CPU load triggered the bypass. The change will result in more effective security measures without unnecessary bypasses.
So it is actually usable now but I still would not recommend it.
Gateway Performance Optimization R81.20 Course
now available at maxpowerfirewalls.com
now available at maxpowerfirewalls.com
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 7 | |
| 4 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Fri 10 Jan 2025 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 32: Infinity External Risk Management (CyberInt)Fri 10 Jan 2025 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 32: Infinity External Risk Management (CyberInt)About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


