- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Access Control and Threat Prevention Best Practices
5 November @ 5pm CET / 11am ET
Ask Check Point Threat Intelligence Anything!
October 28th, 9am ET / 3pm CET
Check Point Named Leader
2025 Gartner® Magic Quadrant™ for Hybrid Mesh Firewall
HTTPS Inspection
Help us to understand your needs better
CheckMates Go:
Spark Management Portal and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Threat Prevention
- :
- Do I need https inspection to truly benefit from I...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Do I need https inspection to truly benefit from IPS?
Hi All,
As the subject states, do I need https inspection enabled to truly benefit from IPS protections? Does IPS perform just as good on traffic that isn't inspected? Any data that proves this one way or another?
While our workstations have https inspection, not all of our servers have inspection enabled. So we just want to make sure IPS is fully doing its job on servers.
Just trying to get some real data and information to educate myself and my team.
Thanks in advance!
Logan
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
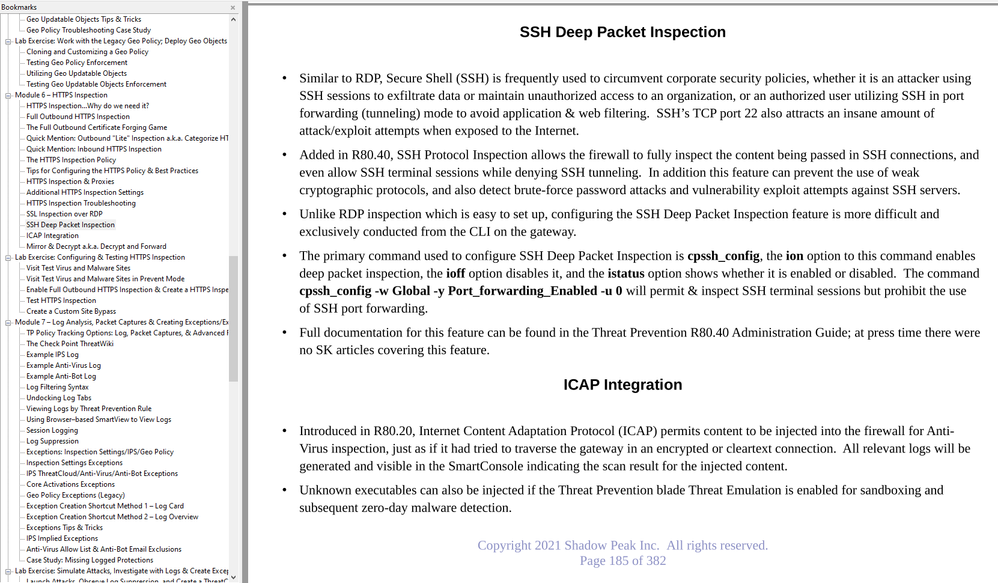
Realistically, yes you do need HTTPS Inspection for proper IPS functioning. Without it IPS will still be able to inspect cleartext payload data, packet headers, and the initial client/server negotiations prior to the start of encryption in the case of HTTPS. Given that around 85-90% of web traffic is now HTTPS you will be missing a lot. This is why HTTPS Inspection was extensively covered in my IPS/AV/ABOT Immersion class even though it is not directly related to those features. Also don't forget about SSH, Check Point firewalls do support SSH Deep Inspection and the cool ability to block port forwarding, but this feature can only be configured from the CLI of the gateway which is why few people know about it.
Performance is definitely a concern, but at least some of that can be mitigated with a properly ordered & configured HTTPS Inspection Policy to avoid multiple HTTPS Policy lookups for the same connection, and avoid unnecessarily triggering Active Streaming when it is not absolutely needed. See here: HTTPS Inspection Policy Rule Order
At some point the Lightspeed/Nvidia card will probably be able to handle at least the HTTPS bulk encryption & decryption aspect, as part of this initiative SecureXL is making the transition out of the kernel (sim) to User Space (UPPAK/usim) starting in R81.20 on Lightspeed systems.
The unofficial way to estimate the performance impact of HTTPS Inspection is to cut the rated throughput of the appliance in half. So if an appliance is rated for 3Gbps with the features you will be using(NGTP,NGTX, etc), to account for HTTPS Inspection cut that number in half to 1.5Gbps.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
22 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No data needed. IPS can't inspect what it can't see. TLS prevents anything between the TLS endpoints from seeing the data exchanged. Therefore, TLS prevents IPS on the firewall from inspecting the data exchanged unless the firewall terminates TLS.
HTTPS Inspection is the feature which lets the firewall terminate TLS.
Protocols which aren't wrapped in TLS can get IPS inspection without HTTPS Inspection enabled. It will catch ping-of-death attempts and so on. That said, most interesting traffic today uses TLS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HTTPS inspection is something only feasible on high-end devices. I've repeated asked what the strategy is to ensure https inspect can be used on medium sized appliances, I've seen nothing suggesting Checkpoint can deliver this.
The only way forward is to radically rethink about the hardware platforms to ensure dedicated https inspection resource is built in (The NVidia card is likely to be utilised for this function, but this is high-end appliances).
So basically, if you have a regional office why buy checkpoint when other vendors have an appliance that is targeted at medium sized offices while ensuring all blades can actually be used without compromising on performance.
Keep in mind business want security but they are not going to spend an unrealistic amount for a regional site installation.
Please Checkpoint can we understand what the road map will be for this targeting medium sized deployments.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have you also noted that in the sizing tool, there is no https inspection option...ummm wonder why!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Never really paid attention to it, but no need to wonder any longer : - )
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would argue that many of those competitors compromise on security that they provide and/or the security of their own platforms.
Regardless, I understand the concern.
We've made some performance improvements in the most recent releases and more are planned for the next release (R82).
I presume some details about this will be covered at CPX.
It might be better to have a conversation with your local Check Point office with your precise performance requirements.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can argue that but there is a moment when the renewal time is there, the prices of CP and the competition are in and we explain the customer that it will be better in the next release of the next platform when some are still only upgrading to R81.10 from R80.X because of cost, operational and hotfix maturity reasons, especially with VSX and advanced platforms.
Now I understand we'll be in a mix of R80.40, R81, R81.10, R81.20 and then R82 which each have their own set of capabilities, some of which might be ported back or not.
Some customers don't even know what version they run, they trust us integrators to make the best out of their installation base.
They don't ask for a new OS each year.
I might be naive but I'd rather see R81.10 as a long-term R81 release with all the features integrated along in jumbo's as long as it's feasible (IoT, Hyperflow, SD-WAN, the announced HTTPSi auto-detect) and R82 as a major stepstone with future improvements which really can't be ported back in R81.10.
That would be much clearer to customers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Very logical points @Alex-
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mellanox (acquired by Nvidia, but ConnectX predates that acquisition) makes programmable switch chips. ConnectX-6 adds AES-XTS hardware to offload the symmetric portion of TLS, and you can toss the asymmetric parts onto the card's CPU, but it's not great at the kinds of operations needed for TLS interception (generating new key pairs and low-latency signing operations). From the description of the Lightspeed cards, they sound more like ConnectX-5 (my bet would be the same chip as the MCX516A-CCHT), which does not have the AES-XTS hardware. I know Check Point's other cards like the 2x40g and 2x100g are ConnectX-4 and ConnectX-5.
For HTTPS Inspection acceleration, I would actually expect a Marvell (formerly Cavium) Nitrox V, which is the product line used by most load balancers with hardware TLS. Maybe an Intel QuickAssist card. Check Point gets their hardware from Lanner. Many of Lanner's 1U network-focused boxes have a fully-internal slot for a custom-form-factor PCIe card. I know of at least one load balancer vendor which also gets their hardware from Lanner, and they offer a Nitrox V card which goes in that internal slot.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great insight on the hardware side of things, thanks!
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is way off topic, but if you want to see some other interesting hardware, check out Barefoot's (acquired by Intel in 2019) Tofino line. The Tofino 2 has up to 256x 56g SerDes lanes, allowing up to 128x100g interfaces per switch chip. Fully programmable data path with P4, which is a fascinating language. Essentially, you define a set of headers, the parsing logic to populate them, then stateful forwarding actions to take based on header values. It can do really fancy forwarding at line rate across all ports. The chip itself is HUGE. BGA4432 with roughly 1/2 the pins for ground, 1/4 for V+, 1/4 for all the SerDes lanes.
I haven't taken a Maestro orchestrator apart, but my understanding is they use a Broadcom Tomahawk. Intel bought Barefoot to compete with Broadcom in that space. The acquisition seems to have been connected with Omni-Path's discontinuation.
Oxide is using Tofino 2 to do some extremely cool stuff in their switches. Incidentally, their sleds use 100g network interfaces from Chelsio, which is a whole other rabbit hole.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Turns out I was wrong about the Maestro orchestrators. I had completely missed that Mellanox has their own semi-whitebox Ethernet switch line (now that they're owned by Nvidia, they sell them directly with Cumulus preinstalled, but they're also available with ONIE) which they call Spectrum. The MHO-140 appears to be an Nvidia SN2410 and the MHO-175 appears to be an Nvidia SN3700 or possibly SN3700C. Not sure about the MHO-170.
Given the normal interface cards from Mellanox and the "lightspeed" accelerated data path cards also from Mellanox, this makes sense.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I finally got a chance to poke a QLS250. It has a nearly identical PCIe topology to the 16200. The only difference is the 16200 has four PCIe 3.0 x8 root ports going to the slots, while the QLS250 has two PCIe 3.0 x8 root ports and the other two are combined into one PCIe 3.0 x16 root port. The specialized network card has the PCIID 15b3:101d (find the card in 'lspci -vv', take note of the address, then find it in 'lspci -nv'), which is a Mellanox ConnectX-6 Dx. Nice to see I underestimated the hardware used for the specialized forwarding path.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is what we thought and were afraid of. However, I suppose I just assumed IPS was smarter and able to detect more somehow.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Realistically, yes you do need HTTPS Inspection for proper IPS functioning. Without it IPS will still be able to inspect cleartext payload data, packet headers, and the initial client/server negotiations prior to the start of encryption in the case of HTTPS. Given that around 85-90% of web traffic is now HTTPS you will be missing a lot. This is why HTTPS Inspection was extensively covered in my IPS/AV/ABOT Immersion class even though it is not directly related to those features. Also don't forget about SSH, Check Point firewalls do support SSH Deep Inspection and the cool ability to block port forwarding, but this feature can only be configured from the CLI of the gateway which is why few people know about it.
Performance is definitely a concern, but at least some of that can be mitigated with a properly ordered & configured HTTPS Inspection Policy to avoid multiple HTTPS Policy lookups for the same connection, and avoid unnecessarily triggering Active Streaming when it is not absolutely needed. See here: HTTPS Inspection Policy Rule Order
At some point the Lightspeed/Nvidia card will probably be able to handle at least the HTTPS bulk encryption & decryption aspect, as part of this initiative SecureXL is making the transition out of the kernel (sim) to User Space (UPPAK/usim) starting in R81.20 on Lightspeed systems.
The unofficial way to estimate the performance impact of HTTPS Inspection is to cut the rated throughput of the appliance in half. So if an appliance is rated for 3Gbps with the features you will be using(NGTP,NGTX, etc), to account for HTTPS Inspection cut that number in half to 1.5Gbps.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Check Point firewalls do support SSH Deep Inspection and the cool ability to block port forwarding, but this feature can only be configured from the CLI of the gateway which is why few people know about it.
Any links or references ? 8)
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
SSH Deep Packet Inspection got a mention in my IPS/AV/ABOT Immersion course and the relevant page is below. There is no SK article for this feature; it is only documented in the Threat Prevention Administration guide starting in R80.40 when it was introduced.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think you got all excellent answers, specially from @Timothy_Hall . In short, ANY vendor would tell you the same, to truly benefit from IPS/app control, you definitely should have inspection enabled. I mean, its reality nowdays that literally 99% of the world's websites are https, so it only makes sense to have that feature enabled for proper inspection.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
and thats my point hardware base https inspection should be in all the models a vendor has; now clearly if you have a 6200 the real work performance level will difference to say a 16200.
So it would make sense that hardware https inspection would be rated to say 500Mbps on a 6200 but 2GBps on a 16200 because the hardware https module would be spec'ed according to the gateway appliance used.
Without https inspection you realistically can only just use the firewall blade if this is just an internet gw., which makes Checkpoint expensive and negates all the real cool blades that justify the costs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
From the recent CheckMates Fest:
While it clear that HTTPS Inspection is needed to inspect traffic up fully, there are challenges with both implementation and the fact not all traffic can be inspected. What are we doing to improve these challenges?
We are addressing both performance and usability challenges during the coming year, some of which will land in the next major release (R82). We are also developing a "learning mode" which will help identify potential issues during deployment and provide recommendations.
You can see what Gera has to say about this in the video, and I suspect we'll have more to say about it at CPX.
Note that at this point, we're focused on software-level changes.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R82? I expect SPECTACULAR things out of that version...I mean it : - ). And, if I may, here is the name suggestion...Hercules ; )
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Appreciate the generalization but what about non-HTTPs traffic?
Also controls such as Anti-bot & DNS security for example...
CCSM R77/R80/ELITE
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Tue 28 Oct 2025 @ 11:00 AM (EDT)
Under the Hood: CloudGuard Network Security for Google Cloud Network Security Integration - OverviewTue 28 Oct 2025 @ 12:30 PM (EDT)
Check Point & AWS Virtual Immersion Day: Web App ProtectionTue 28 Oct 2025 @ 11:00 AM (EDT)
Under the Hood: CloudGuard Network Security for Google Cloud Network Security Integration - OverviewTue 28 Oct 2025 @ 12:30 PM (EDT)
Check Point & AWS Virtual Immersion Day: Web App ProtectionThu 30 Oct 2025 @ 03:00 PM (CET)
Cloud Security Under Siege: Critical Insights from the 2025 Security Landscape - EMEAThu 30 Oct 2025 @ 02:00 PM (EDT)
Cloud Security Under Siege: Critical Insights from the 2025 Security Landscape - AMERAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter