- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Threat Prevention
- :
- Re: Default DNS Trap and malware detection?
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Default DNS Trap and malware detection?
Please advise if it is normal for Check Point default DNS trap to be identified as known to contain malware:

As per Anti-Virus Malware DNS Trap feature , The default value for DNS trap IP is 62.0.58.94.
Thank you,
Vladimir
- Tags:
- dns trap
9 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
DNS Trap means that the DNS request was intercepted and the gateway responded to the client with that bogus IP address. The malicious part is not the IP address 62.0.58.94, but the hostname etacontent. com.
You won't see the real IP address for that suspicious host because the query was intercepted before it reached the external DNS server and the response was replaced by the DNS trap address.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I guess that your log shows what happens after it receives the bogus IP.
Client -> DNS request for a malicious website
Client <- Gateway intercepts/acts as DNS server and tamper the respons with the false IP address 62.0.58.94
Client -> Tries to go to IP address 62.0.58.94 (Your log shows this step).
Here is a similar example where the destination is 62.0.58.94:
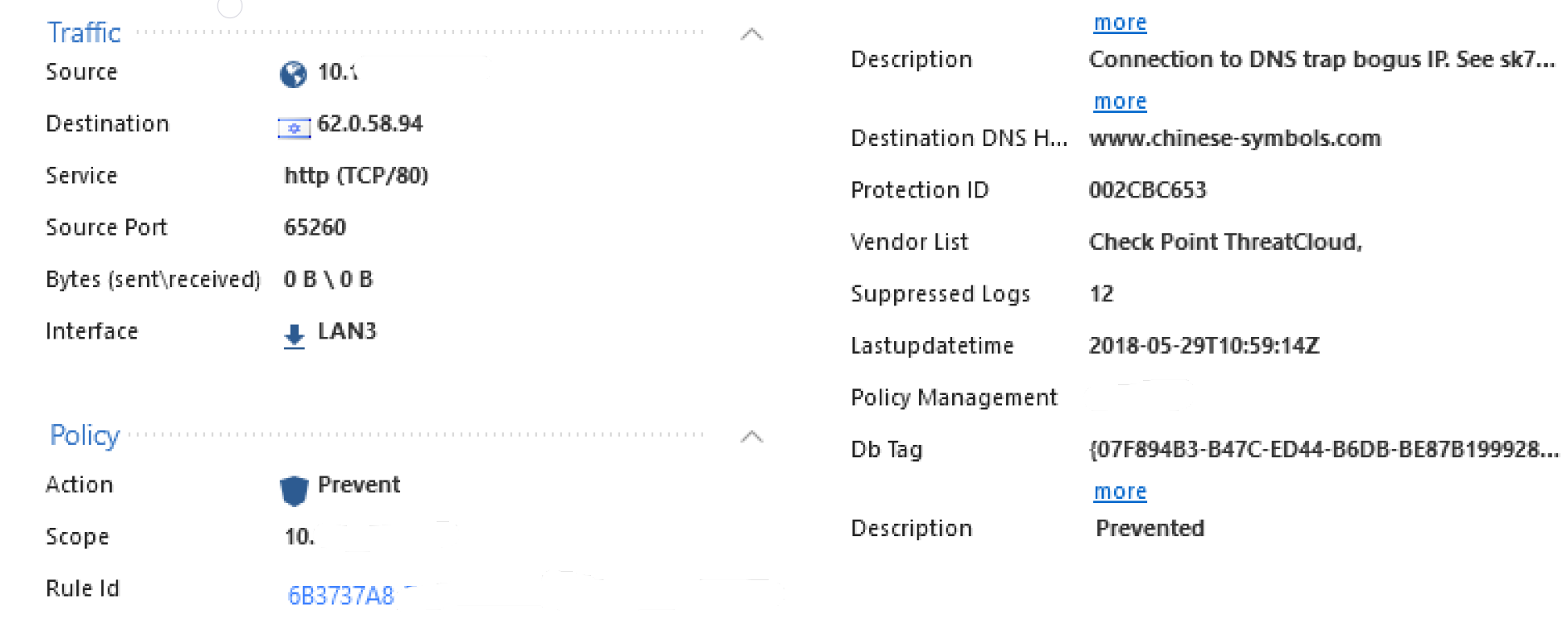
This examples shows that suppressed logs are 12 telling how many connections were made during a session.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Looks about right, but it would be helpful if CP would serve a page stating that the redirect took place for a reason, rather than terminating it on a blank.
My confusion was caused by trying to deliberately access 62.0.58.94 via HTTP and seeing the message shown in the first post, while in fact, the TRAP event was caused by a different machine on the same network.
Trying to access the http://62.0.58.94 directly does not, apparently, generate event logs.
Took me a few minutes to spot the difference of originator IP's.
Thanks guys!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The primary reason, if I'm not mistaken, for the DNS trap is to uncover the real host that made DNS request. Otherwise, we would be flagging the DNS server for forwarding the requests which doesn't do us any good. Of course the DNS server is resolving what is asked of it. By giving the host a bogus IP, and then waiting for the IP to come through we can flag the end host that is infected.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Makes sense, it would just be helpful to have these events better differentiated. I.e. without knowing the default DNS trap IP by heart, this prompts an investigation in misleading direction, (at least this is what happen in my case).
Speaking of this event being indicative of the hosts being infected: One of my clients called in today stating that they are seeing the growing rate of similar events from increasing number of PCs.
My first reaction, predictably, was that they have bought it, and that there is a laterally propagating malware loose in the network. Their endpoint protection, however, is staying mum.
No machines, as of yet, crashed and burned or have asked nicely for bitcoin deposits.
Now I am thinking that these events may be caused by one of the sites frequented by employees hosting malicious payload and, as the day progressed, more and more people accessing it.
For now, Check Point seem to be holding the fort, but am surprised not to see anything on endpoints.
The site in question is likely served via SSL and since there is no HTTPS inspection in place in that environment, we are seeing actions by the clients, but not flagging the real source.
Does this scenario sounds plausible?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
From my experience a massive "DNS Reputation" events could have been because a blacklist was created thru object type "Domain" and put in Access Rule policy.
Then, firewall will try to research IP address for every each all time.
In this case, best practice could be use "indicators" feature. So event reports will be cleaner and better behavior.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Also, a blank page is given because when a bot makes the connection it won't know it is being redirected to a different destination.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nice!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Should I allow traffic to the bogus trap IP in security policy rule?
Upcoming Events
Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


