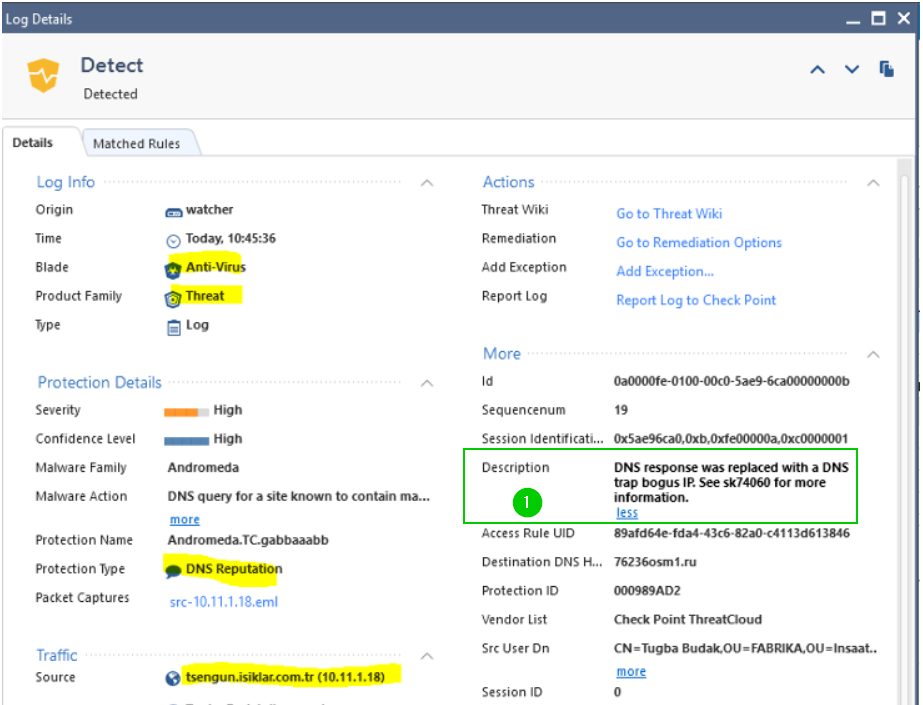
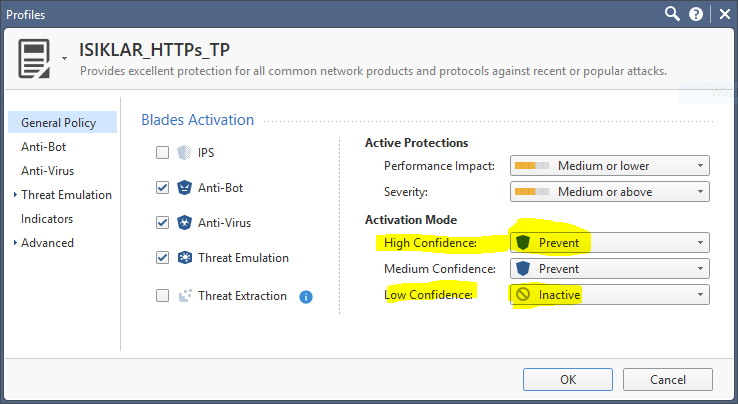
In most conventional infrastructures, your DNS lookups traversing the firewall will be from the internal DNS server configured to perform recursive lookups, not the actual client.
I.e. in rudimentary AD environment, this role is frequently resides on Domain Controller servers configured as DNS.
So the typical lookup from the client queries the DC for the resolution of the name, if it is not yet cached there, DC then performs the lookup and created a brunch in its cache for the domain in question.
If your environment is similar to what I am describing here, or if you are using any recursive DNS servers, check their logs to see which client has requested lookup of bad domain.
As to creating a special rule for handling this and alerting you, It makes little sense in my opinion, as C&C networks are pretty dynamic and the built-in threat prevention is designed to handle it.
From the point of view of finding the infected clients, especially in recursive DNS environments, If you have SmartEvent, I would configure a notification alert to either email or send an SNMP trap for these events and, if you would like to further automate the process of looking up infected clients, use a third party such as phantom:
Phantom: Security Automation & Orchestration Platform
You can request a fully functional and non-expiring copy of it for free from vendor, its only limitation is the number of events it will be allowed to process per day.
Otherwise, you'll have to script the process.
Regards,
Vladimir