- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Access Control and Threat Prevention Best Practices
5 November @ 5pm CET / 11am ET
Firewall Uptime, Reimagined
How AIOps Simplifies Operations and Prevents Outages
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Spark Management Portal and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Threat Prevention
- :
- Re: Bypass Windows & Office update from TP (AV & S...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Bypass Windows & Office update from TP (AV & Sandboxing)
Hi,
We are having an issue with DLPUD process which is pending for weeks (TAC involved)
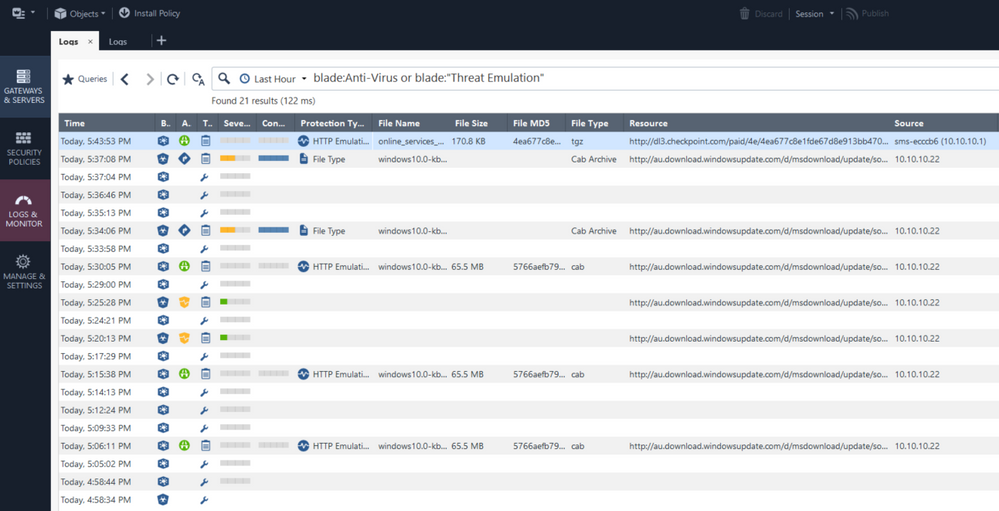
We found that some CAB files from Microsoft & Office update are passing through the Threat Prevention Layer and some AV action are done on the file. Files are written to the disk for inspection.
This process is causing high Disk utilization and increase CPU on our Gateways
Here is an example of log from dlpud.elg
[28962][3 Mar 10:01:20] Start [1A] umsess=0x8ecb9a0 (x.x.x.x:52535 -> 87.248.222.128:80) initiator=0x8 partial=1(4194304-5242879/68673795) strict_hold_skip_active=0 orig_file=windows10.0-kb5010472-x64-ndp48_07d328da3e495d688287607c0c4748cb4a327b90.cab tmp_file=/opt/CPsuite-R81.10/fw1/tmp/dlp/{E645F264-B9F1-3ECE-F3F6-D2A5A6C2C855} file_unique_id=
This directeory is full of file that are sometimes not cleaned du to a DLPUD crashed - /opt/CPsuite-R81.10/fw1/tmp/dlp/
This lead to full disk utilization are require at the moment manual cleanup...
If we look at the Firewall logs based on filename windows10.0-kb5010472-x64-ndp48_07d328da3e495d688287607c0c4748cb4a327b90.cab. We can see that:
Time: 2022-03-03T09:01:12Z
Interface Direction: outbound
Connection Direction: Outgoing
Id: c0a80101-6a65-0000-6220-83d80000001c
Sequencenum: 46
Hll Key: 13342166036668581550
Duration: 60
Last Update Time: 2022-03-03T09:01:16Z
Update Count: 2
Creation Time: 2022-03-03T09:01:12Z
Connections: 2
Aggregated Log Count: 2
Source Country: United States
Source: x.x.x.x
Destination Country: Unknown Location in Europe/SW Asia
Destination: 87.248.222.128
Destination Port: 80
IP Protocol: 6
Client Type: Other: Microsoft-Delivery-Optimization/10.0
User Agent: Microsoft-Delivery-Optimization/10.0
Protocol: HTTP
Sig Id: 0
Service ID: http
Application ID: 10074906
Application Signature ID:10074906:3
Method: GET
Action: Accept
Type: Session
Db Tag: {23137267-A306-D44E-8AA2-D0EF42FA9BA1}
Policy Date: 2022-02-25T10:21:19Z
Blade: Application Control
Service: TCP/80
Product Family: Access
Logid: 288
Application Name: Windows Update
Application Description: Windows Update is a Microsoft tool that enables users to setup automatic updates for their products.
Primary Category: Software Update
Matched Category: Software Update
Additional Categories: Very Low Risk, Microsoft & Office365 Services, Software Update, Web Services Provider
Application Risk: Very Low
Resource: http://au.download.windowsupdate.com/d/msdownload/update/software/updt/2022/01/windows10.0-kb5010472...
Access Rule Name: App_Updates
Access Rule Number: 242.11
Policy Rule UID: 79aa6811-dc90-4e5b-b300-6c4c0b0d62bf
Marker: @A@@B@1646289832@C@4404630
Index Time: 2022-03-03T09:02:11Z
Lastupdatetime: 1646298132000
Lastupdateseqnum: 46
Severity: Informational
Confidence Level: N/A
Stored: true
URLs: 1
Layer Uuid Rule Uuid: ca2438ac-7706-4b85-ac70-eb7a63e55f34_3285e8df-63e0-48ca-94e6-d986b2c10da6, a6a6961d-6d63-4169-9d12-7e0eca58f093_79aa6811-dc90-4e5b-b300-6c4c0b0d62bf
From what we know there is 2 options to do a correct bypass in Threat Prevention (Updatable Objects or Custom App with URL). Unfortunately there is no object for Windows Update / Office in Updatable objects (that would be very helpfull...)
We then implemented URL Regex exceptions that should match or URL
^windowsupdate\.com
\/windowsupdate\.com
\.windowsupdate\.com
However files are still inspected by TP and cause our daily crashes
Any recommandation to bypass Windows Update & Office update from TP are welcomed 🙂 Please note it's HTTP and not HTTPS traffic so no option to do a more global bypass with HTTPS...
I guess we are not the only one in this situation. Gateways are in R81.10
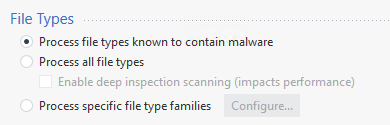
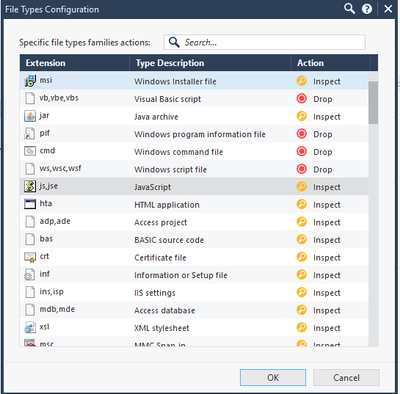
Last option is to bypass CAB from TP profile but as we don't want to cause more issue than we have today we need to stick the custom profile with default options but there is no doc about this
- It’s now defined as « Process files types known to contain malware
- We can migrate to « Process specific file type families but we first need to configure this settings with similar option that applied at the moment – Please provide the match between both settings
Thank you
24 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Interesting I would expect TE should handle these natively as a "Trusted Source".
Regarding alternate bypass syntax examples refer also:
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I also thought it were natively excluded but unfortunately it's not the case
I added (^|.*\.)windowsupdate\.com however this syntax is not recommeded for performance purposes 🙂
Our Regex should match the URL already so I'm not expecting improvement.
On top of that we have same issue with Office on a different URL also bypassed with URL exceptions
From my point of vue we should have an updatable object for perfect match
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm checking internally regarding the trusted sources, please message me your SR number if you wouldn't mind.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
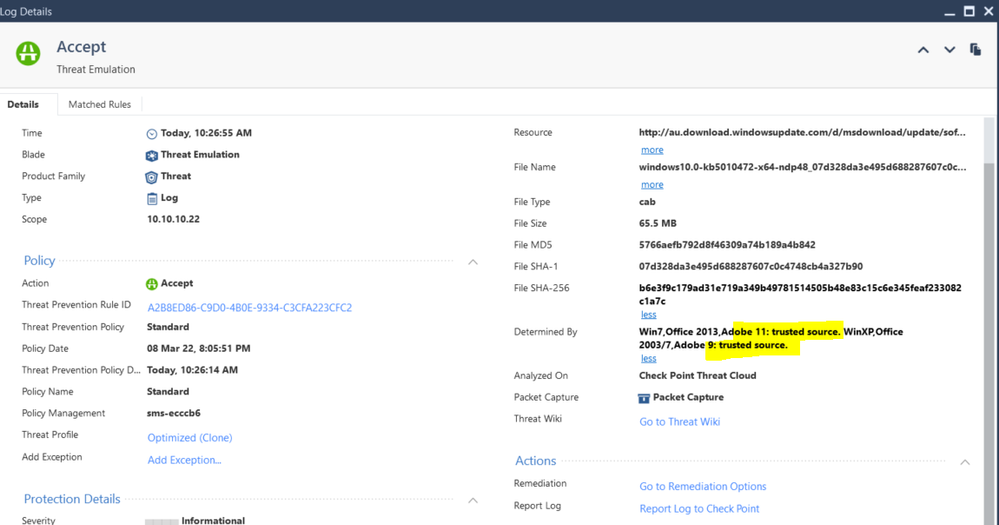
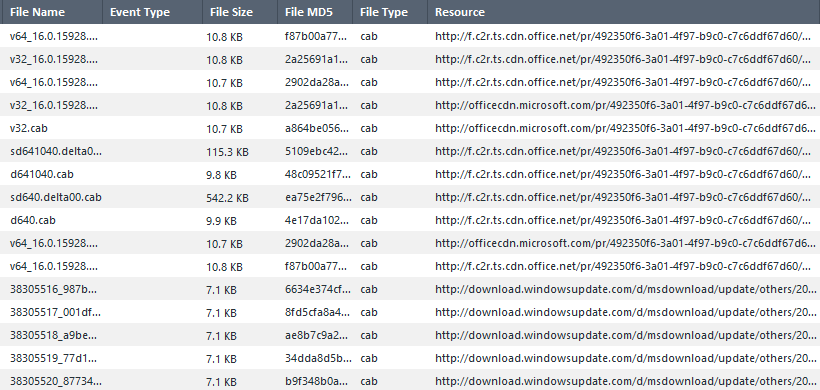
If a file exceeds the defined emulation file size limit set for TE then it won't report that it is a trusted source, this is outlined in sk114522 and sk166366. In the below example I have changed the TE limit from the default 15MB to 100MB to demonstrate Windows update is indeed trusted for the example file/download.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Thank you for this update
I understand that Trusted source is not detected due to the size but it should be bypassed with the Regex in the custom App
TAC confirmed that the bypass with regex should match but it's not the case
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I just tested the same download URL with the following exception configured and it works as expected (this is on R81 JHF T58).
With the exception disabled the file is either Emulated (benign verdit/trusted source) or blocked/scanned by AV depending on the profile configuration.
You can see in the logs below the intermediate "control" log types where threat prevention policy was installed to toggle the exception state - between which a download was initiated and no logs were generated by the applicable TP blades.
Will update my lab to R81.10 over the weekend and test again for continuity.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
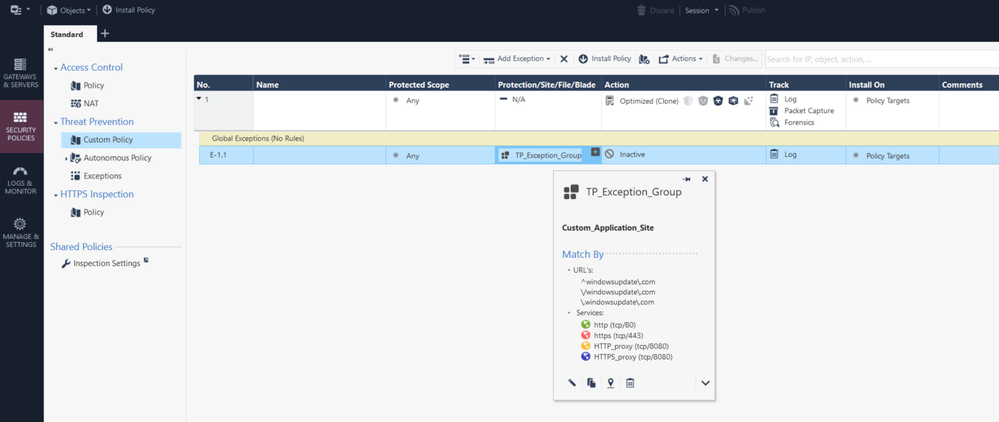
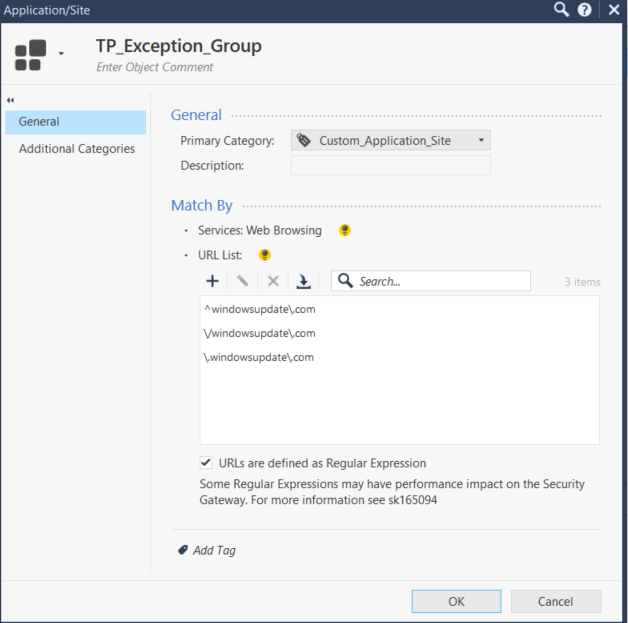
Can you please share the content of the TP_Exception_Group ?
Also can you please describe when the Profile is enabled or not as I see some AV events after each installation
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can see the contents of the group under it, it contains just the three regex entries that you supplied in an earlier post i.e.
^windowsupdate\.com
\/windowsupdate\.com
\.windowsupdate\.com
(It's just a custom application site with multiple entries despite the name)
In each of the instances the AV events occurred only after disabling the exception and specifically configuring the profile to perform Deep archive scanning or to explicitly block CAB files (since I wanted to ensure there would be a log entry).
For clarity multiple on/off test were performed.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Confirmed behavior is unchanged after upgrading to R81.10 JHF T30 and the exceptions work as configured.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
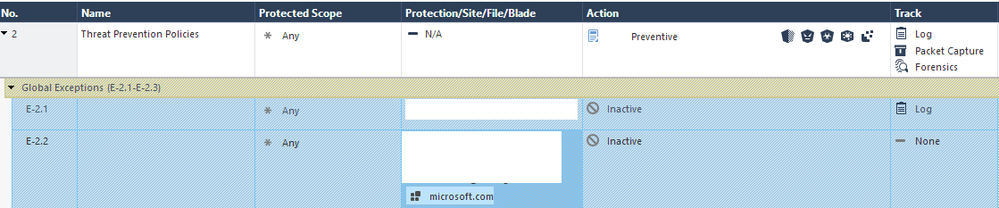
Hello Chirs,
it seems that it is not possible to use it inside a policy with a "Null_Profile" to fully accelerate traffic.
Only way is to use exception so TP Engine will be triggered.
any solution? my rule with FQDN seems to be ignored
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What's the scope of what needs to be allowed in your case is it an entire fleet or just a WSUS server or similar?
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
i wanna bypass all these stuff:
i've tried: HTTPS bypass Updatable Objects, FQDN objects, RegEX... it doesn't work neither with Null_Profile nor in Global Exceptions with Inactive action
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For multiple internal source machines correct?
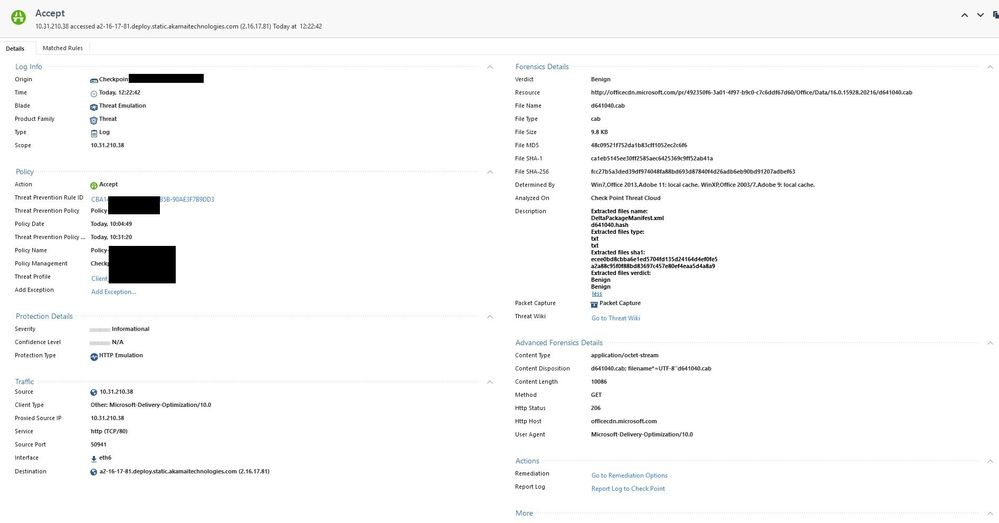
Can you share one of the log cards in more detail please?
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
yes, basically for all internal desktop; log card here:
probably last resort is disable .cab files from emulation...
let me know if you need more info
thank you for your help
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
this is definitely the weirdest thing that i've seen with TE:
is trusted source functionality broken?
on my gw should be enabled:
1:2]# tecli advanced attributes show | grep trusted
trusted_source value is: enabled
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I can't see "office" domains in the list, so that's something I'd probably take with your SE for discussion.
For context what file size limit is configured here - just the default 15MB or has it been lowered considerably?
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, default size 15MB
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
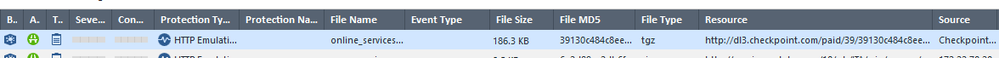
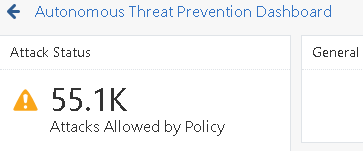
Have you ever found a solution to this? It seems that ever since Threat Emulation was enabled we have a ton of Microsoft.com files being scanned, and logged because of the file size. It shows up on the reports as possible attacks. However, so far none of them seemed to be malicious.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Having reviewed sk114522 & sk166366 are you expecting something different?
What TP exceptions do you have configured if any and are the URLs encountered "office" domains or others?
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I guess maybe I shouldn't be expecting anything different from what is being shown. I can't help but think the logs I am seeing shouldn't be logged this way because of the overheard (if any?). Log example below.
Currently testing this out: https://support.checkpoint.com/results/sk/sk172928
------------------
This is how I have it configured. I'll post the changes I did above after tests are complete and after I can move over global exceptions into another exception profile since it applies to all at the moment.
These are happening all the time for our Exchange servers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Tried to add the latest Regex but files are still processed by TE
[28958][3 Mar 13:51:01] Start [8EB] umsess=0x86c7c10 (x.x.x.x:63011 -> 23.72.249.12:80) initiator=0x8 partial=1(29360128-30408703/68677217) strict_hold_skip_active=0 orig_file=windows10.0-kb5009467-x64-ndp48_28770b5a14360312b6e3c34422d6f14e8a05de6f.cab tmp_file=/opt/CPsuite-R81.10/fw1/tmp/dlp/{6B22D288-076A-3E63-6788-FA419791928C} file_unique_id=
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
For your info TAC suggest to implement sk163595 for the bypass which is already done
I checked on other infra and all have these CAB files inspected
Are we the only one that want to bypass this updates from TP ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Don't know but we've tried multiples Regex, implement SK, opened multiple ticket with TAC and no solution were found...
The best would be an updatable object for Windows & Office Updates but it's not available
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Wed 05 Nov 2025 @ 11:00 AM (EST)
TechTalk: Access Control and Threat Prevention Best PracticesThu 06 Nov 2025 @ 10:00 AM (CET)
CheckMates Live BeLux: Get to Know Veriti – What It Is, What It Does, and Why It MattersTue 11 Nov 2025 @ 05:00 PM (CET)
Hacking LLM Applications: latest research and insights from our LLM pen testing projects - AMERTue 11 Nov 2025 @ 10:00 AM (CST)
Hacking LLM Applications: latest research and insights from our LLM pen testing projects - EMEAAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter