- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Threat Prevention
- :
- Re: Block torrent applications
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Block torrent applications
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Like I said, you need to limit either the destinations, the services, or both.
This advice applies to one or more of 8, 17, 20, 24.
Each one of these rules could easily be two rules.
One example:
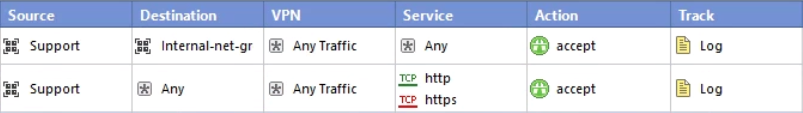
Replace http/https with the precise services that are actually required for Internet access and nothing more.
This is by far the most performant approach.
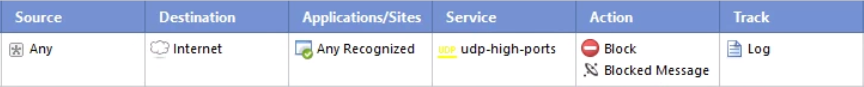
Another option would be to put a rule near the bottom of your App Control rulebase like the following:
To get the Service column to show up in your App Control rulebase, right click on the title bar and check Service.
If you don't want to outright block the traffic, you can instead use the action "Limit" and specify whatever sort of limit you wish to place on this traffic.
Note the limit applies for anything matching this rule and should be below more specific rules.
12 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please share some additional information if you would like assistance e.g.
- Version & JHF?
- SSL / HTTPS inspection? Y/N
- Classification (hold) mode Y/N
- What alternate rule in the policy is matching the traffic?
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Version :- R77.30
SSL/HTTPS - N
Classification - N
Currently no policy is there except the Application block policy which is of no help.
Thanks
Prashant.
SSL/HTTPS - N
Classification - N
Currently no policy is there except the Application block policy which is of no help.
Thanks
Prashant.
Prashant
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What rules are the traffic matching on instead and how do those rule relate to the one you've shown?
Based on that we might be able to make suggestions.
Also note that R77.30 is End of Support and it would probably be a good idea to upgrade to a supported release.
Based on that we might be able to make suggestions.
Also note that R77.30 is End of Support and it would probably be a good idea to upgrade to a supported release.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
UDP utilization is showing too high for interface when checked. so i checked client pc remotely he is using torrent. now i don't want him or anyone else to use torrent.
Yeah, received the new firewall but waiting for downtime from management.
Thanks,
Prashant.
UDP utilization is showing too high for interface when checked. so i checked client pc remotely he is using torrent. now i don't want him or anyone else to use torrent.
Yeah, received the new firewall but waiting for downtime from management.
Thanks,
Prashant.
Prashant
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Understood, but what rule(s) are matching the traffic in question?
In this case, both Firewall and Application Control rules?
I suspect you're allowing UDP high ports to random places on the Internet, which is generally not best practice.
In this case, both Firewall and Application Control rules?
I suspect you're allowing UDP high ports to random places on the Internet, which is generally not best practice.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
yes both FW and Application control rules.
I suspect you're allowing UDP high ports to random places on the Internet, which is generally not best practice. - How do i stop this??
Sorry i am not having much knowledge of firewalls doing just some RnD. Support is not available trying to do it myself.
Prashant
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You sent a screenshot of the Application Control rule you thought should have blocked Bittorrent, so clearly you have access to SmartDashboard...and probably SmartView Tracker and/or SmartLog to see the logs of the traffic.
As a general rule in R77.x and earlier: in order to pass through the Firewall rulebase, there has to be an explicit rule that allows the traffic.
What precise rule is allowing the traffic?
SmartView Tracker and/or SmartLog should tell you if it's not obvious from looking at your rulebase and you have logging enabled on your rules.
Then, in R77.x and earlier, if the Firewall rulebase allowed the traffic, it goes to the Application Control rulebase.
In this rulebase, unless there is an explicit rule that blocks traffic, it will be allowed.
Note that in R80.x with Policy Layers, this behavior is different as you can potentially have many layers and set the default behavior for each layer differently (default deny or accept).
As a general rule in R77.x and earlier: in order to pass through the Firewall rulebase, there has to be an explicit rule that allows the traffic.
What precise rule is allowing the traffic?
SmartView Tracker and/or SmartLog should tell you if it's not obvious from looking at your rulebase and you have logging enabled on your rules.
Then, in R77.x and earlier, if the Firewall rulebase allowed the traffic, it goes to the Application Control rulebase.
In this rulebase, unless there is an explicit rule that blocks traffic, it will be allowed.
Note that in R80.x with Policy Layers, this behavior is different as you can potentially have many layers and set the default behavior for each layer differently (default deny or accept).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
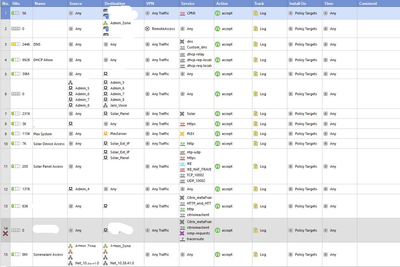
We have some firewall rules which state from any to any. please find the SS attached.
Prashant
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For an effective strategy you will need to limit (reduce) the number of such rules and get more detailed with the permitted services and destinations.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
i will make sure of that during the installation of latest firewall. for time being i am looking for the solution to block torrent or limit the download speeds(only for torrent not whole interface).
Thanks,
Prashant.
Prashant
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
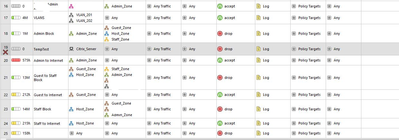
Like I said, you need to limit either the destinations, the services, or both.
This advice applies to one or more of 8, 17, 20, 24.
Each one of these rules could easily be two rules.
One example:
Replace http/https with the precise services that are actually required for Internet access and nothing more.
This is by far the most performant approach.
Another option would be to put a rule near the bottom of your App Control rulebase like the following:
To get the Service column to show up in your App Control rulebase, right click on the title bar and check Service.
If you don't want to outright block the traffic, you can instead use the action "Limit" and specify whatever sort of limit you wish to place on this traffic.
Note the limit applies for anything matching this rule and should be below more specific rules.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Thank you very much for your all help and support.
i limited the traffic through the application rule.
now seems to be working fine with bandwidth.
Thank you very much for your all help and support.
i limited the traffic through the application rule.
now seems to be working fine with bandwidth.
Prashant
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Fri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter