- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Quantum (Secure the Network)
- CloudGuard CloudMates
- Harmony (Secure Users and Access)
- Infinity Core Services (Collaborative Security Operations & Services)
- Developers
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Infinity Portal
- Products Announcements
- Threat Prevention Blog
- CheckMates for Startups
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
CheckMates Toolbox Contest 2024
Submit a Tool for a Chance to WIN a $300 or $50 Gift Card!
May the 4th (+4)
Roadmap Session and Use Cases for
Cloud Security, SASE, and Email Security
Harmony Endpoint:
Packing a Punch in 2024
CPX 2024 Content
is Here!
Harmony SaaS
The most advanced prevention
for SaaS-based threats
CheckMates Go:
The Difference Is In The Details
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Management
- :
- Re: basic network config
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
basic network config
I recently bought a 3000-series appliance and am having difficulty connecting it to my network. I have a small business cable internet connection with a regular cable modem. I would like to use my cable modem's DHCP server to keep things simple.
I wired it up like this:
Cable Modem Eth0 Port to CheckPoint eth5 Port
CheckPoint eth0 Port to laptop
Can anyone share what my network settings on the firewall should be?
I have the interfaces set to "Obtain IPv4 address automatically" and set an IPv4 Static Route of, "Destination Address: Default" to Gateways: "eth5"
I'm not getting any DHCP address on my laptop and if I set a static IP and try to ping my cable modem from my laptop it will not ping.
I'm probably in over my head, but I want to use this to replace my old Meraki device and am pretty excited to start learning the platform. Any help you could spare would be immensely appreciated.
8 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Seems to me that there are number of things that you should configure for your setup to work properly:)
1. On your 3000 appliance is the interface labeled "Mgmt" I suspect that you have used it for initial configuration of the appliance. Please connect your laptop/management PC to it.
2. Configure static IP address from the range you were previously getting from your router on eth0 (i.e. 192.168.1.2 with the gateway being the that of your router, i.e. 192.168.1.1)
3. You will be better-off using firewall's built-in DHCP server, instead of passing-through the DHCP requests to your router, so I suggest defining another network for internal scope (i.e. 192.168.2.0/24) and assign it to your eth5.
4. For DNS, I suggest using 9.9.9.9 (IBM quad9 secure DNS server that is marginally better than Google's in terms of privacy)
5. Now, create the outbound rule permitting network 192.168.2.0/24 to access the Internet.
6. Once connected, enable security features such as IPS, AV, Antibot, etc... and configure their automatic update schedule.
Cheers,
Vladimir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am very much agreed with Vladimir. To add, just login to the modem (most probable IP would be 192.168.1.1 - depends on modem) and check the settings, IP ranges etc. You should give IP to eth5 within that range and after that you can follow with Vladimir's post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Don't forget-if using another address range for your internal network you will need to configure the 3000 device to NAT that traffic so that the cable modem recognizes those packets.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You will need to configure DHCP relay to point to the modem as the gateway will drop all broadcast traffic if each gateway NIC is a layer 3 interface, as opposed to bridge mode like on the smaller 1400 appliances where all interfaces are sitting in a single logical switch named LAN1.
Honestly though, just do DHCP on the gateway and ensure rule 1 permits bootp and or DHCP requests to the local module to ensure DHCP is not dropped on the stealth rule.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I really appreciate the help you all are offering me. I'm still stuck at the basic connectivity of this darn thing!
I set rule 1 to allow all from all to all just to keep it simple and get this thing working. No other rules exist.
Could anyone specifically tell me what exactly I should set the interfaces to as an example? I tried doing what was recommended above but none of it worked. I must be doing something wrong, but after a ton of hours I just can't get it! I really wish there was a simple write-up on how to get this to work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI Red,
I feel your pain. Although there is no "simple write-up" for a 3200 appliance - Check Point is kind of complicated - it seems to me the first step here is to see if the firewall has an outside IP address and can see the world.
First thing: Does the firewall have a public IP address on eth5? You set it to get a number assigned automatically, but did it actually get an address?
Second thing: I notice you set the default gateway to "eth5" the default gateway for the firewall would not be its own interface. It would be the IP address of your modem or some other address the modem hands the firewall. (It would basically be the same stuff handed to your PC if you connected it direct.) Bottom line, it would be a public IP address different from the firewall's external IP. And looks something like this:
More importantly, if your outside interface is getting a DHCP-assigned address, then it should automatically pick up the default gateway as well. The fact that you're writing your own default gateway kind of makes me stop and go, "Hold on, let's back up a step."
So, I would start there. Do you have an actual IP address on the external interface? Is the default gateway set to the upstream modem? Can you ping it?
All of these need to be "yes" before you can really do anything else.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Let's start with some basic questions:
- How many public IP addresses come with your service plan from your cable company? If you don't the answer to this question, it's probably one.
- Do you purchase any management appliances? My guess is probably not and you only have the 3200 appliance.
- Is your IP address static? If you don't know the answer to this, it's probably not static.
Assuming the answers are as I specified above, you will need to contact your cable company and inquire about a static IP address.
A static IP is required for a self-managed 3200 series appliance.
If you cannot get a static IP address, you will be much better off with a 7xx/14xx series appliance, which is generally more geared for this sort of deployment.
Regardless of the appliance, you will typically have two interfaces configured:
- A WAN interface that's connected to your Cable Modem.
- As noted above, this will be configured with a static IP address
- You will configure it with a default route--check with your ISP for the correct setting.
- A LAN interface that's connected to a switch with your other clients connected.
- This can be anything in the RFC-1918 address space (e.g. 192.168.0.1/24)
- DHCP can be enabled on this interface to allow your clients to be auto-configured.
You will also need to enable an Address Translation rule or have the following checkbox enabled on your gateway object in SmartConsole:
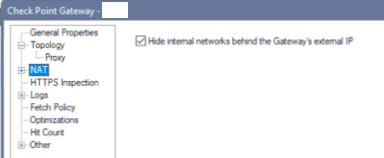
I strongly encourage you to engage with your local Check Point SE/reseller to assist you to make sure you have the correct solution for your deployment.
If you can send me a private message with where you're located, I can help locate the correct resource to assist you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not an ideal solution you have there with a 3000 box. You’re better off having that with a public IP on its external interface so see if you can bridge your cable modem so that you can get an external IP on your 3000-series. If that means you’ve got to set up a PPPoE connection, get something like a Cisco RV042 to sit between the firewall and the cable modem to make your life a bit easier. Disabling SecureXL to make the PPPoE connection work is a pain as it means you can’t do other stuff.
(Remember that the main function of your cable modem is just a means for your ISP to extract money from you on a monthly basis so don’t expect that box to be anything dazzling or “feature-rich”.)
If you can’t bridge the cable modem, provided you’ve got an IP range assigned to your connection, assign the same IP address to the internal interface on the cable modem as you have on the external interface of it and turn off any NAT and firewall. Then assign one of your other public IPs to the external interface of your 3000-series and use the IP of your cable modem as your DG. (This is also where the little Cisco box can help you out massively.)
Once you’ve done that, make sure Gaia can update itself with time via NTP. If it can’t, open a console window and ping stuff to see where the problem lies.
Next, make sure CPUSE can do its updates and apply the latest patches and Jumbo Hotfix.
Now you know you have an internet connection you can move on to SmartDashboard. Make sure you’ve got the latest version of that too.
Topology is important so make sure you have that correct and don’t activate any other blades until you know you have access externally. Log everything and get SmartLog auto-refreshing so that you can see what is going on.
Once you’ve got connection, turn on the blades one by one and push policy after each one so that you know the effect it has on the logs.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 8 | |
| 8 | |
| 5 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Thu 16 May 2024 @ 10:00 AM (CEST)
EMEA: Playblocks & MS Defender – Security Automation DeepDive into New Endpoint IntegrationThu 16 May 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - ACHTUNG, Sie werden gehackt! So schützen Sie sich!Thu 16 May 2024 @ 05:00 PM (CEST)
Americas: Playblocks & MS Defender – Security Automation DeepDive into New Endpoint IntegrationFri 17 May 2024 @ 10:00 AM (CEST)
CheckMates Live Netherlands - Sessie 26: ElasticXL & VSNext DescriptionTue 21 May 2024 @ 10:00 AM (CEST)
CheckMates Live DACH - Einführung in Check Points Hyperscalinglösung - Quantum MaestroThu 16 May 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - ACHTUNG, Sie werden gehackt! So schützen Sie sich!Fri 17 May 2024 @ 10:00 AM (CEST)
CheckMates Live Netherlands - Sessie 26: ElasticXL & VSNext DescriptionTue 21 May 2024 @ 10:00 AM (CEST)
CheckMates Live DACH - Einführung in Check Points Hyperscalinglösung - Quantum MaestroAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
Facts at a Glance
User Center


