- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- vpn access broken after setting up a cluster in hi...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
vpn access broken after setting up a cluster in high avaliablity
Hi Everybody,
We have a client who had a single 3100 series device and vpn worked with L2TP and the windows client no problem, for other reasons we where not able to use the checkpoint client vpn. This solutions has worked perfectly and been in place for a number of years.
We upgraded the client to two 3600 series devices, and setup the cluster in high availability mode, so far everything else is working except the vpn. The VPN worked once when I tested it and now nothing happens.
The internet is on eth1, fw1 x.x.x.98, fw2 x.x.x.99, cluster ip x.x.x.100. which is the ip we always connected to. We sent checkpoint the debug files last night.
I have noticed in testing, when connecting I don't get the normal prompt to enter a user name and password.
Has anybody else had issues with L2TP vpn connectivity in a high availability cluster ? My colleague has had no issues at other sites with a similar setup but those sites are using the checkpoint vpn software to connect.
Labels
- Labels:
-
ClusterXL
- Tags:
- vpn
13 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Were there other changes such as version involved at the same time, does it work when a specific cluster member is active?
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for the reply @Chris_Atkinson ,
I have tried with disconnecting one of the devices, then the other, no luck. I have tried using the IP on each physical firewall, and also no luck.
Same versions on the old and new devices. R81.20 and the same blades are active.
Still waiting on checkpoint support for an update.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What version of code was it working on and what version is it failing on?
Other than testing the L2TP client, what debug/information did you gather from the gateway?
The following SK might help in terms of debug: https://support.checkpoint.com/results/sk/sk17957
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you share logs here so we can have a look?
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the reply Andy, I spoke to my boss he doesn't want me sharing logs in an open forum unless we can make sure none of the public IP information is visible.
I will try to make sure I keep this thread updated once we have found the solution and the steps taken to resolve.
Checkpoint support are normally pretty quick, the client has pro support plus if I am not mistaken. I raised this issue on Friday, the 24th, and still no proper feedback from them. I hope its not other issues in the world causing challenges.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thats totally fair, understood. If you can share whatever possible, would help us.
Best regards,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The issue you're describing, where the client could only connect once, sounds very similar to what happens when you have your Link Selection settings set to "Main IP" when the main IP of your cluster is not the IP address your VPN will terminate on.
If you have not already, please collect a tcpdump packet capture on your gateway, filtered only for the public IP address of your L2TP client and share that alongside the debugs for TAC to review.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In case like this the client connects in Visitor mode and it disconnects after 60mins in my experience
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for your reply. We are still trying to get this resolved with the assistance of checkpoint support. We had a remote session this morning with a T3 engineer who collected some more logs wile I was attempting to connect.
I had a look on the ipsec VPN on the cluster and link selection is set "Selected address from topology table" and the public facing ip is chosen.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
One thing I would do personally is when you examine the logs collected, search for public IP of the client, as well as whatever external IP is they are connecting to and see what you can find.
Not saying that will give you clear resolution, but at least it may "steer" in the right direction.
Best regards,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you to everybody who has commented. Checkpoint Support came back to us last night, it looks like we have a mismatch in encryption.
We re added the clients 3100 to our management server after updating all the ip's to new ones as a possible alternative. Last week checkpoint support removed the device in case it was causing a conflict.
When testing we got the vpn connection but the connection to the lan was not working. After 15 minutes I then started to get a response to a ping to a local device.
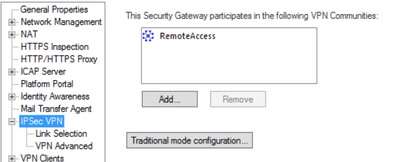
Last night I did some changes on the GW, under IPSec VPN, Traditional Mode. The bellow screen shots are from our 3100 device:
Advanced Tab
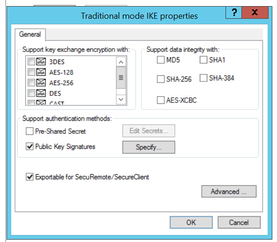
If I click okay it gives me an error "check one data integrity method", so I have clicked cancel, and if I open it again I get the same.
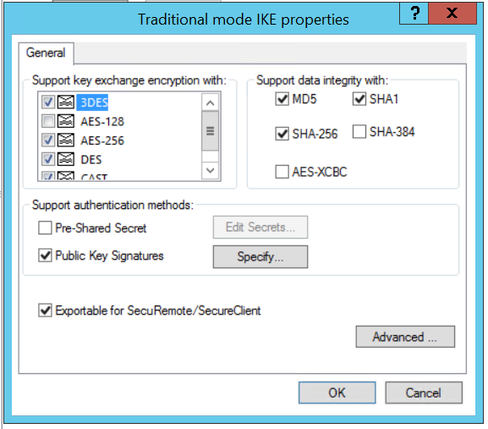
In my testing last night I cleared the traditional mode on cluster settings as they had all been ticked, then tried to set it to what windows l2pn connection wanted then matched it to what the 3100 showed as we could establish the connection to that device.
The cluster shows the following under Traditional mode IKE Properties:
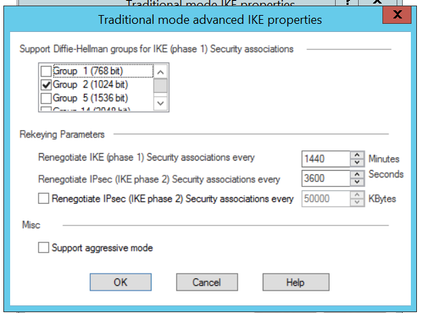
Under Advanced settings, I have only selected group 2, previously 19 and 20 where also ticked.
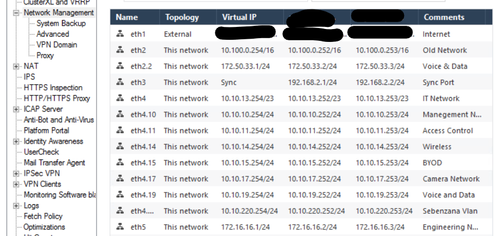
The 3600 member's had new IP Addresses assigned to their network ports and we changed the main ip address on the 3100 and unplugged it from the network when we added the virtual Ip addresses on the cluster to match the 3100 ip addresses.
The cluster virtual IP column is what we had on the 3100 device.
In my testing the vpn to the 3100 on a different public ip is working today as it always use to. The vpn to the cluster and the normal public ip does nothing. It almost looks like the policy for the Gateway settings are not applying properly. The 3100 was our main firewall, which was replaced with 2 3600 in high availability mode.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Checkpoint T3 support is still investigating the issue. In the Debug the negotiation is failing on phase2, and the other error that is seen is :
TransMatchFailure: prop# 1 propID ISAKMP trans# 1 transID 1 reason <Wrong value for: Authentication Method>
TransMatchFailure: prop# 1 propID ISAKMP trans# 2 transID 1 reason <Wrong value for: Hash Algorithm>
We getting vpn connectivity on the old 3100 no issues, but for some reason the 3600 in cluster mode is giving the above errors.
Checkpoint Support checked through out settings, and we have them set the same as the 3100.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 11 | |
| 8 | |
| 7 | |
| 7 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter