- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
Quantum SD-WAN Monitoring
Register HereCheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
MVP 2026: Submissions
Are Now Open!
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- tcpdump any interface didn't show interface in R80...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
tcpdump any interface didn't show interface in R80.40
Hello Experts,
with pre R80.40 systems I captured with
tcpdump -Penni any <pcap-filter>
and got the interface:
12:19:15.061879 Mgmt.600[out]: 10.238.1.1.22 > 10.238.0.4.52825: P 443932:444192(260) ack 1769 win 47888
12:19:15.061883 Mgmt[out]: 10.238.1.1.22 > 10.238.0.4.52825: P 443932:444192(260) ack 1769 win 47888
12:19:15.062010 Mgmt.600[out]: 10.238.1.1.22 > 10.238.0.4.52825: P 444192:444452(260) ack 1769 win 47888
12:19:15.062014 Mgmt[out]: 10.238.1.1.22 > 10.238.0.4.52825: P 444192:444452(260) ack 1769 win 47888
12:19:15.062141 Mgmt.600[out]: 10.238.1.1.22 > 10.238.0.4.52825: P 444452:444712(260) ack 1769 win 47888
12:19:15.062145 Mgmt[out]: 10.238.1.1.22 > 10.238.0.4.52825: P 444452:444712(260) ack 1769 win 47888
12:19:15.062277 Mgmt.600[out]: 10.238.1.1.22 > 10.238.0.4.52825: P 444712:444972(260) ack 1769 win 47888
With R80.40 "-P" is not possible. I used "-Q inout" but I didn't get the interfaces.
With cppcap you can get it in text output but not in capture/wireshark.
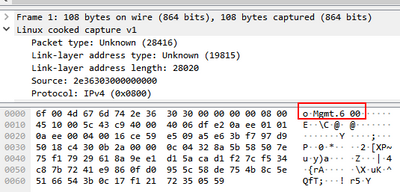
I need something like this (captured with "tcpdump -Penni any" on R80.20)
Any ideas to get interfaces in text output with tcpdump and also in capture file (for wireshark) back?
Bye
7 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As mentioned in my Max Capture class, the tcpdump 3.9.4 version bundled with Gaia 2.6.18 had the -P flag directly hacked in to the tcpdump binary by Check Point to display the interface name in CLI output.
When Gaia 3.10 was introduced the version of tcpdump was updated to version 4.9.0 and the -P hack went away with it. Will probably need to submit an RFE to get this put back in. Alternatively it looks like tcpdump version 4.9.9 now natively supports displaying the interface name in the CLI output. As a further motivator for an RFE, the tcpdump changelog (https://www.tcpdump.org/tcpdump-changes.txt) notes that literally dozens of CVE vulnerabilities were fixed in tcpdump versions 4.9.2 and 4.9.3, so perhaps R&D could just update tcpdump to 4.9.9 via Jumbo HFA and kill two birds with one stone. Tagging @PhoneBoy for R&D coordination.
As an workaround for now just use cppcap (my preferred tool) or there is the "anydump" script:
https://sebastianhaas.de/anydump-release/
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the fast answer.
If "-P" is always build in: If I start (on R80.40)
tcpdump -s0 -w file.cap -enni any host <pcap-filter>
I can't see the interface information inside Wireshark as shown in my screenshot in my first post (and also not with my preferred tool cppcap 😏).
BTW: I read you presentation and didn't got the information that "-P" is build in 😮
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can't see the interface name in Wireshark because it is not embedded in the pcap file in the first place. If doing a live capture or a replay with version 4.9.9, tcpdump can only display the interface information because it is looking at the live interface configuration of the system it is running on, and can calculate the interface name for display. If a pcap file created by tcpdump/cppcap is replayed on a different system or viewed in Wireshark, the interface name information is not supported by the pcap format at all, and is simply not available. Using the hacked-in -P option embedded the interface name into the pcap file in what I assume is an unsupported way, as seen in your screenshot. pcapng (which is still experimental) will address this by including interface name information right in the capture file.
So without the -P hack you are basically stuck, and cannot see interface information in Wireshark with pcap captures generated by cppcap/tcpdump. It would be a very interesting feature if cppcap had an option to output its captures in pcapng format (which would include interface name information embedded in the capture) instead of standard pcap format, so I'm going to tag cppcap's author @Aviad_Hadarian who also got a shout out in my 2021 CPX presentation.
As a workaround you could use fw monitor -F, which can capture accelerated traffic and has the interface name information along with capture points embedded in its capture file output in the "snoop" file format, which does support including the interface name. You'll need to set up Wireshark to display this properly as described here: sk39510: How to configure Wireshark to display Check Point FireWall chains in an FW Monitor packet. However be sure to read my stern warning in the presentation about how fw monitor -F can blast you with an unfiltered capture if you make a mistake with your filter, so double-check your filtering syntax and always use the -ci and/or -co options to automatically limit the number of packets captured by fw monitor -F just in case you do make a mistake.
I suppose you could take the older tcpdump binary from a R80.20 system and copy it over to a Gaia 3.10 system and try to run it, but that is unlikely to work and most definitely not supported.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Timothy_Hall thank you for you kind words, I don't think it too problematic to add interface names if such thing is available in libpcap, will look
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks to take a look to this. And an other RFE 😉
Can you add a fileinfo in the pcap file (as f5 does)?
This would also help TAC to interpret captures.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's Nice but will require special extension in wireshark
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm running Wireshark 3.4.3 and didn't installed any plugins (AFAIK)...
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 18 | |
| 9 | |
| 7 | |
| 6 | |
| 5 | |
| 5 | |
| 5 | |
| 5 | |
| 4 |
Upcoming Events
Thu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter