- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
The Great Exposure Reset
24 February 2026 @ 5pm CET / 11am EST
CheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Hybrid Mesh
- :
- Firewall and Security Management
- :
- Re: sync interfaces going up and down (partially u...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
sync interfaces going up and down (partially up)
Hello,
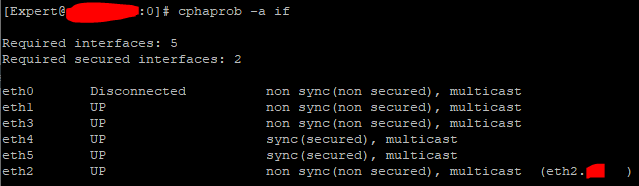
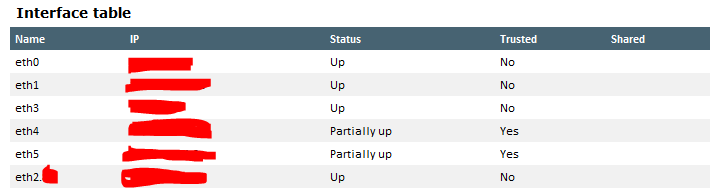
this morning I replaced one of the two nodes in HA, the new one was configured and tested in a test environment and in fact now it has no problems. the problem occurs in the two interfaces (ETH4 and 5) that deal with the sync. these keep going up and down
from the smart console are partially up
ETH4 is set as secondary in sync while ETH5 is primary.
node 1 (the old one) restarted by itself when I attacked node 2 (new) and node 1 was not restarting for a year. at this moment node 1 is running and has no problems, but due to the problems on the interfaces there is no node 2 among the members of the HA
I read that I should broadcast the network cards to solve the problem but I don't want to, as it has worked so far. the problem shouldn't be here.
any suggestion?
thanks
13 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I cant say this 100%, but I believe it was never recommended to use 2 sync interfaces. Regardless, you can try below steps. I always use to do this when someone had issues with sync in the cluster.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Which GW version is this?
Note the use of more than one dedicated physical interface for synchronization redundancy is not supported. You can use Bonding for synchronization interface redundancy.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
this configuration works since 2014, I have no idea at this point how they made it work, however, can this modification to create the bonding be done hot? taking into account that I only have a functioning node and that I can no longer afford down periods.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can do sync debug from the link I sent, hope that helps, as it should give you a clue why its failing.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Also, to add what @Chris_Atkinson said, I dont know if it says anywhere its not officially supported, but either way, all I can tell you from my experience is that I had customers run it and it does work, BUT, when it breaks, tough fixing it...its NOT an easy task, thats for sure.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For reference it's explained in the Cluster XL admin guide here:
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for that.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Backing up what Chris said here, I even mentioned in my book that adding a second physical interface as a 2nd sync is not a good idea and to use a bond instead:
Click to Expand
If you elect to add a second sync network, bond the original physical interface with
another physical interface via the Gaia web interface (or clish) and declare the new
bonded aggregate interface as “1 st Sync” in the cluster object topology settings. DO
NOT simply add a new non-bonded interface and declare it as “2nd sync” in the cluster
topology, as this setup will severely degrade cluster performance. Check
netstat -ni statistics as well for the physical sync interfaces to ensure zero values
for RX-ERR and RX-OVR.
another physical interface via the Gaia web interface (or clish) and declare the new
bonded aggregate interface as “1 st Sync” in the cluster object topology settings. DO
NOT simply add a new non-bonded interface and declare it as “2nd sync” in the cluster
topology, as this setup will severely degrade cluster performance. Check
netstat -ni statistics as well for the physical sync interfaces to ensure zero values
for RX-ERR and RX-OVR.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think I will buy your book @Timothy_Hall , one of my colleagues said he got it on Amazon and loved it :- ). Any discount code for checkmates peeps? haha
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Unfortunately I have no ability to create discount codes at Amazon for the hardcopy edition.
However discount codes for the PDF edition and the self-guided video series offerings do tend to pop up during CPX season every year so stay tuned.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just bought it on amazon, pays to be prime member : )
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The top of this SK suggests you should, except in a few unique cases, only use bonded sync interfaces if you want redundancy.
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
sk92804: Sync Redundancy in ClusterXL
CCSM R77/R80/ELITE
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 56 | |
| 44 | |
| 16 | |
| 14 | |
| 14 | |
| 11 | |
| 10 | |
| 10 | |
| 9 | |
| 8 |
Upcoming Events
Thu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 19 Feb 2026 @ 03:00 PM (EST)
Americas Deep Dive: Check Point Management API Best PracticesThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 19 Feb 2026 @ 03:00 PM (EST)
Americas Deep Dive: Check Point Management API Best PracticesAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter