- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
CheckMates Fest 2025!
Join the Biggest Event of the Year!
Simplifying Zero Trust Security
with Infinity Identity!
Operational Health Monitoring
Help us with the Short-Term Roadmap
CheckMates Go:
Recently on CheckMates
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Security Gateways
- :
- identity collector - gateway can't see user/machin...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
identity collector - gateway can't see user/machine details
Hi,
Just installed and configured Identity Collector for one of our two domains.
Everything looks fine on the IDC, I can see events and users-machines correlations.
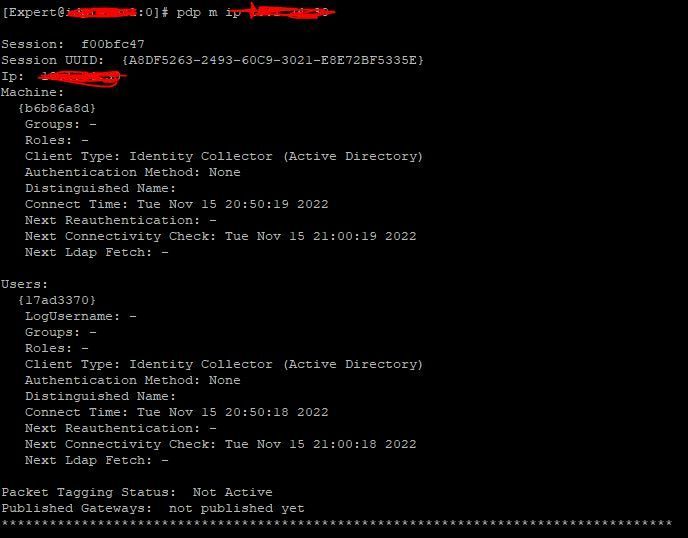
however when running pdp m ip x.x.x.x there are many details missing:
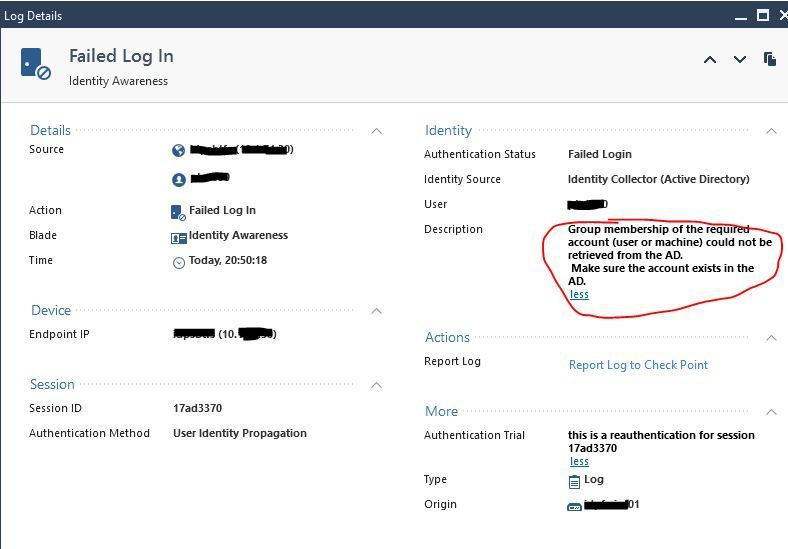
Also in SmartConsole logs I see this:
Anyone familiar with this issue?
Labels
- Labels:
-
ClusterXL
-
Gaia
-
Identity Awareness
-
Open Server
14 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
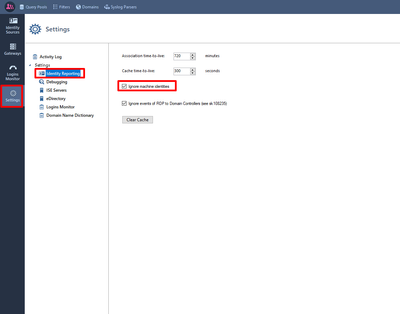
There was a recent post on similar and issue was windows firewall on IC itself, but dont believe thats problem here. Make sure below is checked as per my screenshot.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
There's no firewall on the IDC.
However, "Ignore machine identities" was not checked.
Sounds like it really should not be checked or else it would ignore the machine identity.
Also, how is this related to users not being propagated?
can you explain please?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
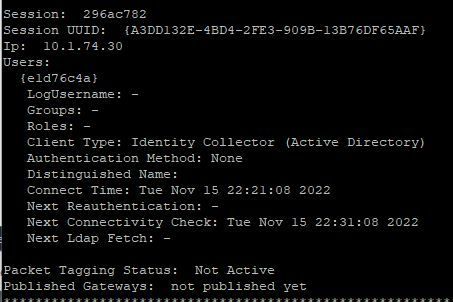
Anyway, I tried what you suggested and it didn't work.
Only now, I don't see machine details at all:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry man, my bad, I confused 2 different things. I was thinking of "log out", rather than "log in" events. For what you are after, yes, option should be unchecked, apologies.
I found below links about it, but not sure either one applies 100% to your scenario:
Let me check on my end and see what could be missing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No problem 🙂
Already went through these links, they didn't help unfortunately...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have you done any troubleshooting on the LDAP piece of this?
The groups come from an LDAP lookup from the gateway, not from Identity Collector.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The LDAP object is working fine when adquery is used. It's only when switching to IDC that it's not working.
After switching to IDC I unchecked the "AD query" option in the LDAP object, that's the only change I've made.
I rechecked the server and credentials in the LDAP and they're OK. What else can I check?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That made me remember...when you say unchecked "ad query", are you referring to actual setting on the identity awareness tab on the firewall object itself?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Both.
I've tried all combinations:
IDC + ADQuery on fiewall object
IDC without ADQuery on firewall object
IDC without ADQuery on fiewall object and on LDAP object.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So odd...I work with customer who has AD query enabled WITH IC as well and no issues at all. Mind you, I believe TAC recommends to turn off AD query if you use IC (which makes sense), but either way, it should work, 100%. Do you see any logs related to this on your AD server at all?
Below is what TAC gave me once to debug identity awareness issue, so this also might be worth a shot.
(•)•) Identity awareness debugs
# cd $FWDIR/log
# rm pdpd.elg.*
# echo "=debug_start=" >> $FWDIR/log/pdpd.elg
(•) To turn pdp debug on:
# adlog a d on
# pdp debug on
# pep debug on
# pdp debug set all all
(•) Replicate the issue
(•) To turn them off:
# adlog a d off
# pdp debug unset all all
# pdp debug off
# pep debug off
# pdp d reset
# pep d unset all all
Collect debug:
$FWDIR/log/pdpd.elg
# tar zcvf pdpd_debugs.tgz pdpd.elg*
# tar zcvf pepd_debugs.tgz pepd.elg*
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Jonathan,
Did you get this working?
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is this issue resolved? if yes, can you share the solution here, please?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi!
I had this issue. I just installed and configured the Identity Collector and missed the LDAP part.
You need to have a "LDAP Account Unit" to map usernames from Identity Collector to the Domain for the Microsoft_AD.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I do have LDAP account unit in place. For me the issue is slightly different.
The individual user authentication works fine but when I use LDAP user groups instead of individual users in Access Roles the network access doesn't work.
When I do "pdp monitor all" I can users populated and but not their associated user groups on AD.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 20 | |
| 11 | |
| 9 | |
| 6 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 3 | |
| 3 |
Upcoming Events
Thu 13 Feb 2025 @ 03:00 AM (CET)
Navigating the Cyber Frontier: A Check Point Executive Briefing - APACThu 13 Feb 2025 @ 03:00 PM (CET)
Navigating the Cyber Frontier: A Check Point Executive Briefing - EMEAThu 13 Feb 2025 @ 02:00 PM (EST)
Navigating the Cyber Frontier: A Check Point Executive Briefing - AmericasFri 14 Feb 2025 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 33: CPX 2025 terugblik!Tue 18 Feb 2025 @ 03:00 PM (CET)
Why Adding SASE to Your Network Infrastructure is a Win-Win - EMEATue 18 Feb 2025 @ 02:00 PM (EST)
Why Adding SASE to Your Network Infrastructure is a Win-Win - AMERICASThu 13 Feb 2025 @ 03:00 AM (CET)
Navigating the Cyber Frontier: A Check Point Executive Briefing - APACThu 13 Feb 2025 @ 03:00 PM (CET)
Navigating the Cyber Frontier: A Check Point Executive Briefing - EMEAThu 13 Feb 2025 @ 02:00 PM (EST)
Navigating the Cyber Frontier: A Check Point Executive Briefing - AmericasFri 14 Feb 2025 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 33: CPX 2025 terugblik!Tue 18 Feb 2025 @ 03:00 PM (CET)
Why Adding SASE to Your Network Infrastructure is a Win-Win - EMEATue 18 Feb 2025 @ 02:00 PM (EST)
Why Adding SASE to Your Network Infrastructure is a Win-Win - AMERICASAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter