- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: configure Proxy Arp on VSX cluster firewall
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
configure Proxy Arp on VSX cluster firewall
Hi Team ,
Can someone explain me how to configure Proxy Arp for Static NAT Public IP on R80.10 VSX Cluster firewall .My Cluster is active passive mode .I am go through SK30197 but not understand .
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nilesh,
ther's another way to add a proxy arp entry to a gateway without configuring via the GAiA portal or close.
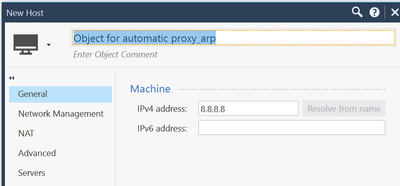
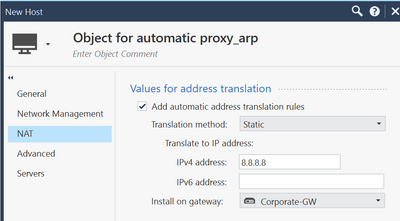
Add a host object with your external IP to your rulebase and configure automatic NAT (static). As NAT-IP use the same external IP, add the relevant gateway and do a policy install. With this host object the gateway adds an proxy arp entry to the the gateway.
Wolfgang
13 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
First thing you need to know is the mac address that is connected to the correct interface, you can find that by entering in expert mode (lets say you are working on VS5:
vsenv 5
cphaprob stat
ifconfig
From the last find the correct interface that belongs to the IP from the same network/subnet you want to add the proxy arp for.
Now go back to clish and enter the following commands:
set virtual-system 5
add arp proxy ipv4-address 10.10.10.20 macaddress 00:xx:xx:xx:xx:xx real-ipv4-address 10.10.10.1
Where 10.10.10.20 is the NAT IP you added and 10.10.10.1 is the IP on the interface. Once added push policy, but before you do, do not forget to check that the global NAT properties, 'merge manual proxy ARP configuration' is ticked.
Now check to see if it all works properly with:
fw ctl arp
vsenv 5
cphaprob stat
ifconfig
From the last find the correct interface that belongs to the IP from the same network/subnet you want to add the proxy arp for.
Now go back to clish and enter the following commands:
set virtual-system 5
add arp proxy ipv4-address 10.10.10.20 macaddress 00:xx:xx:xx:xx:xx real-ipv4-address 10.10.10.1
Where 10.10.10.20 is the NAT IP you added and 10.10.10.1 is the IP on the interface. Once added push policy, but before you do, do not forget to check that the global NAT properties, 'merge manual proxy ARP configuration' is ticked.
Now check to see if it all works properly with:
fw ctl arp
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nilesh,
ther's another way to add a proxy arp entry to a gateway without configuring via the GAiA portal or close.
Add a host object with your external IP to your rulebase and configure automatic NAT (static). As NAT-IP use the same external IP, add the relevant gateway and do a policy install. With this host object the gateway adds an proxy arp entry to the the gateway.
Wolfgang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am virtualizing a HA Cluster to a VSX Cluster and have been reading some documentation regarding PROXY ARP and VSX . One thing I would like to discuss is the relation between a proxy arp entry in clish and the local.arp file. I have to understand this better so that I can configure this in the new VSX enviroment.
This is taken from a normal HA cluster not a VSX!
local.arp - 193.45.59.11 00:1c:7f:63:e8:76 193.45.95.20
--------------------------------------------------------------------------------------------------
clish - add arp proxy ipv4-address 193.45.59.11 interface bond1 real-ipv4-address 193.45.95.20
If I have understood this post correctly I only have to add proxy arp on the vs and nothing in the local.arp file?
Sincerely
Clive Overton-Fox
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Clish commands overwrite the files in the background, like the add arp proxy will add an entry to local.arp
The main advantage of using clish instead of editing local files is that show configuration will show you that information without you needing to get into those pesky files.
Same goes for cronjobs, add cron in clish will add a line to crontab and you will see with crontab -l that the command you added in clish is properly added to the crontab.
Also in some companies you're not allowed to go into expert mode, thus making the access to local.arp very difficult.
The main advantage of using clish instead of editing local files is that show configuration will show you that information without you needing to get into those pesky files.
Same goes for cronjobs, add cron in clish will add a line to crontab and you will see with crontab -l that the command you added in clish is properly added to the crontab.
Also in some companies you're not allowed to go into expert mode, thus making the access to local.arp very difficult.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I tried this and it did not work, I ended up creating a local.arp file on the VS, I used SK30197 as reference. This was done on a R80.40 VSX cluster.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
With VSX, you must use clish to configure proxy ARP entries for VS0 (this isn't common, but it is technically possible), and you must use local.arp for proxy ARP entries for any VS other than 0.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Bob - I confirmed this with TAC today as well, I think Checkpoint should improve on this so that clish commands for proxy arp entries should also work on specific VS's (the commands are accepted).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm the other way around. I can't stand clish, and would love to go back to local.arp for all proxy ARP entries on all VSs and on non-VSX firewalls.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @Bob_Zimmerman
In a VSX cluster in VSLS mode, when you add an entry in local.arp, does it have to be done on both members of the cluster?
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Matlu yes, you have to change this on all cluster members. But you can configure "proxy arp" from Smartconsole following
Add a host object with your needed proxy arp IP to your rulebase and configure automatic NAT (static). As NAT-IP use the same external IP, add the relevant gateway and do a policy install. With this host object the gateway adds an proxy arp entry to the gateway. You can check this with "fw ctl arp" on the gateway. If the "Install on gateway" is a cluster the entry is changed on all members.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I have “encountered” a reality that differs from “best practices” in this legacy architecture.
The VS does not have any PROXY ARP entries configured with the command:
add arp proxy ipv4-address 1.2.3.4 macaddress 00:xx:xx:xx:xx:xx real-ipv4-address 190.90.90.90
And they haven't used the option to use an object from the SmartConsole either.
The only thing that makes sense is that they were previously creating PROXY ARP entries but editing the VS local.arp file.
This also works fine, right?
I mean modifying the local.arp file from the CLI.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sure @Matlu modifying local.arp in context of the VS will work, see sk30197 - Configuring Proxy ARP for Manual NAT section "Procedure for the Traditional VSX mode - context of any Virtual System, other than VS0 (VSX itself)"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
One thing to note, ensure you use the mac of the virtual interface in the VS if its the interface leading to the internet, so in affect the mac used on both nodes is the same (I've done this in R82 and it works fine)
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 17 | |
| 8 | |
| 8 | |
| 5 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter