- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: checkpoint web filtering works too slow
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
checkpoint web filtering works too slow
hello
I have Url filtering with proxy,
it'has been working very slow for 2 day , (web sites are opening very slowly) and CPU in Checkpoint has increased,
I discover this error logs , followed down , should it cause of this problem .
[ERROR]: uc_log_suppression_set_entry: Failed storing log data in log suppression table!
15 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For this error message, sk162639 suggests the following:
Contact Check Point Support for assistance with this issue.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What is the hardware of your gateway?
Are you using a separate management server or is this a standalone install?
Are you using a separate management server or is this a standalone install?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hardware -5600
i have both, Management server and gateway
now i have very big problem , URL filtering doesn't work at all , and network is too slow
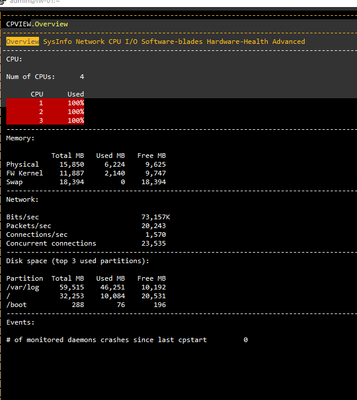
when i type this command (cpview) See it in screenshot, CPU's are always 100 % , but network traffic is very small , about 70 MB . I cannot find which process loads CPU's
CPview command
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Need to see output of top command to determine if CPU load is kernel-based or process-based, and if it is process-based top will show which processes are consuming CPU.
However being in standalone mode with 16GB of RAM and only 4 cores, it will be difficult to get good performance.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don't have big traffic .
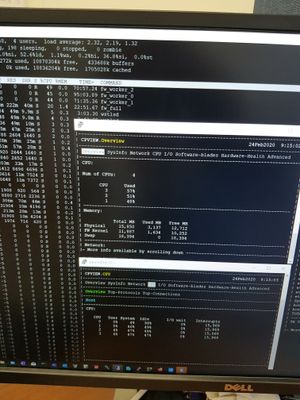
Please see screenshot . TOP shows me only this information
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Now this screenshot is taken in the morning hours and it is not loaded yet, but in 10 o,clock it was 100 % and TOP was same
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
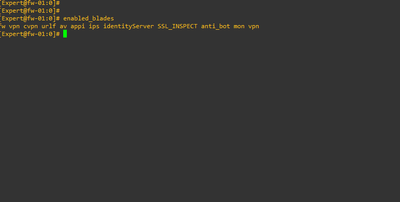
I need to see the entire screen of the top output, but it looks like you have HTTPS Inspection enabled due to the presence of the wstlsd process. Probably not advisable to use that feature on a 5600 configured in standalone mode. Also please provide output of enabled_blades command, my guess is you have most of the blades enabled.
Also are you sure this box is managed standalone and not with a separate SMS/MDS? I don't think the typical management processes are showing up in your top output.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It was working normally 2 days ago. Nothing happened , i just made install policy and after that it began increasing CPU . These are active blade . Now it is not work hours.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What version of code is this you're running?
Highly recommend getting the TAC involved here to help you sort this out.
Highly recommend getting the TAC involved here to help you sort this out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
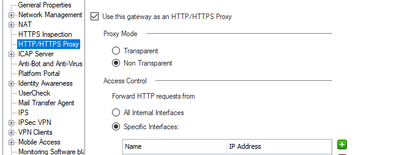
hello.
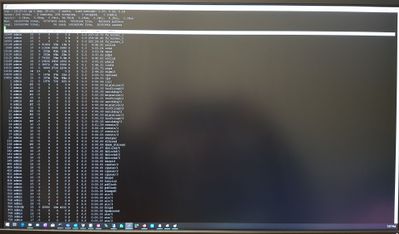
i have enabled http/https proxy , see it in screenshot.
Could this function be the reason for processor load? And is it possible to see, how many process uses this particular function?
Support said us that for testing, i should disable this function , install new proxy server in other machine (linux) , move only this function to this server, (NOT Url filtering, Url filtering should stay in checkpoint ) and then test .
For this situation All trafic come to this proxy server and then go internet via checkpoint (Url filtering ) .
version is R80.30
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I agree with TAC here, you should never enable the firewall as a HTTP/HTTPS Proxy like that as it will invoke Active Streaming in the CPASXL path in R80.20+. This is a legacy feature that should not be necessary in today's world, and was singled out for some pretty harsh words in the third edition of my book:
Click to Expand
Do not enable the firewall as a HTTP/HTTPS Proxy Server. On the firewall object is
a screen called “HTTP/HTTPS Proxy Server” that will permit the firewall to be used as a
web proxy server for web browsers. This feature is disabled by default, do not enable it!
An easy way to see if this feature is enabled is by running command ps -efw |
grep wsdnsd. If the wsdnsd daemon is running HTTP/HTTPS proxying is enabled,
and can case some various performance-impacting issues such as:
Any traffic proxied by the firewall in this way will be handled by active streaming in
the CPASXL path. If you have this option enabled it may have been turned on
mistakenly, or under the guise that the firewall configured in this way would act as a
“caching” proxy server, and reduce the utilization of an overloaded Internet connection
by providing cached responses to popular websites. WRONG. This feature does not
perform any caching of web content whatsoever, and will suck large amounts of traffic
into the CPASXL path. See the following for more information:
sk92482: Performance impact from enabling HTTP/HTTPS Proxy functionality.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Timothy,
I just looked at some firewall (R80.20 and R80.30) using the wsdnsd process.
And although I have not activated HTTP / HTTPS proxy on any firewall, the process is still active.
If I can trust the output of CPWD_admin _list. 🙂
What else could have activated this process?
PS: Your book ist awsome!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As long as you are sure the firewall is not defined as a proxy I wouldn't worry about it, wsdnsd is probably just doing DNS lookups for something else such as Dynamic Objects.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I check this in my lab.
The wsdnsd process is activated as soon as you use an updateble object in the policy.
Maybe the sk97638 need a update.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Makes sense, thanks for the followup.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 20 | |
| 19 | |
| 18 | |
| 8 | |
| 7 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter