- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: ZScaler GRE to CP Cluster
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ZScaler GRE to CP Cluster
5 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Nathan,
Thanks for providing the solution in the attached cluster guide. I have a few questions -
If a cluster is setup in an active/standby HA configuration, there is a single external VIP. This is used to provision the Zscaler GRE tunnel. Zscaler provides a /29 subnet to be used for the GRE tunnel configuration for 2 tunnels. This does not provide a configuration for 4 tunnels.
As mentioned in the guide, it mentions 2 separate tunnel configurations. Please advise if 2 public IPs were utilized on the firewall cluster. This is not clearly noted.
Also, can you share a screenshot of the SmartConsole Network Management window showing the interface configuration?
If the same GRE configuration is mirrored onto both firewalls, what issues would that present as only a single firewall will be active at any given time.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Raj,
For one of my customer i configured GRE tunnels with 2 tunnels, even if in GRE tunnel configuration you specified local address of gateway, active member will replace it by cluster VIP in GRE tunnel establishment and to encapsulate traffic.
So you can use the same local address for differents tunnels, that's what i did and it works.
Also i disagree the configurations steps regarding network topology, here is what i configured :
As Zscaler do not provide enough IP address i used the IP provided for my node as cluster VIP in topology. As local address in tunnel i used another IP address.
I declared the VIP as scopelocal route as explained in Configuring Cluster Addresses on Different Subnets (checkpoint.com)
I attach GRE tunnel configuration, scopelocal routes and the topology configured
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Guerric_LM could you please share the total configuration steps with screenshot
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
i could not provide it, it's customer configuration.
But with the 1st post and mine you should be able to configure it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Maybe this will help:
Check Point Cluster -- GRE with Zscaler:
During creation of tunnel in Zscaler you will get following info:
(just examples without real data)
Zscaler public pool: 1.1.1.1 and 2.2.2.2 ( t basing on location they recomend which dc should be used )
Zscaler Internal GRE pool: 172.25.0.0/29 ( you can choose from avaliable /29 pools) = it means that you have x2 /30 = 172.25.0.0/30 & 172.25.0.4/30
Basing on above :
primary_fw-vip_internal_peer - 172.25.0.1 ( 1st usable host)
primary_zscaler_internal_peer- 172.25.0.2
secondary_fw-vip_internal_peer - 172.25.0.5 ( 1st usable host)
secondary_zscaler_internal_peer - 172.25.0.6
Our fw data:
e.g
Fw public pool: fw-01 - 100.100.100.2 , fw-02 -100.100.100.3 , fw-vip - 100.100.100.1
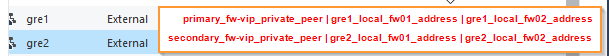
gre1_local_fw01_address & gre1_local_fw02_address - different subnet than delivered by Zscaler, only local significance
e.g 192.168.0.1/30 & 192.168.0.2/30
gre2_local_fw01_address & gre2_local_fw02_address - different subnet than delivered by Zscaler, only local significance
e.g 192.168.0.5/30 & 192.168.0.6/30
Fw-01
add gre id 1 local <pubic_fw-01_ip = 100.100.100.2 > remote <primary_public_zscaler = 1.1.1.1> ttl 255 ip <gre1_local_fw01_address = 192.168.0.1> mask 30 peer <primary_zscaler_internal_peer = 172.25.0.2 >
set interface gre1 comments "Primary GRE to Zscaler"
set interface gre1 state on
add gre id 2 local <pubic_fw-01_ip = 100.100.100.2> remote <secondary_public_zscaler = 2.2.2.2 > ttl 255 ip <gre2_local_fw01_address = 192.168.0.5> mask 30 peer <secondary_zscaler_internal_peer = 172.25.0.6>
set interface gre2 comments "Secondary GRE to Zscaler"
set interface gre2 state on
Fw-02
add gre id 1 local <pubic_fw-02_ip = 100.100.100.3> remote <primary_public_zscaler = 1.1.1.1> ttl 255 ip <gre1_local_fw02_address = 192.168.0.2> mask 30 peer <primary_zscaler_internal_peer = 172.25.0.2>
set interface gre1 comments "Primary GRE to Zscaler"
set interface gre1 state on
add gre id 2 local <pubic_fw-02_ip = 100.100.100.3> remote <secondary_public_zscaler = 2.2.2.2> ttl 255 ip <gre2_local_fw02_address = 192.168.0.6> mask 30 peer <secondary_zscaler_internal_peer = 172.25.0.6>
set interface gre2 comments "Secondary GRE to Zscaler"
set interface gre2 state on
set static-route <primary_zscaler_internal_peer_range/30 = 172.25.0.0/30> nexthop gateway logical gre1 on
set static-route <primary_zscaler_internal_peer_range/30= 172.25.0.0/30> scopelocal on
set static-route <secondary_zscaler_internal_peer_range/30 = 172.25.0.4/30> nexthop gateway logical gre2 on
set static-route <secondary_zscaler_internal_peer_range/30 = 172.25.0.4/30> scopelocal on
Scope Local
Use this setting on a Cluster Member when the cluster virtual IPv4 address is in a different subnet than the IPv4 address of a physical interface. Now the Cluster Member can accept static routes on the subnet of the cluster virtual IPv4 address.
set ip-reachability-detection ping address <primary_public_zscaler = 1.1.1.1> enable-ping on
set ip-reachability-detection ping address <secondary_public_zscaler= 2.2.2.2> enable-ping on
set pbr table GRETable static-route default nexthop gateway address <primary_zscaler_internal_peer = 172.25.0.2> priority 1
set pbr table GRETable static-route default nexthop gateway address <primary_zscaler_internal_peer = 172.25.0.2> monitored-ip <primary_public_zscaler = 1.1.1.1> on
set pbr table GRETable static-route default nexthop gateway address <primary_zscaler_internal_peer = 172.25.0.2> monitored-ip-option fail-any
set pbr table GRETable static-route default nexthop gateway address <secondary_zscaler_internal_peer = 172.25.0.6> priority 2
set pbr table GRETable static-route default nexthop gateway address <secondary_zscaler_internal_peer = 172.25.0.6> monitored-ip <secondary_public_zscaler = 2.2.2.2> on
set pbr table GRETable static-route default nexthop gateway address <secondary_zscaler_internal_peer = 172.25.0.6> monitored-ip-option fail-any
Get topology:
Nat:
From fw-01_public = 100.100.100.2 and fw-02_public = 100.100.100.3 do a source nat 100.100.100.1 toward zscaler 1.1.1.1 & 2.2.2.2
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 18 | |
| 17 | |
| 8 | |
| 8 | |
| 5 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter