- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: What are the implications of setting an interf...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
What are the implications of setting an interface as "management interface" ?
Hey Guys,
what are the exact implications of setting an interface as "management interface" ? For example, are the number of queues for the management interface somehow limited?
Cheers
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There are a couple of aspects to what the management interface definition actually does, let's cover the Multi-Queue side first.
In regards to Multi-Queue and the management interface, it was impossible to enable Multi-Queue on the defined management interface in the Gaia 3.10 FCS (First Customer Ship) edition of R80.30 and the FCS of R80.40 (which uses Gaia 3.10). The explanation I got from R&D is that they wanted to ensure management access to the box even if some kind of Multi-Queue failure occurred, as MQ is enabled by default on all interfaces that support it under Gaia 3.10 except the management interface.
This restriction was lifted in Gaia 3.10 R80.30 Jumbo HFA Take 219+ and R80.40 Jumbo HFA Take 78+. In R81+ FCS MQ is enabled by default on all interfaces that support it. I'm not exactly sure what happens to the MQ status of the management interface if you started with an older Jumbo HFA or FCS and cross the boundary into where MQ is supported on the management interface, I believe it does get automatically enabled.
Be warned however that it is not a good idea to manually mess around with MQ's state on the various interfaces under Gaia 3.10 as you can end up with various issues such as sk168498: High rate of input discards after reboot when Multi-Queue is configured and sk167200: Multi-queue state is "off" when changing the management interface.
The other aspect to the management interface definition independent of Multi-Queue is what the definition means to the Gaia OS:
- The defined management interface will have it's IP mapped to the firewall's hostname in the /etc/hosts file generated at Gaia boot. Elements of the Gaia OS (not Check Point Product code) that need to determine what the main IP is they should use for various purposes will look here.
- Trying to change the IP address of the management interface in the Gaia web interface will throw a warning cautioning that completing this change may cut off your administrative access.
That's about it as far as I know, if I missed any other impacts I'd love to hear about it. The management interface definition does not impact or restrict your ability to "manage" the Gaia OS with SSH or HTTPS on any interface, as long as the firewall policy and the Gaia "Authorized Hosts" definitions (clish command add allowed-hosts) permit it. As far as which interface to choose as the management interface, I did provide some guidance on this in my Gaia 3.10 Immersion video course; here are the relevant pages:
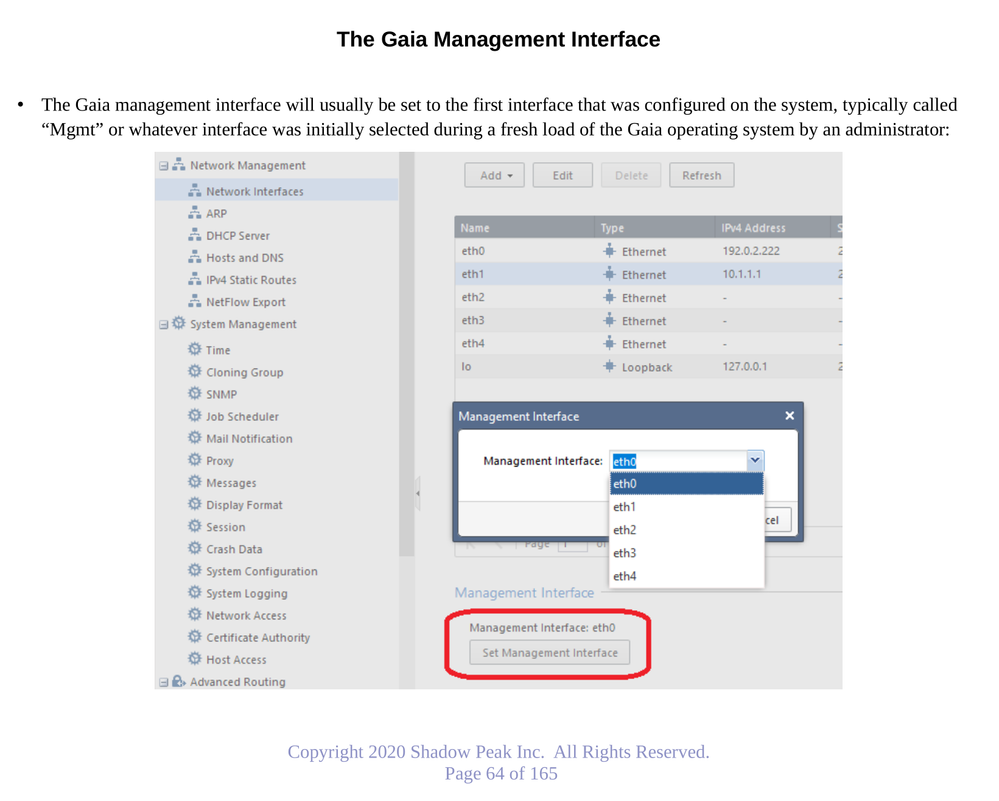
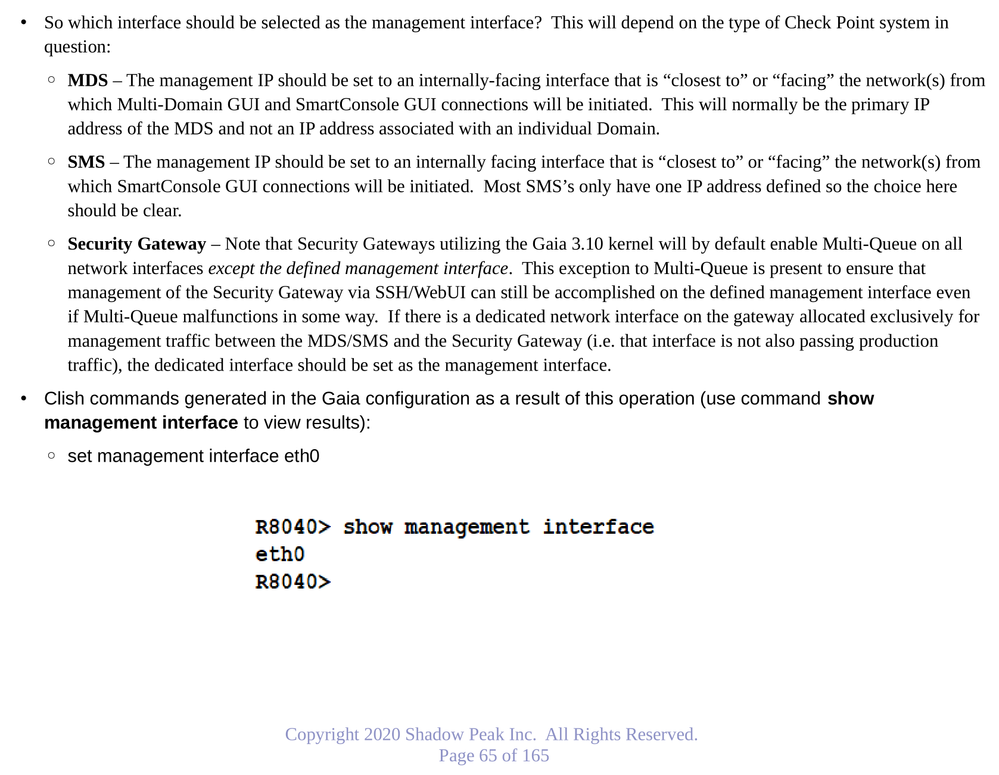
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
8 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There are a couple of aspects to what the management interface definition actually does, let's cover the Multi-Queue side first.
In regards to Multi-Queue and the management interface, it was impossible to enable Multi-Queue on the defined management interface in the Gaia 3.10 FCS (First Customer Ship) edition of R80.30 and the FCS of R80.40 (which uses Gaia 3.10). The explanation I got from R&D is that they wanted to ensure management access to the box even if some kind of Multi-Queue failure occurred, as MQ is enabled by default on all interfaces that support it under Gaia 3.10 except the management interface.
This restriction was lifted in Gaia 3.10 R80.30 Jumbo HFA Take 219+ and R80.40 Jumbo HFA Take 78+. In R81+ FCS MQ is enabled by default on all interfaces that support it. I'm not exactly sure what happens to the MQ status of the management interface if you started with an older Jumbo HFA or FCS and cross the boundary into where MQ is supported on the management interface, I believe it does get automatically enabled.
Be warned however that it is not a good idea to manually mess around with MQ's state on the various interfaces under Gaia 3.10 as you can end up with various issues such as sk168498: High rate of input discards after reboot when Multi-Queue is configured and sk167200: Multi-queue state is "off" when changing the management interface.
The other aspect to the management interface definition independent of Multi-Queue is what the definition means to the Gaia OS:
- The defined management interface will have it's IP mapped to the firewall's hostname in the /etc/hosts file generated at Gaia boot. Elements of the Gaia OS (not Check Point Product code) that need to determine what the main IP is they should use for various purposes will look here.
- Trying to change the IP address of the management interface in the Gaia web interface will throw a warning cautioning that completing this change may cut off your administrative access.
That's about it as far as I know, if I missed any other impacts I'd love to hear about it. The management interface definition does not impact or restrict your ability to "manage" the Gaia OS with SSH or HTTPS on any interface, as long as the firewall policy and the Gaia "Authorized Hosts" definitions (clish command add allowed-hosts) permit it. As far as which interface to choose as the management interface, I did provide some guidance on this in my Gaia 3.10 Immersion video course; here are the relevant pages:


Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This setting might also impact if the gateway tries to connect to the SMS via NAT IP or not, see https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
Quote: "The Security Gateway sends logs to the Security Management NATed IP because the Management's server private IP is found on the "Management" interface of the NAT-enforcing Gateway, and only hosts with IP's from the network behind the "Management" interface are allowed to connect to the Management server private IP.
Since the Gateway IP is not in range of the "Management" interface, the Gateway connects to the Management server via the NATed IP."
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Always kind of wondered how the gateway decided whether to use the SMS's NAT address or real address for sending logs, thanks for this.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am having trouble visualizing this. From what I am reading, it seems that:
1. both management interfaces, the one of SMS and the one of the gateway are on the same network.
2. SMS object defined with public IP in its NAT properties.
3. the last sentence: "Since the Gateway IP is not in range of the "Management" interface, the Gateway connects to the Management server via the NATed IP." does not make sense to me, because of the preceding statement "Management's server private IP is found on the "Management" interface of the NAT-enforcing Gateway".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hopefully someone from Checkpoint can clarify, I'm not sure if this info is still relevant myself.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I also would like for someone from Check Point to clarify.
The only scenario where that description may be applicable, (stretching our imagination), is if there is an L3 routing hop between SMS and the Management interface of the gateway performing NAT for SMS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm pretty sure the IP that will be used here is the main IP of the management object in SmartConsole.
Which...may or may not be the interface marked as management.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Fair point, but even in this case, I do not see why the logs would be forwarded to a different interface, unless there is a routing issue.
I've used some fancy routing setup on virtual SMS long time ago, advertising its local loop address (used as its main IP as well as management interface) through different virtual interfaces via OSPF, but did not see any issues described in sk171665.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 17 | |
| 9 | |
| 8 | |
| 4 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


