Hello everyone! I am learning VSX and trying to make my first lab for it.
I want to try to implement the following configuration (I drew a picture for clarification):
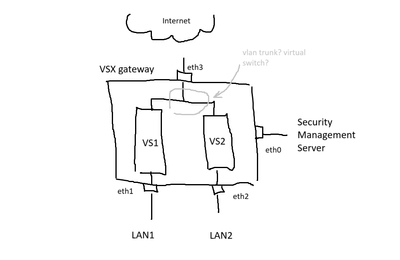
A vsx gateway with physical interfaces eth0, eth1, eth2, eth3.
There are two virtual systems vs1 and vs2 on the gateway.
eth0 is the interface leading to the management server, which is not accessible to the virtual systems.
eth3 is the interface leading to the internet, accessible to both the vsx gateway and the virtual systems.
eth1 is the interface leading to LAN 1 via vs1.
eth2 is the interface leading to LAN 2 via vs2.
Virtual systems are not a cluster, as they lead to different local networks.
I tried to configure this several times, but I had problems.
The first problem. I have created windows machines in the lan1 and lan2 networks to check the functionality of the gateway. However, for some reason there is no ping from these win machines to the relevant vs.
The second problem, which causes the most questions. I don't know how to properly configure the interface leading to the Internet for use by both virtual systems. I've tried different methods, tried creating a virtual switch, tried without it. I even began to doubt whether such a configuration is workable.
Does anyone know if it is possible to work with such a scheme? If so, how to configure it correctly? I would be grateful for any help!