- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
What's New in R82.10?
10 December @ 5pm CET / 11am ET
Improve Your Security Posture with
Threat Prevention and Policy Insights
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- VSX and VS in different domains ?
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
VSX and VS in different domains ?
Hello All,
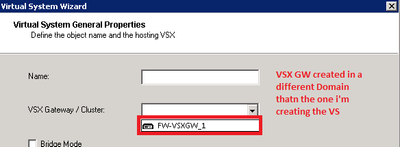
I've read somewhere, that would be possible to have a VSX Gateway inside a specific Domain (MDM environment) and create VS from that VSX Gateway in different Domains.
Is this something feasible ?
Inside the domain where i want to create the VS, i can see the VSX Gateways that reside in different domains, so i would guess its possible.
Is this something that someone already tried ?
Pros/Cons would be grateful.
Thanks in advance !
Bruno Petrónio
13 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If the VSX is managed from a MDS setup then far as I'm aware the VSX appliances should be managed via the main domain, in this way this can then be seen by customer domains.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Main Domain, implies that only one Domain could have the VSX Gateway ?
If i need 2 VSX Gateway (not cluster), is it possible/make sense to have it in different domains ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The short explanation is this is how VSX and Provider-1 are meant to be used together in a managed service provider context. You, the service provider, own the MDS and the VSX chassis. You then provision a Customer Management Add-on for the customer, and a VS (or several) to go with it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for clarifying that.
We are not running different customers, but have business related needs and we are running VSX for the virtualization fun/benefits 🙂
Saying that, make sense to have VSXs together in one domain and all VSs spread by different Domains, right ?
No Pros having VSX and VSs per Domain, i would say.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As stated already one reason was separation in provider/customer scenario.
But this was also a best practice to have a separate domain for the VSX gateways, as changes to a VS also locked the domain of VSX gateway (before R80) and so you separated it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We have many VSX and their vs separated in different CMA. I don't really see a disadvantage of doing that if there is a need to do so.
and now to something completely different - CCVS, CCAS, CCTE, CCCS, CCSM elite
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You mean, many VSX in one domain (called main domain), and their VS inside the several other domains ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I've written something on this subject some time ago for R77.30
Perhaps you'd find it useful.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, we have several VSX one domain and their VS inside several other domains. We really have some vsx in a domain called main but several others in different domains.
and now to something completely different - CCVS, CCAS, CCTE, CCCS, CCSM elite
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I believe VSX clusters in the main domain can be shared with other CMAs. VSX Clusters controlled by a customer CMA, are only usable within that domain and not visible to other customer domains.
If you decided to implement a global level VPN then having a mixed installation may not work (Never done this but thought its worth considering if you ever intended to use this feature in MDS).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, how we can verify that a domain is the "main"?
Also the "virtual switch" can be shared with two or more CMA?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm not sure what you mean by "main". I would translate that to "the DMS that should have the VSX appliances and the virtual switches". However all depends on your setup.
In general I would say the first DMS created is where the VSX appliance should be managed. The virtual switches would be created here and would then be available for other DMS's to use.
Now keep in mind the DMS that controls the _VSX policy would generally be where you manage you VSX platform from.
HOST POLICY DATE
localhost POLICY_VSX 1Apr2023 22:39:44 : [>bond1] [<bond1] [>bond2] [<bond2]
Additionally you could have other VSX appliances controlled from Customer DMS, but they would be totally isolated to that customer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, OK, thanks a lot. Your explanation is clear.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 26 | |
| 19 | |
| 11 | |
| 8 | |
| 6 | |
| 6 | |
| 5 | |
| 5 | |
| 5 | |
| 4 |
Upcoming Events
Wed 03 Dec 2025 @ 10:00 AM (COT)
Última Sesión del Año – CheckMates LATAM: ERM & TEM con ExpertosThu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasWed 03 Dec 2025 @ 10:00 AM (COT)
Última Sesión del Año – CheckMates LATAM: ERM & TEM con ExpertosThu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter