- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
CheckMates Fest 2025!
Join the Biggest Event of the Year!
Simplifying Zero Trust Security
with Infinity Identity!
Operational Health Monitoring
Help us with the Short-Term Roadmap
CheckMates Go:
Recently on CheckMates
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Security Gateways
- :
- Re: VPN tunnel latency with AWS
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
VPN tunnel latency with AWS
Hello everybody!
How are you doing?
I am writing to you because we are having a latency problem against one of the VPNs that are created against an AWS platform.
On our side we have two VTI interfaces configured and the connections are made through an Internet link.
The current version of Gaia is R80.30.
The problem is that we see that the transfers made over this VPN have a limit of between 1.5 Mbps and 3.5 Mbps. In view of this, some files are reported to be lost due to timeouts or excessive slowness when transferring certain files.
We checked the connections with the CPView tool but found nothing unusual.
Do you have any idea what it could be? Or what could we check?
Thank you very much, we wanted to know this, before opening a case with TAC.
Regardss to al!
Labels
11 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R80.30 is no longer supported and you should consider upgrading to R81.10 / R81.20.
With that said could you please confirm some elements for context?
- Configured MTU value
- MSS clamping enabled y/n
- Jumbo version
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Chris.
How are you doing?
Thank you for your reply.
Yes, we know, we still have the update pending, we had to do a rollback due to a problem when upgrading.
The jumbo currently installed is 251.
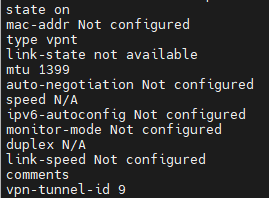
The configured MTU is 1500 on both VTIs.
We check that the MSS is enabled, through the following command #fw_clamp_vpn_mss
Thank you very much for your response.
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Let me clarify.
The previous command I mentioned returned a value of 1 as enabled, however when I ran the following command the result was 0
command: #fw ctl get int fw_clamp_tcp_mss
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There can be other causes but AWS typically mandated changes to the tunnel MTU & MSS please refer sk108958.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
AWS generated config file states MTU should be set at 1399 and recommends enabling MSS Clamping. I have many S2S against AWS and things have been running smooth.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thats an excellent point...I mostly dealt with Azure VPN tunnels and IM sure same sort of file is generated on AWS as well.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi guys.
While trying to do a tracepath we could detect the following error related to the mtu when running in another shell window a debug in parallel.
I share with you the output of the command.
fw_log_drop_ex: Packet proto=17 x.x.x.x.x -> x.x.x.x.x dropped by fwlinux_nfipout Reason: packet with IP_DF larger than MTU;
Considering this error, do you recommend changing the MTU on both ends? The 2 VTI and also on the VPC side? On both ends it is 1500.
Thank you very much.
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If AWS config file shows you certain value, as @Zolocofxp mentioned yesterday, then thats most logical value you should use, so it matches on both ends.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I agree with @Chris_Atkinson 100%. Version aside, even if you were on R81.20 and had same problem, I would also say to check the same things Chris mentioned.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
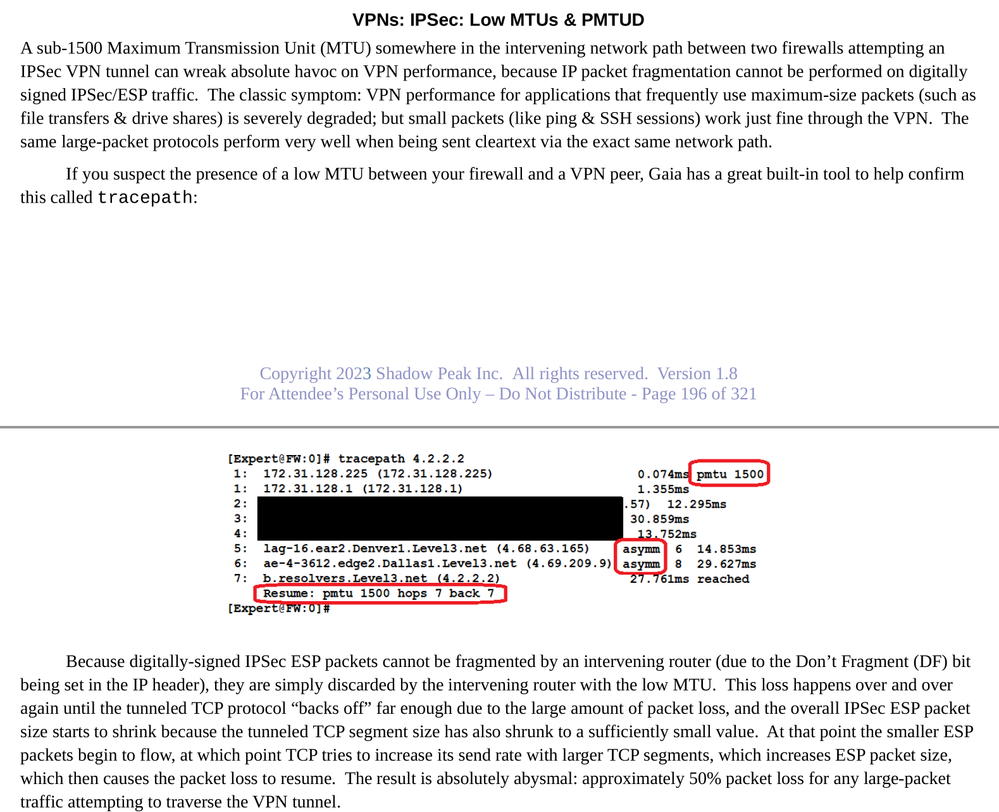
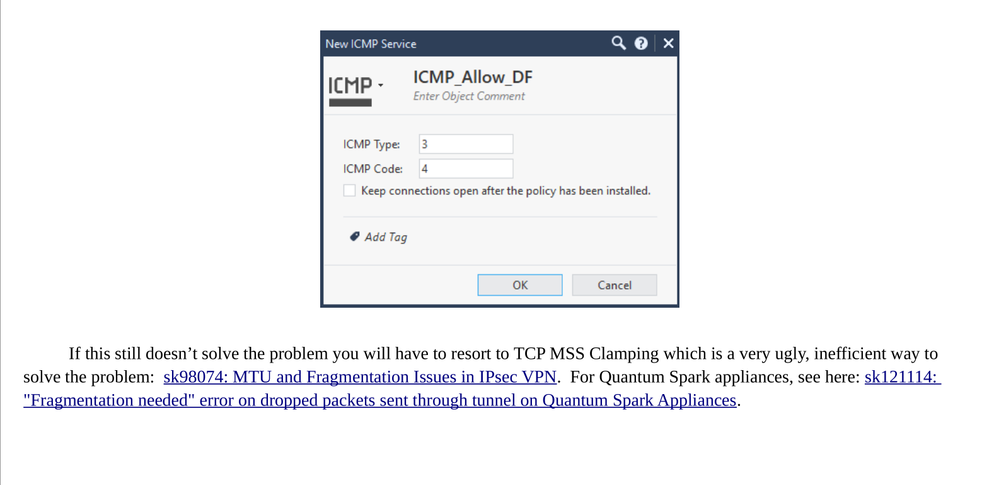
Almost certainly a sub-1500 MTU somewhere in the network path as Chris mentioned. This is covered in my Gateway Performance Optimization Course, here is the relevant content:
Gateway Performance Optimization R81.20 Course
now available at maxpowerfirewalls.com
now available at maxpowerfirewalls.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Timothy.
How are you doing?
Nice to meet you.
Thank you very much for your answer and detailed explanation, it is very useful for us to better understand this latency problem.
We will try the solution proposed in the materials you shared with us to validate that it fits our issue and to solve it.
Again thank you very much for your response.
We will let you know the results soon.
Thank you very much for your reply.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 30 | |
| 15 | |
| 11 | |
| 10 | |
| 7 | |
| 5 | |
| 4 | |
| 4 | |
| 3 | |
| 2 |
Upcoming Events
Tue 21 Jan 2025 @ 04:00 PM (CET)
Boosting Network Performance with New R82 Software and AI-Powered Gateways - EMEATue 21 Jan 2025 @ 03:00 PM (EST)
Boosting Network Performance with New R82 Software and AI-Powered Gateways - AmericasThu 23 Jan 2025 @ 10:00 AM (CET)
Enhancing Cyber Resilience with Check Point Security Operation (SecOps) Services (EMEA)Tue 21 Jan 2025 @ 04:00 PM (CET)
Boosting Network Performance with New R82 Software and AI-Powered Gateways - EMEATue 21 Jan 2025 @ 03:00 PM (EST)
Boosting Network Performance with New R82 Software and AI-Powered Gateways - AmericasThu 23 Jan 2025 @ 10:00 AM (CET)
Enhancing Cyber Resilience with Check Point Security Operation (SecOps) Services (EMEA)About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter