- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- VPN performance on a 3800
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
VPN performance on a 3800
Dear community,
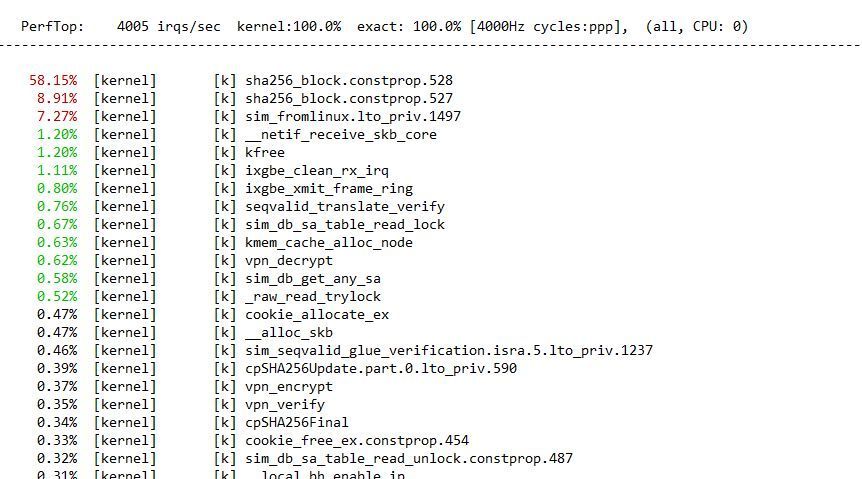
I am currently investigating an issue on a CPSG 3800 cluster running only S2S vpns. Throughput is limited to roundabout 300 Mbps because CPU 0 is contantly at 100% load. Besides normal SND tasks, there is the process show below which is causing the load:
Does any of you had similar issues and a solution?
Cheers,
Michael
54 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
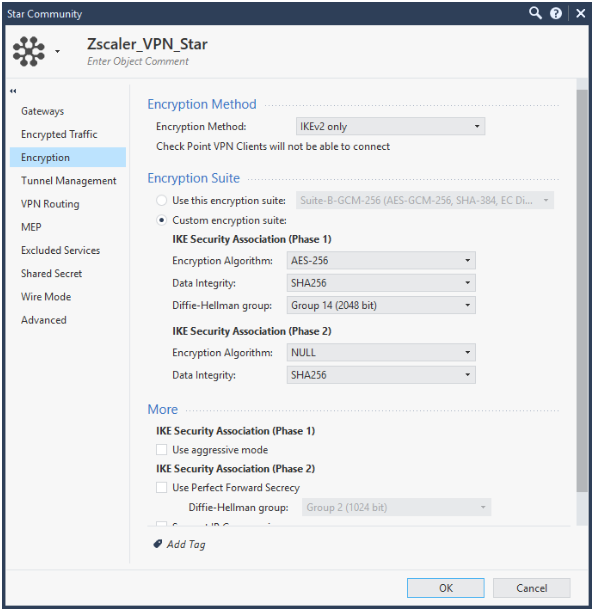
Question was: why did you use sha256 in P2 ? sk174848 has MD5...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Screenshot from sk174848...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Seems to me you did everything exactly right.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Update: Traffic limit now at ~800 Mbps with SHA1 hashing. Customer still not satisfied (me neither). Still only one core at 100%, others are ~90% idle.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey @dj0Nz
Just wondering, that screenshot you sent, is that AFTER TAC asked you to follow sk174848?
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Andy,
we didn't ask TAC as we configured the VPN but we were following the sk you mentioned...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Keep us posted, super interested how this gets solved.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you please clarify how many SND are currently set/allocated?
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Currently, there are 3 SND cores and 5 workers with dynamic balancing activated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I assume that CPU 0 is your SND? How many you have? The other cores are FWK's?
For me it looks good , the performance. You pull the traffic via one CPU only, as I can see. I think the datasheet speed is for when more then 1 CPU is used. I have never seen 1 CPU carry all the speed that is specified in the datasheet.
-------
Please press "Accept as Solution" if my post solved it 🙂
Please press "Accept as Solution" if my post solved it 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
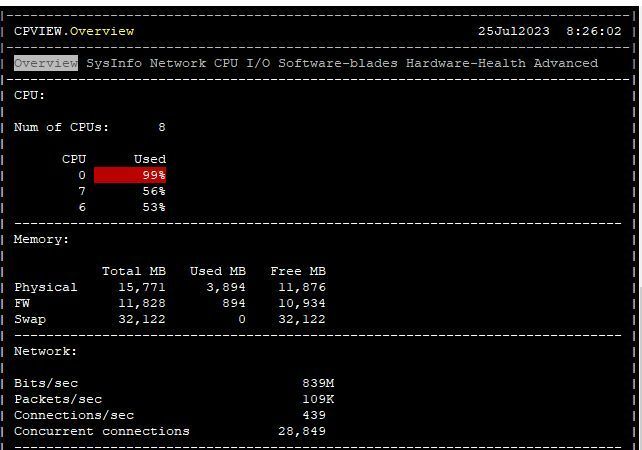
Yes, CPU 0 is one of three SND cores.
But for the customer, this doesn't look good because the machine is specified with 2.75 Gbps of IPSEC traffic and he doesn't care how many CPUs are involved.
As a technician, I know that the CPUs used in this box are low end Atoms and I would not expect more than the ~800 Mbps we reached today but customer is right here.
Who would accept a glass of water if he ordered a pint of ale?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think this is not a technical issue anymore, more customer expectation.
Now you pull the traffic via one SND and get the performance you should get.
-------
Please press "Accept as Solution" if my post solved it 🙂
Please press "Accept as Solution" if my post solved it 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Only other thing I'll add is that the new Hyperflow/pipelining feature in R81.20 requires 8+ cores be present on a Check Point appliance. All current Check Point appliances with 8 or more cores support Hyperflow, *except* the 3800 which sk178070 states is explicitly not supported even though it has the minimum 8 cores. Hmm...
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hyperflow is for the deeper inspection (traffic on the FWK). This traffic goes via the SND.
-------
Please press "Accept as Solution" if my post solved it 🙂
Please press "Accept as Solution" if my post solved it 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Correct, but the point is that it has 8 cores yet can't support Hyperflow? What is different about those 8 cores on an 3800 vs another appliance?
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This model uses older CPU's.
For topic starter here is more background information.
Topic has been discussed here: https://community.checkpoint.com/t5/Security-Gateways/Check-Point-CPAP-SG3800-and-expected-performan...
And here:
-------
Please press "Accept as Solution" if my post solved it 🙂
Please press "Accept as Solution" if my post solved it 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The 15600 uses two Xeon E5-2630 v3 processors, which were introduced in 2014q3 and which has since been discontinued. It supports HyperFlow. The 3800 uses an Atom C3758 processor, which was introduced in 2017q3 and which is still being manufactured. It does not support HyperFlow. This isn't about the age of the processor.
My bet is it's down to the TDP. At 25W with no turbo boost, the C3758 is one of the lowest-power eight-core amd64 processors available. Even eight-core laptop chips generally have double the TDP. Per-core TDP strongly correlates to per-core performance. It probably just isn't fast enough for HyperFlow to provide a good experience.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As stated by @Lesley, this model uses older Atom CPU, which lacks certain optimizations. Supporting it is currently under evaluation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Okay problem is finally "solved": Check Point provided a POC hardware (6400) with better CPUs but lower VPN throughput according to datasheet. But single thread performance matters in this case. Bandwidth is now at interface maximum (1 Gbps) with CPU 0 load at about 30%.
Conclusion: Either "someone" fixes the datasheets or performance figures must be divided by ten...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don't believe our datasheets include VPN performance numbers at present.
For specific guidance on that, you will need to reach out to your Check Point SE.
Having said that, R81.20 should have significantly better VPN performance:
- Scalable VPN performance - 3 times faster to process simultaneous Remote Access and Site to Site VPN connections.
- Major performance and stability improvement for Remote Access VPN and Site to Site VPN that delivers a significantly greater capacity for VPN tunnels.
- Extended Security Gateway certificate validation capabilities for quicker authentication.
- Resilient VPN architecture - multi-process architecture to handle IKE negotiations in dedicated scalable daemons, providing unprecedented resiliency.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@PhoneBoy wrote:I don't believe our datasheets include VPN performance numbers at present.[...]
Are you certain? I was under the impression that on page 3 of each appliances' Data Sheets under Specifications / Performance / RFC 3511, 2544, 2647, 1242 Performance (Lab), there is clearly a line specifying "VPN AES-128 (Gbps)" followed by a numeric figure. If that is not VPN perfromance numbers, then I do now know what is.
Obviously (for an experienced firewall admin) you won't get those figures unless under VERY specific conditions, but barely getting 10% of that figure IS a problem.
I also agree that NULL encryption might throw a wrench in the VPN stack's mechanism, but it does appear as if the 3xxx series may have some serious throughput issues, due to some form of software failure.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here is something that most people may not even realize...numbers you see on data sheet for any appliance for any vendor really (not only CP) are NOT what is even close to reality. Those numbers are usually only true if you dont enable any additional blades and say for VPN, since you need to have vpn blade on, you leave everything else by default.
It does not even take into account creating super basic security rules.
That is 100% the truth.
Best,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Agree with The Rock here, the published VPN number also will not be anywhere close to achievable with a single VPN tunnel. VPN handling is to some degree multi-core (sk118097) and can be spread around, but everything going through a single VPN tunnel is more or less limited to the speed of one processor for inspection and another processor for encryption/decryption. Hyperflow/pipelining (which allows potentially many cores to handle/inspect the packets of a single connection in R81.20) does not apply to VPN traffic operations.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not to sound ironic now, but I will tell you a quick story, maybe not the best comparison, but you will get an idea. When I bought my Mazda 6 back in the day, guy was showing me all the bells and whistles on it and he goes "As you can see, it has an amazing fuel efficiency, 100kms highway on 6.1 litres" and I said to him "Come on, we all know thats nonsense, no offence" and his face turned a different color lol
He knew I was 100% right, but its a "script" they have to go by. Then, few years later, I was in Japan, met with a guy who lived there (we used to work for same company), told him the same story, he took me to one Mazda dealership in Tokyo and we saw EXACT same Mazda 6 car, year and model and he translated for me what it says in fuel efficiency and bam, it showed 100 km highway driving and you spend 8.45 litres.
But then again, thats Japanese culture, they are ALWAYS 100% honest and would never exaggerate or inflate anything, no matter how small or big it might be.
Anyway, food for thought as they say..
Best,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Those numbers occur only under ideal testing conditions and with the specific encryption settings specified.
Some settings benefit from hardware acceleration in the CPU, others do not.
This can make a significant difference in observed performance.
- « Previous
-
- 1
- 2
- Next »
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 23 | |
| 17 | |
| 11 | |
| 8 | |
| 7 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter