- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
CheckMates Fest 2025!
Join the Biggest Event of the Year!
Simplifying Zero Trust Security
with Infinity Identity!
Operational Health Monitoring
Help us with the Short-Term Roadmap
CheckMates Go:
Recently on CheckMates
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Security Gateways
- :
- Re: VPN Tunnel to Cisco ASA doesn't work
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
VPN Tunnel to Cisco ASA doesn't work
Hello,
We’ve setup a VPN tunnel from our Check Point DC firewall to a Cisco ASA firewall in Australia but it doesn’t work. In logs (and IKEView), we see: Auth exchange: Received notification from peer: Traffic selectors unacceptable MyTSi: <IPv4 Universal Range> MyTSr: <My Peer's public IP>.
We’ve tried what is proposed in sk157473 but no luck.
IKEView (legacy_ikev2.xmll), during authentication, Check Point proposes "IPv4 Universal Range" as its own traffic selector and the IP of the peer as TS for the peer but ASA refuses this in its response. Why doesn't Check Point propose its own public IP as TS ?
Can you help us find the issue?
Thanks in advance for your help.
Regards,
Alain
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey @Leader_Kiongi
See if you can do changes I proposed in below link to Rich. Let us know if that helps.
Andy
22 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Tried sk108600: VPN Site-to-Site with 3rd party yet ?
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @G_W_Albrecht . Yes I already had a look at sk108600 but I don't see any scenario similar to my issue.
Regards,
Alain
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Better contact TAC to get this resolved asap !
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes already opened a ticket with our partner, we don't have direct support with Check Point. But no feedback from them yet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey @Leader_Kiongi
See if you can do changes I proposed in below link to Rich. Let us know if that helps.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @the_rock for your feedback. I could only change ike_p2_enable_supernet_from_R80.20, which can be changed on community basis. ike_enable_supernet and ike_use_largest_possible_subnets are global properties and changing those would have a huge impact on the VPN tunnels that are already working. The thing is that we have many other working tunnels with 3rd parties (Cisco, Fortinet etc...) with those settings set to true. Really don't understand.
Thanks !
Regards,
Alain
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No worries, I understand. I will tell you I had people change those many times before without any issues. Btw, those values should be set to FALSE to begin with. But, keep us posted on what TAC says.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @the_rock ,
I made the changes, pushed policy and reset the tunnel but still the same error. Something curious is that the tunnel shows as up in SmartView Monitor but ping doesn't work and in SmartConsole and IKEView I see the error "Traffic selectors unacceptable". Check Point still proposes "IPv4 Universal Range" as Traffic Selector, which is rejected by the ASA.
Any idea ?
Thanks !
Regards,
Alain IKULA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
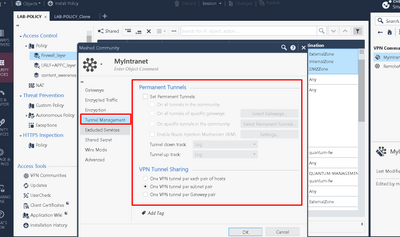
How do you have tunnel management tab configured inside vpn community on CP side? Can you send a screenshot please? That message tells me it does not like something about phase 2 config.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@the_rock Andy is on the right way. The problem looks like related to tunnel management settings. Check your settings (subnet pair or gateway pair or host pair) The same must be defined on the Cisco ASA site, this is a common mistake.
Have a look at Site to Site using IKEv2 fails with "None of the traffic selectors match the conection
Is the ASA object configured as interoperable device ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thats honestly the only thing left that makes sense to me. @Leader_Kiongi , here is the best Cisco vpn debug commands I got while back from the guy who used to work in Cisco TAC. If you can have them run this, should give better insight as well.
Andy
debug vpn:
debug crypto condition peer x.x.x.x
debug crypto ikev1 200
debug crypto ipsec 200
to cancel all debugs-> undebug all
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @Wolfgang @ . Unfortunately, I already tried all tunnel management options (host pair, network pair and gateway pair) but still the same result. Check Point keeps proposing "IPv4 Universal Range" as Traffic Selector, but ASA refuses it. Yes I already had a look at sk157473 and yes Cisco ASA is configured as interoperable device
Thanks !
Regards,
Alain
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Now i am not sure which steps you already have taken or what Check Point version you are running but
there are some things i would try in an effort to rule out some issues.
IKE Version, are running v1 or v2 in the community ? Possible to switch and test ?
IPv4 summarization, Check Point fw is going to try to summarize the networks in the encryption domain which will cause issues if the other end has 2 /24's for example and Check Point is presenting a /23.
Are there more VPN tunnels to this Check Point endpoint ? Have you considered trying to use "Encryption Domain per Community"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @svori . We're using IKEv2. Already tested with IKEv1 but same issue. What's curious is that same settings are being used with another Check Point in Azure and it works. The only difference here is that my encryption domain is a test encryption domain with three /32 networks.
IPv4 summarization has been disabled by switching those 3 settings to FALSE using GUIDBedit:
ike_enable_supernet
ike_p2_enable_supernet_from_R80.20
ike_use_largest_possible_subnets
I'm hopeless. No feedback yet from TAC.
Thanks !
Regards,
Alain
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How is tunnel management configured? Can you send a screenshot please? I referenced to it yesterday : - )
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @the_rock. Here you are:
Since around 01.00 PM, tunnel is up, though ping still doesn't work. My colleagues in Australia need to check if they see my incoming ping and maybe firewall rule is missing but traffic is now successfully encrypted in the tunnel. I think the change you proposed here https://community.checkpoint.com/t5/Security-Gateways/Site-to-site-Disconnects-amp-Questions/m-p/175... made the trick. We still have to confirm with colleagues in Australia on Monday. I'll keep you posted.
Thanks a lot guys for your support. This community is incredible
Regards,
Alain
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Leader_Kiongi Glad we can help mate, its always team effort on here! Funny story...one time, I was on the phone with TAC guy and the customer (customer I know very well personally) and TAC guy sends us a link and he goes "Here is the link I found, this is the guy called rock on community and I think he knows lots of stuff" and customer says to him "Hm, yea, I always wonder who that dude is" and it took support guy few minutes to figure out it was me HAHAHA
We all laughed about it later, it was sort of funny lol
Though as I said in the post you referenced, I had been know to fix some issues here and there in last 15 years, but nothing like community legend @PhoneBoy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is really funny. I'll mark as solution if our Australian colleagues confirm on Monday.
Have a nice week-end
Regards,
Alain
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
All good mate, just let us know if it gets resolved, thats way more important!
Cheers,
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Confirmed! The issue can be marked as resolved. Thanks guys for your support
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Glad it helped you mate. As my good friend would say, we are after all brothers from different mothers helping each other out : - ). Its not Oscar Wilde, more IT geek type of poetry lol
Anyway, happy it all got sorted out.
Cheers and dont hesitate to reach out directly if any issues down the road.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apologies mate, forgot to attach a screenshot. This is what I was referring to.
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 21 | |
| 11 | |
| 9 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 4 | |
| 3 |
Upcoming Events
Thu 13 Feb 2025 @ 03:00 AM (CET)
Navigating the Cyber Frontier: A Check Point Executive Briefing - APACThu 13 Feb 2025 @ 03:00 PM (CET)
Navigating the Cyber Frontier: A Check Point Executive Briefing - EMEAThu 13 Feb 2025 @ 02:00 PM (EST)
Navigating the Cyber Frontier: A Check Point Executive Briefing - AmericasFri 14 Feb 2025 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 33: CPX 2025 terugblik!Tue 18 Feb 2025 @ 03:00 PM (CET)
Why Adding SASE to Your Network Infrastructure is a Win-Win - EMEATue 18 Feb 2025 @ 02:00 PM (EST)
Why Adding SASE to Your Network Infrastructure is a Win-Win - AMERICASThu 13 Feb 2025 @ 03:00 AM (CET)
Navigating the Cyber Frontier: A Check Point Executive Briefing - APACThu 13 Feb 2025 @ 03:00 PM (CET)
Navigating the Cyber Frontier: A Check Point Executive Briefing - EMEAThu 13 Feb 2025 @ 02:00 PM (EST)
Navigating the Cyber Frontier: A Check Point Executive Briefing - AmericasFri 14 Feb 2025 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 33: CPX 2025 terugblik!Tue 18 Feb 2025 @ 03:00 PM (CET)
Why Adding SASE to Your Network Infrastructure is a Win-Win - EMEATue 18 Feb 2025 @ 02:00 PM (EST)
Why Adding SASE to Your Network Infrastructure is a Win-Win - AMERICASAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter