- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Quantum Spark Management Unleashed!
Check Point Named Leader
2025 Gartner® Magic Quadrant™ for Hybrid Mesh Firewall
HTTPS Inspection
Help us to understand your needs better
CheckMates Go:
SharePoint CVEs and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Traffic being dropped by Anti Malware
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Traffic being dropped by Anti Malware
I'm troubleshooting a problem with users unable to log into the backblaze website. It reports an issue fetching the account however if I switch to a broadband connection it works fine!
Checking the logs I see nothing being blocked, however when I run a zdebug I see the following:
@;1564707902;[cpu_6];[fw4_2];fw_log_drop_ex: Packet proto=6 10.110.0.10:62707 -> 62.0.58.94:443 dropped by fw_handle_first_packet Reason: Anti Malware;
The first confusing thing is the destination IP appears to belong to Checkpoint.
The Threat prevention policy is set to Optimised but the IPS blade is not enabled (in fact at present only the anti-bot and anti-virus blades are enabled. (not idea I know but this is a temporary measure) Also note that HTTPS inspection is not enabled at present either)
I've tried creating a new rule for the machine in question, disabling all threat prevention, but the issue remains.
Any assistance would be appreciated!
Thanks in advance.
25 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you find the corresponding logs? It might be, for example, the GW is checking SNI for that server and founds it a malware site. What do the AB logs say?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Val,
There are no logs that I can find for this, I've checked in the main logs, and also logs for the AB and the AM blades, I'm only seeing the drops when running a zdebug.
Out of interest, if I try to login from my laptop running the full Harmony Endpoint suite connected to broadband, there are no problems, which indicates that the site is ok. So the issue is only when the connection is going via the gateway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok, I know this may sound extreme thing to try, specially during work hours, but to be 100% sure, are you able to disable anti-bot and install policy? If that works, then we are positive something within that blade is causing it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That is extreme, but it would certainly prove that the AB blade is the culprit!
I'll try this later tonight if I can.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I agree, BUT, here is good news...even if you disable the blade and install policy, it would NOT wipe out any existing settings, rules, si easy to put it all back after, just re-enable the and install the policy again.
Personally, I would still make sure I have screenshots of all the existing things related to AB...better be on the safe side.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I agree 100%, record the settings first!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Look at the raw logs, search by source and destination. It is extremely unlikely there are no logs at all.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I've never tried viewing the raw logs, are you able to advise how I do this please? (I know where they are stored!)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
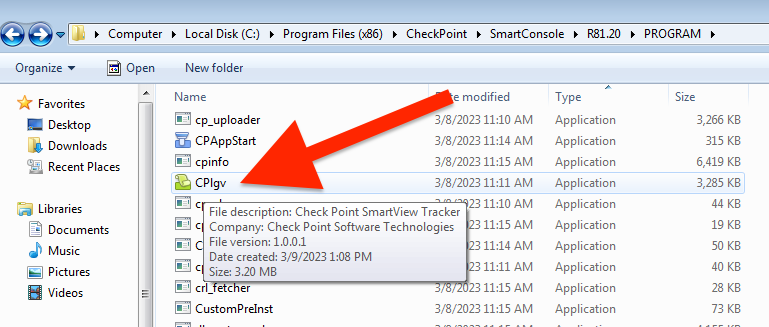
Search either via SmartView or in SmartViewTracker. The latter is a legacy application available with your SmartConsole installation package. You will need to go to the SmartConsole program folder and find it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry, I didn't realise that you were referring to SmartView when you said to look at the raw logs.
I can't find Smartview Tracker in the SmartConsole folders at all.
SmartView runs but returns an error - Query failed. This is before I even type a query, and for anything I type. I suspect that this may relate to SmartEvent not being enabled? The reason for this is that we are recovering from an incident, so currently running with on box management on a 5800 applicance, and disk space is limited.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
While you are fixing your SmartLog, here is the SmartView Tracker
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for that!
Running this and filtering by the users IP I see nothing more that the logging in Smartconsole unfortunately, but zdebug still shows the drops.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thats odd, as normally, when someone has issues with log indexing, logs show perfectly fine from old school SV tracker, as @_Val_ pointed out in his screenshot.
So, you dont see anything more from there either?
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No I don't, there is just some http and https traffic in the logs, but nothing going to the address that zdebug is showing, which I beleive is a Checkpoint IP address!
I've now also tried an fwmonitor for a short time whilst I tested the login process, but it only sees the packets that zdebug is dropping.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Maybe not related to you directly, but I would give this a go
https://support.checkpoint.com/results/sk/sk123075
fw ctl set int mal_conns_dep_limit 0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey mate,
Did you end up disabling AB blade to see if it makes any difference?
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, sorry for the slow reply, I work remotely and had no connection all day yesterday (drunk driver hit a telegraph pole!)
I did disable the AB blade an Monday night, and it resolved this issue, so that was a good move.
I then re-enabled it and tested again and it still worked!
I cleared the cache and rebooted the test pc, it still worked.
Couldn't do anything yesterday, tested again today and it's stopped working again!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's a good time to open that support request with TAC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry to hear about the incident. I think that based on all the testing you did, this definitely warrants TAC case. Keep us posted how it goes.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's with TAC now, they are investigating. I'll let you know the outcome, but will be out of the office for a few days now!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sounds good, hopefully it gets sorted out, Im positive.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
TAC have come back to me and said "it seems that the URL api002.backblazeb2.com was blocked in TC due to one of our automatic feeds"
They have whitelisted it at their end and it has resolved the issue!
Regards, Steve
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The default value for DNS trap IP is 62.0.58.94
more detail here:
https://support.checkpoint.com/results/sk/sk74060
It may be a query from your DNS server that is triggering anti malware/anti bot blade to return the DNS trap IP, instead of the real backblaze IP address.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for this, I was unaware of this default address.
I've changed this in the config and sure enough it now reports the same error against the trap address that I set, so it thinks that there is a problem with the DNS lookup I assume.
What bothers me is that this gateway is a temporary solution whilst we rebuild the original one with its original policy. I have access to this and there are no exceptions for this site, and it always used to work fine. It suggests that the site may have been compromised, so I'm hesitant about putting an exception in for it.
As Val suggests, I'm going to raise a ticket with TAC to see what their view on this is.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Steve_Pearson That's odd. I advise you to open a TAC case for this: https://help.checkpoint.com
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 12 | |
| 8 | |
| 7 | |
| 6 | |
| 6 | |
| 6 | |
| 4 | |
| 4 | |
| 3 |
Upcoming Events
Tue 16 Sep 2025 @ 02:00 PM (EDT)
Securing Applications with Check Point and AWS: A Unified WAF-as-a-Service Approach - AmericasWed 17 Sep 2025 @ 04:00 PM (AEST)
Securing Applications with Check Point and AWS: A Unified WAF-as-a-Service Approach - APACWed 17 Sep 2025 @ 03:00 PM (CEST)
Securing Applications with Check Point and AWS: A Unified WAF-as-a-Service Approach - EMEAThu 18 Sep 2025 @ 03:00 PM (CEST)
Bridge the Unmanaged Device Gap with Enterprise Browser - EMEAThu 18 Sep 2025 @ 02:00 PM (EDT)
Bridge the Unmanaged Device Gap with Enterprise Browser - AmericasTue 16 Sep 2025 @ 02:00 PM (EDT)
Securing Applications with Check Point and AWS: A Unified WAF-as-a-Service Approach - AmericasWed 17 Sep 2025 @ 04:00 PM (AEST)
Securing Applications with Check Point and AWS: A Unified WAF-as-a-Service Approach - APACWed 17 Sep 2025 @ 03:00 PM (CEST)
Securing Applications with Check Point and AWS: A Unified WAF-as-a-Service Approach - EMEAThu 18 Sep 2025 @ 03:00 PM (CEST)
Bridge the Unmanaged Device Gap with Enterprise Browser - EMEAThu 18 Sep 2025 @ 02:00 PM (EDT)
Bridge the Unmanaged Device Gap with Enterprise Browser - AmericasAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter