- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
Policy Insights and Policy Auditor in Action
19 November @ 5pm CET / 11am ET
Access Control and Threat Prevention Best Practices
Watch HereOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: The packets from a source to a destination in ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
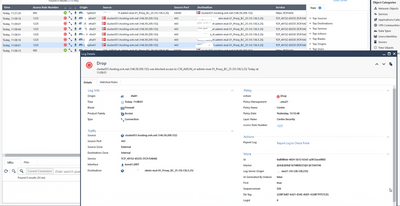
The packets from a source to a destination in one path and takes a different path when it returns
17 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have you confirmed the routing is correct end-to-end and that anti-spoofing is set correctly?
Is there any NAT involved and could you please share a better/clearer screenshot?
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This screenshot appears different to the original, can you provide the more detailed log cards for both flows?
There is some suggestion here that's proxy is involved, are only some ports/redirected to the proxy and others NAT different?
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I didn't understand your message but the client has a proxy in his intranet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would agree totally with what Chris said. 99% of the time, its either NAT, routing or anti-spoofing (or combination of all of them).
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok I will check the cpinfo file today to verify?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What will you check how in cpinfo ?
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As i said, I am currently looking for the cause of the asymmetric routing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
But how to accomplish this in cpinfo ? Never heard of routing issues resolved by cpinfo analysis...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don't have access to the appliance, so i will analyze on my side the cpinfo file and after that i will contact the customer to have clear understanding of the issues.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I do not think you will find all answers in the CPInfo. In most cases, asymmetric routing is caused by external factors.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great - which tool are you using ? Or do you search in the cpinfo text ?
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CheckPoint Diagnostics View
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey @A_KOUADIO ,
I think what @_Val_ and @G_W_Albrecht are saying is that its very unlikely you would find an answer as to why assymetric routing happens from cpinfo file review, as thats simply the config file from the firewall. Here is what I would run and examine carefully the output. So, just as an example, say the source is 10.10.10.10 and dst is 20.20.20.20, try commands like below:
fw monitor -e "accept host(10.10.10.10) and dst(20.20.20.20);"
fw monitor -e "accept host(20.20.20.20) and dst(10.10.10.10);"
fw minitor -e "accept host(10.10.10.10) or dst(20.20.20.20);"
Alternatively, you can also use below command. Idea is to filter for src IP, src port, dst IP, dst IP, protocol
fw monitor -F "10.10.10.10,0,20.20.20.20,0,0" -F "20.20.20.20,0,10.10.10.10,0,0"
I can also suggest a website my colleague made ages ago to help people with captures on different platforms (its very useful)
Hope all this helps you.
Cheers,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dropped by Access Rule Number 1225 ???
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Because the source port match another rule.
As I said previously, the return traffic is dissociated from the going trafic so it match another rule or drop by the cleanup rule.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would not use 1225 rules - but that should not cause asymmetrical routing afaik...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 27 | |
| 23 | |
| 15 | |
| 12 | |
| 10 | |
| 9 | |
| 6 | |
| 6 | |
| 5 | |
| 4 |
Upcoming Events
Thu 13 Nov 2025 @ 10:00 AM (CET)
Cloud Architect Series - Guarding Generative AI: Next-Gen Application Security with CloudGuard WAFThu 13 Nov 2025 @ 06:00 PM (COT)
Tegucigalpa: Risk Management al Horno: ERM, TEM & Pizza Night para la Comunidad CheckMatesThu 13 Nov 2025 @ 10:00 AM (CET)
Cloud Architect Series - Guarding Generative AI: Next-Gen Application Security with CloudGuard WAFFri 14 Nov 2025 @ 10:00 AM (CET)
CheckMates Live Netherlands - Veriti, Threat Exposure ManagementWed 19 Nov 2025 @ 11:00 AM (EST)
TechTalk: Improve Your Security Posture with Threat Prevention and Policy InsightsThu 20 Nov 2025 @ 05:00 PM (CET)
Hacking LLM Applications: latest research and insights from our LLM pen testing projects - AMERThu 20 Nov 2025 @ 10:00 AM (CST)
Hacking LLM Applications: latest research and insights from our LLM pen testing projects - EMEAThu 13 Nov 2025 @ 06:00 PM (COT)
Tegucigalpa: Risk Management al Horno: ERM, TEM & Pizza Night para la Comunidad CheckMatesThu 13 Nov 2025 @ 06:00 PM (COT)
Tegucigalpa: Risk Management al Horno: ERM, TEM & Pizza NightAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter