This post is based on my initial comments here:
https://community.checkpoint.com/t5/Security-Gateways/Find-the-TCP-out-of-state-packets/m-p/111302/h...
Situation: The "Drop out of state TCP packets" checkbox on the Stateful Inspection screen of the Global Properties is unchecked. This is not the default setting and is not considered security best practices, as traffic that is "out of state" or does not otherwise exist in the firewall's connections state table will not be blocked if the checkbox is not set.
Rechecking this box is always a bit nerve-racking, especially if no one knows or can remember why it was unchecked in the first place. Leaving this box unchecked will permit various situations such as asymmetric routing and faulty TCP implementations to continue working, and checking the box could suddenly break these things. It is possible to quickly toggle the checkbox on a live security gateway as described here if things do suddenly break:
sk117374: How to enable/disable Out of State inspection on a Security Gateway without performing a p...
However the nagging question still remains: regardless of how we toggle the dropping of out of state TCP packets, when should we actually do it? If we enable it after regular business hours, things may well be broken all night and we get a really lousy start to our morning. If we do it in the middle of production during the day, the sudden breaking of things could cause even more career-limiting problems to occur even if we manage to toggle it back quickly from the gateway CLI.
But there is another way: there is a hidden "monitor mode" functionality for dropping out of state TCP packets that will allow us to enable this function, see logs for it, but it doesn't actually drop the traffic. This will allow us to assess the impact of enabling this checkbox without actually breaking things. So here we see a typical "out of state" drop where the checkbox is set:
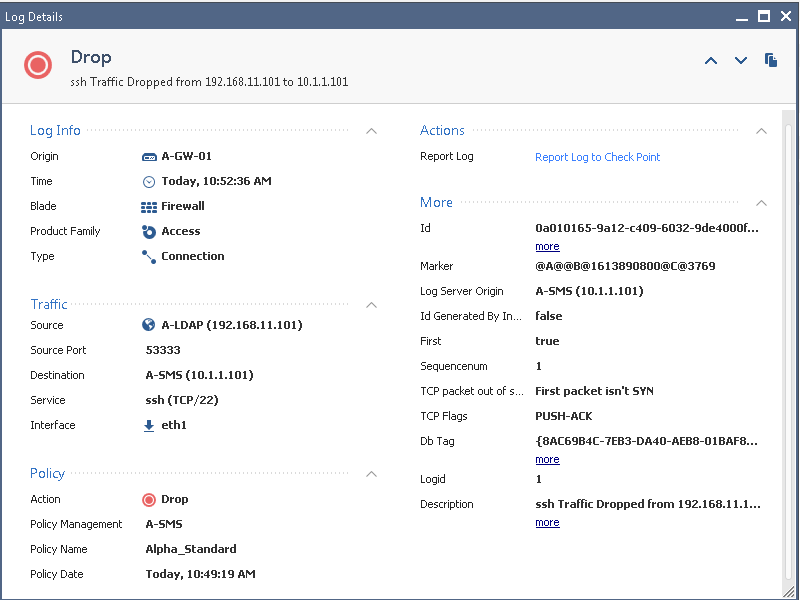
However then we toggle this kernel value:
[Expert@A-GW-01:0]# fw ctl get int fw_tcp_out_of_state_monitor
fw_tcp_out_of_state_monitor = 0
[Expert@A-GW-01:0]# fw ctl set int fw_tcp_out_of_state_monitor 1
[Expert@A-GW-01:0]# fw ctl get int fw_tcp_out_of_state_monitor
fw_tcp_out_of_state_monitor = 1
And now:
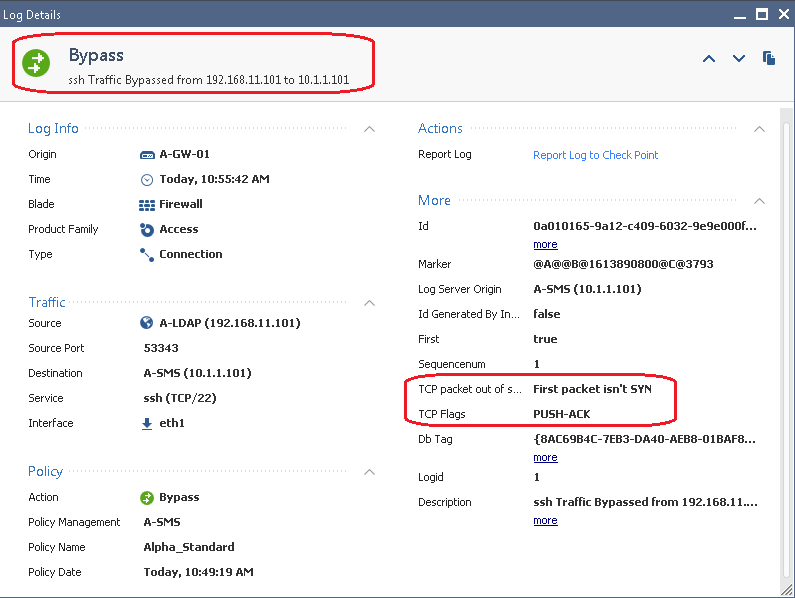
So toggling the fw_tcp_out_of_state_monitor kernel value to 1, checking the "Drop out of state TCP packets" box and reinstalling the policy will allow us to observe in the logs what would happen if the box was to be rechecked. Once we are confident that things won't get broken, we toggle fw_tcp_out_of_state_monitor back to its default of 0.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course




