- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- TCP Out of State Drops - Hidden Monitor Mode
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
TCP Out of State Drops - Hidden Monitor Mode
This post is based on my initial comments here:
Situation: The "Drop out of state TCP packets" checkbox on the Stateful Inspection screen of the Global Properties is unchecked. This is not the default setting and is not considered security best practices, as traffic that is "out of state" or does not otherwise exist in the firewall's connections state table will not be blocked if the checkbox is not set.
Rechecking this box is always a bit nerve-racking, especially if no one knows or can remember why it was unchecked in the first place. Leaving this box unchecked will permit various situations such as asymmetric routing and faulty TCP implementations to continue working, and checking the box could suddenly break these things. It is possible to quickly toggle the checkbox on a live security gateway as described here if things do suddenly break:
However the nagging question still remains: regardless of how we toggle the dropping of out of state TCP packets, when should we actually do it? If we enable it after regular business hours, things may well be broken all night and we get a really lousy start to our morning. If we do it in the middle of production during the day, the sudden breaking of things could cause even more career-limiting problems to occur even if we manage to toggle it back quickly from the gateway CLI.
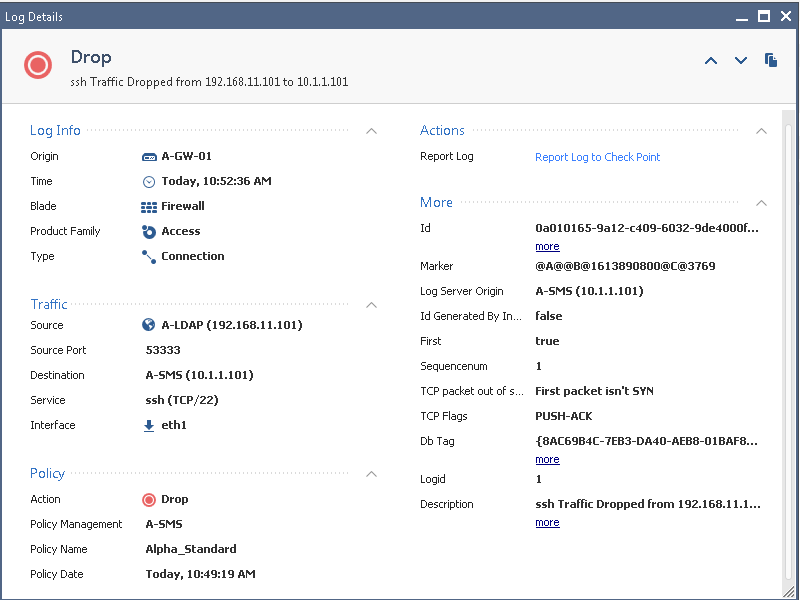
But there is another way: there is a hidden "monitor mode" functionality for dropping out of state TCP packets that will allow us to enable this function, see logs for it, but it doesn't actually drop the traffic. This will allow us to assess the impact of enabling this checkbox without actually breaking things. So here we see a typical "out of state" drop where the checkbox is set:
However then we toggle this kernel value:
[Expert@A-GW-01:0]# fw ctl get int fw_tcp_out_of_state_monitor
fw_tcp_out_of_state_monitor = 0
[Expert@A-GW-01:0]# fw ctl set int fw_tcp_out_of_state_monitor 1
[Expert@A-GW-01:0]# fw ctl get int fw_tcp_out_of_state_monitor
fw_tcp_out_of_state_monitor = 1
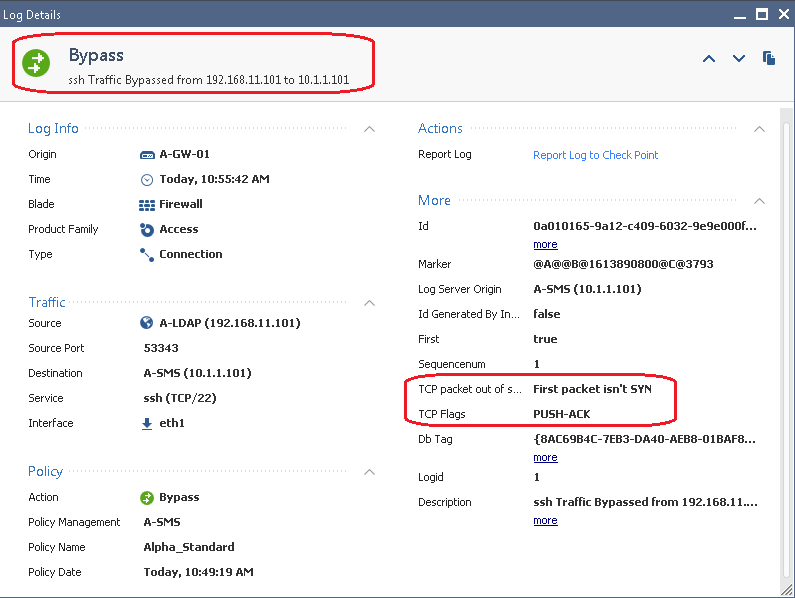
And now:
So toggling the fw_tcp_out_of_state_monitor kernel value to 1, checking the "Drop out of state TCP packets" box and reinstalling the policy will allow us to observe in the logs what would happen if the box was to be rechecked. Once we are confident that things won't get broken, we toggle fw_tcp_out_of_state_monitor back to its default of 0.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
13 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Timothy_Hall , this will save us from a lot of trouble monday morning like you wrote.
With the monitoring feature we have time to analyze and debug the traffic without any disruption.
Any information which version support this ? Is it new in R81 or available too in older releases?
Wolfgang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just checked in my lab, the variable fw_tcp_out_of_state_monitor exists in R81 and also at least back into gateway version R80.10. Can't see why it wouldn't exist in R77.30 and earlier as well, although I have no easy way to verify that at the moment.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do you see some real life situation why "TCP packet out of state" should be allowed ?
Isnt it functionality of firewall to inspect the TCP packet and drop packet which is not correct (wrong implementation of TCP RFC or routing) ?
Instead of correcting real TCP packer order, the admins are allowing workaround ?
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The most common situation is allowing asymmetric routing which is not the end of the world, but is certainly not desirable as it can cause some strange effects especially in the realm of network performance. Another scenario is the checkbox gets unset as part of troubleshooting and never gets rechecked; I've also seen situations where an organization's firewalls were outsourced to a MSP, then insourced back to the internal IT team, and the box had been left unchecked by the MSP. Hard to know what to do in that case.
One other situation would be to uncheck this box prior to a gateway cluster version upgrade to blunt the effect of a non-stateful failover, and then forgetting to recheck it. However unless you are jumping a very very long way as far as gateway version during the cluster upgrade, Check Point has gotten very good about maintaining "statefulness" through all of the upgrade steps assuming the proper procedures are followed. So unchecking this box as part of a cluster upgrade is becoming much less common now.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Timothy_Hall . Thank you for a great addition to the toolbox.
Question though: when we enable bypass, is out of state traffic being processed by the rulebase at all?
Also, to add to your statement about the original cause (for unchecked box), being asymmetric routing: in these cases, you pretty much guaranteed to see the anti-spoofing configured in "Detect", disabled outright or including exemptions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
> Question though: when we enable bypass, is out of state traffic being processed by the rulebase at all?
For purposes of stateful inspection and the Firewall/Network policy layer, it is not being inspected as the Bypass is specific to the Firewall blade/feature. I would assume the out of state traffic is still able to be inspected by other blades such as APCL/URLF and Threat Prevention.
> Also, to add to your statement about the original cause (for unchecked box), being asymmetric routing: in these cases, you pretty much guaranteed to see the anti-spoofing configured in "Detect", disabled outright or including exemptions.
True but it is possible to configure the same network/subnet on more than one interface in the topology configuration, so antispoofing can still be utilized properly in an asymmetric scenario. However as you mention in most cases administrators get confused about what is really going on with traffic getting dropped, and either set antispoofing to Detect or just disable it completely.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Option is available on R77.20 SMB gateways:
[Expert@myfw]# fw ctl get int fw_tcp_out_of_state_monitor
fw_tcp_out_of_state_monitor = 0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Timothy_Hall, thank you for your useful post.
When the traffic is bypassed, the firewall still allow it, right ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Timothy_Hall,
Can you please explain the inner mechanics of Hidden Monitor mode? Does this feature send RST packets (to client and server) when out of state packet arrives at the gateway to invite new connection formed after the timed out connection is removed from the connection table? I 'll appreciate if you can shed some light on the inner workings of the Hidden Monitor Mode enabled feature.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Be aware there were some fixes for the out of state monitor mode introduced in R81.10 Jumbo HFA 93+:
|
PRJ-29668, |
SecureXL |
When the "fw_tcp_out_of_state_monitor" mode is enabled with the "fw_allow_out_of_state_tcp" flag, some connections may be dropped, although they should go through and be monitored. |
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have a look at How to enable/disable Out of State inspection on a Security Gateway without performing a policy inst...
"The above procedure is only temporary and will not survive a reboot, restart of Check Point services (cpstop;cpstart, or cprestart), or policy installation."
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 11 | |
| 8 | |
| 7 | |
| 6 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter