- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
CheckMates Fest 2025!
Join the Biggest Event of the Year!
Simplifying Zero Trust Security
with Infinity Identity!
Operational Health Monitoring
Help us with the Short-Term Roadmap
CheckMates Go:
Recently on CheckMates
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Security Gateways
- :
- Some connections show XLATE NAT, some are not
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
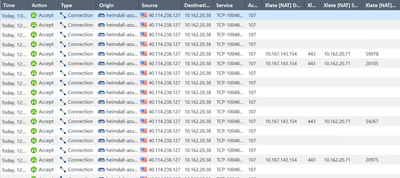
Some connections show XLATE NAT, some are not
Hi,
We have a connection flow 40.114.238.127 > 10.162.20.38 or 10.162.20.39 port 10048.
When i check traffic log, some connections show XLATE NAT. But some are not showing, even though all connections are accepted.
You can check below:
Labels
- Labels:
-
NAT
14 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Could someone explain why we can not see XLATE NAT on some connections ? Are they normal or abnormal ?
If abnormal, how can we fix it ?
Thanks in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
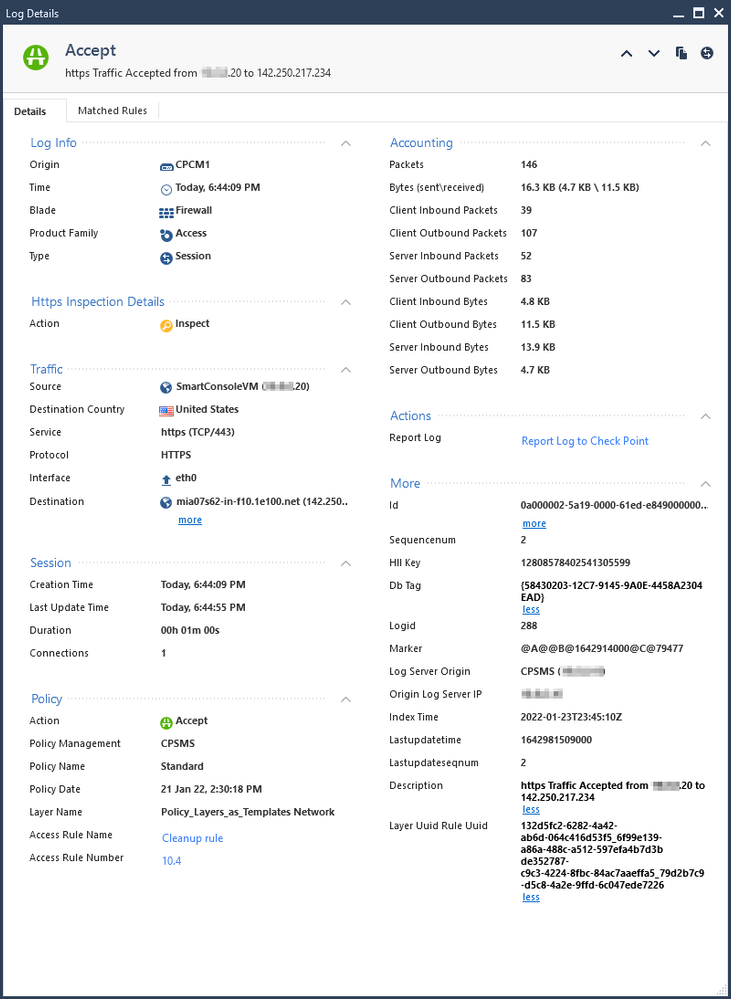
Please post the full log card with all sections exposed of one log entry that is showing NAT in the columnar output, and another log card that is not. Please redact identifying IP addresses as needed. It may be due to Session Logging but it looks like all of those are Connection-based logs.
Attend my 60-minute "Be your Own TAC: Part Deux" Presentation
Exclusively at CPX 2025 Las Vegas Tuesday Feb 25th @ 1:00pm
Exclusively at CPX 2025 Las Vegas Tuesday Feb 25th @ 1:00pm
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Timothy,
I am not sure if below is full log cards you need.
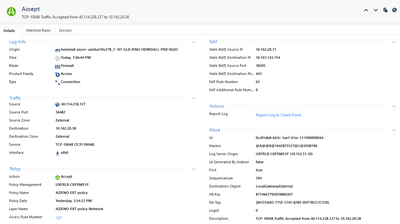
an example log With Xlate NAT:
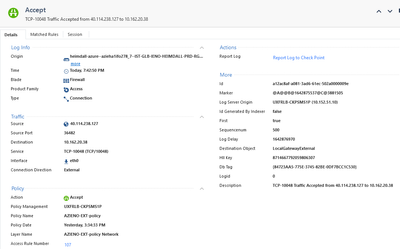
an example log Without Xlate NAT:
If they are not full log cards you need, so could you please tell me how to get them ?
Thanks in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
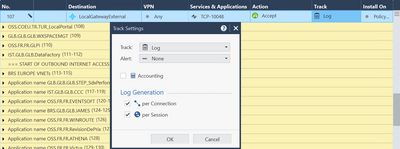
Hmm it is almost like those logs are duplicates of each other, however they are two unique logs generated by the gateway due to the unique Id and Sequence Number under More, almost like you have both Session Logging and Connection Logging set for that rule due to the presence of the Session tab. In your rulebase please right-click the Track column of rule 107 and select More, then post a screenshot of your Track and Log Generation options for that rule. These somewhat hidden Log Generation options are the subject of my 2022 CPX speech called "Max Gander: The Hidden World of Log Generation and Log Suppression on Check Point".
I'm also going to loop in @Vladimir here for his opinion as this is similar to another situation we were discussing recently.
Attend my 60-minute "Be your Own TAC: Part Deux" Presentation
Exclusively at CPX 2025 Las Vegas Tuesday Feb 25th @ 1:00pm
Exclusively at CPX 2025 Las Vegas Tuesday Feb 25th @ 1:00pm
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Timothy_Hall , thank you for looping me in. Definitely something to look into. @Equipe_reseau , can you tell us what version and JHFA you are running and if NAT Templates are enabled ('fwaccel stat' output)?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @Vladimir ,
Here is the result:
[Expert@#####]# cpinfo -y all
This is Check Point CPinfo Build 914000227 for GAIA
[CPFC]
HOTFIX_R80_30_GOGO_JHF_MAIN Take: 236
[MGMT]
No hotfixes..
[IDA]
No hotfixes..
[FW1]
HOTFIX_MAAS_TUNNEL_AUTOUPDATE
HOTFIX_R80_30_GOGO_JHF_MAIN Take: 236
FW1 build number:
This is Check Point's software version R80.30 - Build 240
kernel: R80.30 - Build 250
[SecurePlatform]
HOTFIX_R80_30_GOGO_JHF_MAIN Take: 236
[CPinfo]
No hotfixes..
[PPACK]
HOTFIX_R80_30_GOGO_JHF_MAIN Take: 236
[CVPN]
HOTFIX_R80_30_GOGO_JHF_MAIN Take: 236
[CPUpdates]
BUNDLE_CPSDC_AUTOUPDATE Take: 19
BUNDLE_INFRA_AUTOUPDATE Take: 52
BUNDLE_DEP_INSTALLER_AUTOUPDATE Take: 23
BUNDLE_HCP_AUTOUPDATE Take: 48
BUNDLE_MAAS_TUNNEL_AUTOUPDATE Take: 61
BUNDLE_R80_30_JUMBO_HF_MAIN_3_10_GW Take: 236
[CPDepInst]
No hotfixes..
[AutoUpdater]
No hotfixes..
[hcp_wrapper]
HOTFIX_HCP_AUTOUPDATE
[DIAG]
No hotfixes..
[cpsdc_wrapper]
HOTFIX_CPSDC_AUTOUPDATE
[Expert@###:0]# fwaccel stat
+-----------------------------------------------------------------------------+
|Id|Name |Status |Interfaces |Features |
+-----------------------------------------------------------------------------+
|0 |SND |enabled |eth0,eth1,enP1p0s2, |
| | | |enP2p0s2 |Acceleration,Cryptography |
| | | | |Crypto: Tunnel,UDPEncap,MD5, |
| | | | |SHA1,NULL,3DES,DES,CAST, |
| | | | |CAST-40,AES-128,AES-256,ESP, |
| | | | |LinkSelection,DynamicVPN, |
| | | | |NatTraversal,AES-XCBC,SHA256, |
| | | | |SHA384 |
+-----------------------------------------------------------------------------+
Accept Templates : enabled
Drop Templates : disabled
NAT Templates : enabled
Thanks for your kind support.
Regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
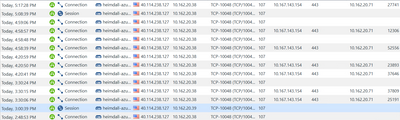
Yes, on our traffic logs, we could observe both Session logs and Connection logs as below.
But the problem here is that Xlate NAT is showing on some Connection logs, and others are not 😞 we dont know if it is a Checkpoint issue (which could cause real connection issue) or it is a normal behavior.
Regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
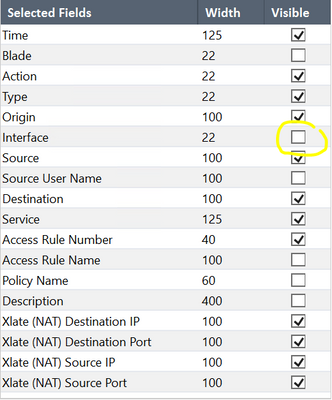
@Equipe_reseau , I see that the log containing NAT data is also listing Source and destination zones, whereas the log without NAT data, does not contain zone information.
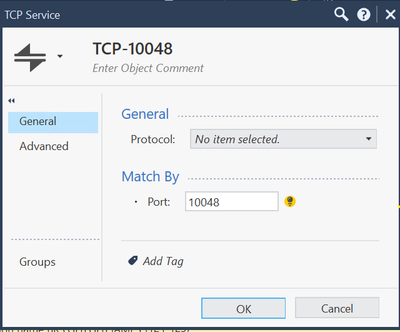
If I have to venture a guess, this is a "router on a stick" implementation and the connection is being logged twice. Not sure if it is intended behavior though. Can you check to see if the Interface filter is enabled in the log view, remove it and post another screenshot? Also, and I am not sure if it is material, the General and Advanced properties of your TCP-10048 service.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Vladimir ,
Since the beginning, we have not enabled interface filter on our log view.
Below is General and Advanced for our TCP-10048 service.
Regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nice catch @Vladimir on the zone information being in one log card and not the other. Definitely possible in a router on a stick implementation.
However Vladimir's question about NAT Templates bugged me a bit and after staring at the two log cards for way too long here is what may be happening (which may possibly explain the lack of NAT information in Session-based logs too). Bear with me here...
In R80.10 and earlier NAT Templates were not enabled, but if they were the sim/SecureXL driver would form NAT Templates (and also of course Accept Templates) by observing traffic leaving the firewall outbound through the sim driver after the initial packet of a new connection went through the inbound side of sim and up into F2F for a rulebase lookup. Obviously if the packet was dropped no templates would form.
However if the packet was allowed by F2F SecureXL would compare what the packet looked like on the inbound side of sim and the outbound side of sim to form NAT Templates (and Accept Templates) directly in SecureXL. Future new connections requiring NAT that matched an Accept Template could also match a NAT Template thus avoiding a F2F trip for a NAT rulebase lookup on a worker.
However note here that SecureXL NAT Templates are not formed by a NAT rulebase lookup, just by observing traffic that passed completely through F2F and back into sim. Contrast this with a cache hit against the separate NAT rulebase caching mechanism on the worker called fwx_cache; that table includes the NAT rule number right in the cache table as detailed in the third edition of my book where I do a poor man's NAT hit count trick on page 301-302. Obviously with a full-fledged NAT rulebase lookup on the worker due to an fwx_cache miss the matching NAT rule number(s) will be known as well.
So here is the crux of the issue: if a new connection matches against a NAT Template how the heck does it know what NAT rule number was matched? I don't think there is any way to know that at the sim/SecureXL level, which is why the "NAT" section is not being shown for some of your log entries; those matched a NAT Template. The packets that matched a cached entry in fwx_cache or a full NAT rule base lookup will of course have the NAT log information present.
However in R80.20+ the initial creation of Accept/NAT templates was shifted from the sim driver up into the workers, BUT those templates are still offloaded back into sim/SecureXL for implementation, and the old limitation of not knowing the NAT rule number might still be there. So Vladimir perhaps the NAT information is not included in pure Session logs because not all the similar connections that were rolled up had NAT information present due to partial NAT template matching, so it just leaves it out completely?
I'll admit I'm stretching here but this could be tested pretty easily by just turning NAT Templates off and making sure to start a NEW connection and see what happens with the NAT logging, even with only Session Logging enabled. May even want to disable NAT Templates permanently and reboot the entire firewall before testing just to be sure, since "disabling" SecureXL in R80.20+ isn't what it used to be.
Attend my 60-minute "Be your Own TAC: Part Deux" Presentation
Exclusively at CPX 2025 Las Vegas Tuesday Feb 25th @ 1:00pm
Exclusively at CPX 2025 Las Vegas Tuesday Feb 25th @ 1:00pm
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Timothy_Hall , since I am testing in my lab and it is not a router on a stick, there is no one-to-one correlation, but so far, no dice: with NAT templates disabled:
[Expert@CPCM1:0]# fwaccel stat
+---------------------------------------------------------------------------------+
|Id|Name |Status |Interfaces |Features |
+---------------------------------------------------------------------------------+
|0 |SND |enabled |eth0,eth1,eth2,eth3,eth4,|Acceleration,Cryptography |
| | | |eth5 | |
| | | | |Crypto: Tunnel,UDPEncap,MD5, |
| | | | |SHA1,3DES,DES,AES-128,AES-256,|
| | | | |ESP,LinkSelection,DynamicVPN, |
| | | | |NatTraversal,AES-XCBC,SHA256, |
| | | | |SHA384,SHA512 |
+---------------------------------------------------------------------------------+
Accept Templates : enabled
Drop Templates : disabled
NAT Templates : disabled by user
[Expert@CPCM1:0]#
...rebooted and made active cluster member.
Firewall sessions do not contain NAT data. (deleted mention of no Firewall sessions being logged, took longer to show up in the log than I expected.)
When connections are logged, they do contain NAT data, but that was the case before NAT templates were disabled.
The APCL/URLF sessions are also present in the logs, but do not contain NAT data.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Well so much for that theory involving NAT Templates, probably time for a TAC case unless Vladimir has any other ideas.
Attend my 60-minute "Be your Own TAC: Part Deux" Presentation
Exclusively at CPX 2025 Las Vegas Tuesday Feb 25th @ 1:00pm
Exclusively at CPX 2025 Las Vegas Tuesday Feb 25th @ 1:00pm
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Timothy_Hall and @Equipe_reseau . I suspect that this particular issue, i.e. seemingly identical connection logs with and without NAT are the result of the combination of 'router on a stick' and the rule's destination specified as Firewall's External. By the way, what is in the Source field of that rule?
Not sure how Azure is handling the traffic in the buffer zone between firewall's interface and the next hop, but it is entirely possible for FW to see the packet on its way out reflected to eth0, accept and log it, as per rule's structure.
I further suspect, that if you want to see only accurately processed packets in the logs, you may have to suppress logging on that rule (or limit it to firewall sessions, which will not contain NAT data) and add an additional one with the same service and the destination being 10.162.20.0/24 (or whatever your destination network is.
...or TAC it and please keep us updated.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 25 | |
| 9 | |
| 9 | |
| 8 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 2 |
Trending Discussions
Upcoming Events
Thu 13 Feb 2025 @ 03:00 AM (CET)
Navigating the Cyber Frontier: A Check Point Executive Briefing - APACThu 13 Feb 2025 @ 03:00 PM (CET)
Navigating the Cyber Frontier: A Check Point Executive Briefing - EMEAThu 13 Feb 2025 @ 02:00 PM (EST)
Navigating the Cyber Frontier: A Check Point Executive Briefing - AmericasFri 14 Feb 2025 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 33: CPX 2025 terugblik!Tue 18 Feb 2025 @ 03:00 PM (CET)
Why Adding SASE to Your Network Infrastructure is a Win-Win - EMEATue 18 Feb 2025 @ 02:00 PM (EST)
Why Adding SASE to Your Network Infrastructure is a Win-Win - AMERICASThu 13 Feb 2025 @ 03:00 AM (CET)
Navigating the Cyber Frontier: A Check Point Executive Briefing - APACThu 13 Feb 2025 @ 03:00 PM (CET)
Navigating the Cyber Frontier: A Check Point Executive Briefing - EMEAThu 13 Feb 2025 @ 02:00 PM (EST)
Navigating the Cyber Frontier: A Check Point Executive Briefing - AmericasFri 14 Feb 2025 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 33: CPX 2025 terugblik!Tue 18 Feb 2025 @ 03:00 PM (CET)
Why Adding SASE to Your Network Infrastructure is a Win-Win - EMEATue 18 Feb 2025 @ 02:00 PM (EST)
Why Adding SASE to Your Network Infrastructure is a Win-Win - AMERICASAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter