- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Site to site VPN using backup ISP for one site
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Site to site VPN using backup ISP for one site
Hello we have 4 sites total, 3 remote sites that connect back to our primary site via site to site vpn tunnels. All sites are checkpoint. One of our sites has a hop that is dropping/losing/whatever with packets and this is causing major slowness. Our primary ISP isn't being helpful since it isn't on their network. During our testing we found that if we use our backup ISP, it will use a different path and the slowness is gone.
So all of that to ask is it possible to route 1 site to site vpn over the backup ISP while leaving the others routed over the primary ISP?
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, you will need to adjust the Link Selection setting to make decision based on the routing table.
Refer to: https://sc1.checkpoint.com/documents/R81.10/WebAdminGuides/EN/CP_R81.10_SitetoSiteVPN_AdminGuide/Top...
12 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, you will need to adjust the Link Selection setting to make decision based on the routing table.
Refer to: https://sc1.checkpoint.com/documents/R81.10/WebAdminGuides/EN/CP_R81.10_SitetoSiteVPN_AdminGuide/Top...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am looking through the article you provided, my scenario from the way I see it would be similar to "Security Gateway with Several IP Addresses Used by Different Parties" There doesn't seem to be much direction on that one though. All sites have static addresses. I only want the one site to run on the alternate ISP. So I would need to add some routing on the local gateways to accomplish this? I am not sure if it make a difference or not but the remote site is running SMB's 1600 series.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, you would route all traffic for that particular site through the other ISP using static routes.
This will cause Link Selection to use the appropriate interface IP when doing a Site to Site VPN on that interface.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Would those static routes be on the remote site pointing back at the main site or at the main site pointing at the remote site? Or would it be on both?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The routes would be on the gateway where Link Selection is configured.
If the remote site has multiple ISPs also, you might want routes configured there as well to ensure symmetry.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
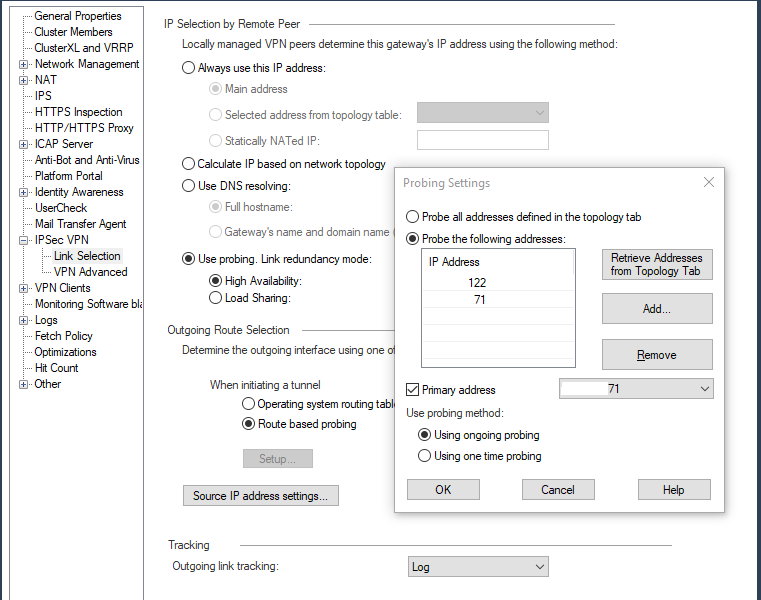
I guess I am missing something sorry - So often pictures are worth a 1000 words so I will include some pics below. First is the the link selection configuration from the Primary site - 71 is the normal ISP link 122 is the one I want this connection only to go out of.
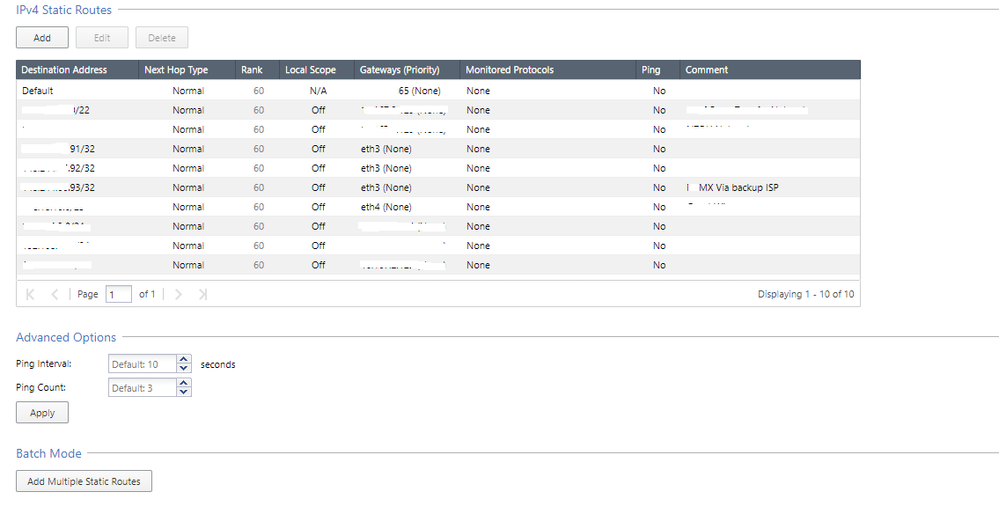
The second picture is of the static routes configured for this. The 91-93 are the external addresses of the remote cluster, Eth3 is the external interface of the alternate ISP I want this remote site to connect on.
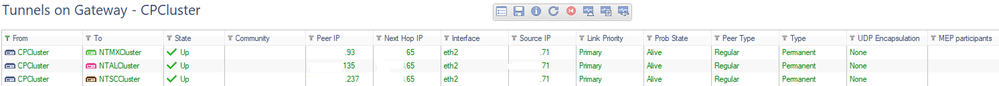
However my tunnel still is connecting on the 71 ISP even after resetting it multiple times.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You're using an interface route when you should be using an IP-based nexthop (specifically to the default route for ISP2).
Also, what is the Source IP address setting say?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So it should work like this? It looks like it is still using the gateway of .65 even after tunnel resets.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes like that.
And, unless a reboot solves it, I recommend a TAC case for further troubleshooting.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok, I am running installs of the latest Check_Point_R81_10_JUMBO_HF_MAIN_Bundle_T78 right now on the clusters so that restarts during the install. I will see if that resolves it. If not we can get a case rolling.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Our SMB at the remote site is managed by the same manager as the main site and the main site IP has its external set as its main IP. Does this change anything on what we need to configure?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You shouldn't need to.
That said, I highly recommend having TAC review your configuration.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 17 | |
| 13 | |
| 8 | |
| 7 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter