- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
CheckMates Fest 2025!
Join the Biggest Event of the Year!
Simplifying Zero Trust Security
with Infinity Identity!
Operational Health Monitoring
Help us with the Short-Term Roadmap
CheckMates Go:
Recently on CheckMates
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Security Gateways
- :
- Searching for IPS protections via ssh
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Searching for IPS protections via ssh
Hey guys,
Figured would share this in case anyone encounters the same problem. So had issue with customer where certain parts of sites on Azure were not coming up when testing from on prem and we ran debug and discovered it was related to IPS, but had hard time finding out the protection in question. So I saw there is a command you can run via expert mode if you have xeha-decimal value for protection (which we did from the drops) and once we got the protection name, was easy to fix the problem.
[Expert@quantum-firewall:0]# ips
Usage:
ips stat # Display IPS status
ips on|off # Enable\Disable IPS
ips bypass stat # Display Bypass Under Load status
ips bypass on|off # Enable\Disable bypass mode
ips bypass set cpu|mem low|high <th> # Set bypass thresholds
ips debug [-e filter] -o <outfile> # Get IPS debugs
ips refreshcap # Refresh the sample capture repository
ips stats [<ip_address> -m] [-g <seconds>] [<ip_address> <seconds>] [-h]
# Print IPS performance and PM statistics
ips protection <protection_id (hex)> # Display protection name
Note: IPS CLI configuration is temporary - it will be overridden by the next
policy installation or boot
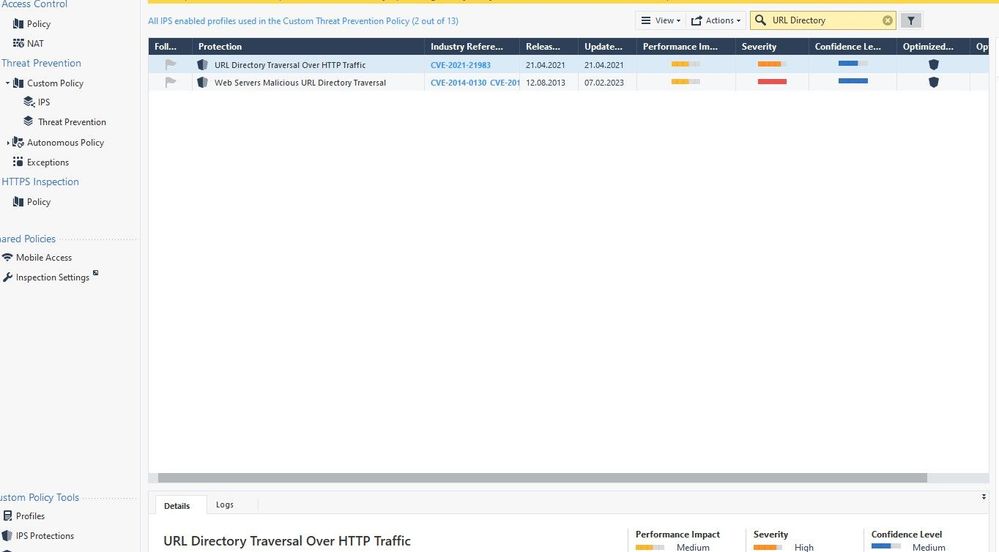
[Expert@quantum-firewall:0]# ips protection 0x82e5656a
Web Servers Malicious URL Directory Traversal
[Expert@quantum-firewall:0]#
I would say since we saw lots of errors first packet isnt SYN and customer proved this worked fine when NOT traversing the CP cluster, I would say, if you ever see that message, always check threat prevention blades, specially IPS, apart from obvious "culprits"...routing, NAT, sxl : - )
Cheers,
Andy
16 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Btw, these are drops from zdebug.
To add this as a side note, no matter what words we used to search for IPS protection in smart console, absolutely nothing worked and we were unable to find the actual protection.
@;436822375;[vs_0];[tid_1];[fw4_1];ips_cmi_handler_match_cb_ex: Packet dir 0, 19 2.168.37.190:63474 -> 10.30.11.17:80 IPP 6 dropped by IPS [reject] , protection_ id=0x82e5656a, protection_name=<GW CLI: ips protection 0x82e5656a>;
@;436822377;[vs_0];[tid_1];[fw4_1];fw_log_drop_ex: Packet proto=6 192.168.37.190 :63474 -> 10.30.11.17:80 dropped by fwmultik_process_f2p_cookie_inner Reason: PS L Drop: WS
@;436822379;[vs_0];[tid_1];[fw4_1];fw_log_drop_ex: Packet proto=6 192.168.37.190 :63474 -> 10.30.11.17:80 dropped by fwmultik_process_f2p_cookie_inner Reason: PS L Drop: WS
@;436822442;[vs_0];[tid_1];[fw4_1];ips_cmi_handler_match_cb_ex: Packet dir 0, 19 2.168.37.190:63424 -> 10.30.11.17:80 IPP 6 dropped by IPS [reject] , protection_ id=0x82e5656a, protection_name=<GW CLI: ips protection 0x82e5656a>;
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I can find it:
Has even been updated recently...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Well, you can find it when I gave full name lol. If you search by the actual words from the debug I attached, you will NOT find it : - )
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, therefore i use the most important part only...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Right and to GET to most important part you need the command : - )
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
But the command will not be helpfull if you cannot find the protection 8)
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So answer this then...based on debug I posted, and ONLY debug, how would you ever figure out what is the IPS protection if you dont run command I gave? 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the info @the_rock . I had exactly the same issue today; zdebug gave a hex code which doesn't show up when you search in the protections in SmartConsole. The CLI command told me the protection name, then I found it in SmartConsole using the name.
Interestingly also, these drops did not appear in the logs in SmartConsole, so at first I didn't even think I had an IPS issue until I'd done the zdebug. Not the first time the logs alone don't tell the full story. Or any of the story!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Glad it helped you.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The issue about lack of logging a specific IPS protection should probably be raised with TAC: https://help.checkpoint.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great tip!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Figured would share since I learned this myself today as well : - )
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Very nice, thanks for sharing.
Attend my 60-minute "Be your Own TAC: Part Deux" Presentation
Exclusively at CPX 2025 Las Vegas Tuesday Feb 25th @ 1:00pm
Exclusively at CPX 2025 Las Vegas Tuesday Feb 25th @ 1:00pm
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No worries, any time. I asked my colleague to share this link with TAC engineer, hopefully it saves them some time if they ever encounter this with another customer.
Cheers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Forgot to mention that it is possible to make the offending IPS signature name show up directly in the fw ctl zdebug drop output by changing variable enable_inspect_debug_compilation from false to true in GUIdbedit, although doing so will substantially increase the size of the compiled policy sent to the gateway: sk60395: How to debug IPS during issues with DCE-RPC traffic.
I haven't done this in quite some time and it may no longer be supported.
Attend my 60-minute "Be your Own TAC: Part Deux" Presentation
Exclusively at CPX 2025 Las Vegas Tuesday Feb 25th @ 1:00pm
Exclusively at CPX 2025 Las Vegas Tuesday Feb 25th @ 1:00pm
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ah, good to know.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 39 | |
| 12 | |
| 9 | |
| 7 | |
| 6 | |
| 6 | |
| 5 | |
| 5 | |
| 5 | |
| 4 |
Upcoming Events
Tue 04 Mar 2025 @ 04:00 PM (CET)
Check Point | WIZ : Powering the Next Era of Cloud Security - AMERICASTue 11 Mar 2025 @ 05:00 PM (CDT)
Under the Hood: Configuring Site to Site VPN with Azure Virtual WAN and CloudGuard Network SecurityWed 12 Mar 2025 @ 06:00 PM (IST)
TechTalk: The Future of Browser Security: AI, Data Leaks & How to Stay ProtectedTue 04 Mar 2025 @ 04:00 PM (CET)
Check Point | WIZ : Powering the Next Era of Cloud Security - AMERICASTue 11 Mar 2025 @ 05:00 PM (CDT)
Under the Hood: Configuring Site to Site VPN with Azure Virtual WAN and CloudGuard Network SecurityAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter