- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
CheckMates Fest 2025!
Join the Biggest Event of the Year!
Share your Cyber Security Insights
On-Stage at CPX 2025
Simplifying Zero Trust Security
with Infinity Identity!
Zero Trust Implementation
Help us with the Short-Term Roadmap
CheckMates Go:
What's New in R82
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Security Gateways
- :
- Received notification from peer: Traffic selectors...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
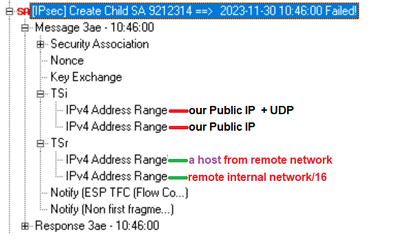
Received notification from peer: Traffic selectors unacceptable
Hello All,
we have a VPN Tunnel on 80.40 with third party Gateway. Almost everything is working, but sometimes some remote server becomes unreachble. During troubleshooting I found following message that repeats every minute:
Source: our VPN Gateway
Destination: remote VPN Gateway
Child SA exchange: Received notification from peer: Traffic selectors unacceptable
MyTSi - <our public IP>
MyTSr: <remote internal network/16>vpt tu tlist shows:
+-----------------------------------------+-----------------------+---------------------+
| Peer: remote Public IP - gateway name | MSA: 7f7f89890408 | i: 1 ref: 2 |
| Methods: ESP Tunnel PFS AES-256 SHA256..| | |
| My TS: our Public IP | | |
| Peer TS: remote internal network/16 | | |
| MSPI: 8000ab (i: 1, p: 0) | No outbound SA | |
+-----------------------------------------+-----------------------+---------------------+
Debug log:
The main question which is bothering me: who initializes this traffic - we or the remote server?
What does it mean "no outbound SA"? If it is incomming traffic why not to write "incoming SA"?
The first assumption the one remote host tries to reach our Gateway via its public IP, which is not in the encryption domain and refused Am I close?
Thank you in advance!
10 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To me, logically looking at this, would indicate there is a problem where remote peer does not accept your selectors, so definitely phase2 problem. Whats the other side? Fortinet, Cisco, Sonicwall, PAN...something else?
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Palo Alto
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I cant recall the wording now on PAN, but if theres something called peer ID, just remove it, as CP does not use that at all. For NAT, as @D_Schoenberger mentioned, if there is need for it, make sure its not disabled within the community and then create manual NAT rule(s).
Best regards,
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Palo Alto uses route-based VPNs by default, and will only accept an IKE Phase 2 proposal of 0.0.0.0/0 0.0.0.0/0 (a so-called "universal tunnel") unless special arrangements are made on the Palo side for it to mimic a domain/subnet-based VPN by configuring explicit Proxy-IDs. See here:
Gateway Performance Optimization R81.20 Course
now available at maxpowerfirewalls.com
now available at maxpowerfirewalls.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I dont believe thats totally accurate. In older versions of PAN, you could build domain based tunnels, but you are correct, in new versions, its only route based. As far as phase 2 selectors, I am 100% positive you can use regular subnets, not just 0.0.0.0/0, because I had seen customers do it and it works, and Palo Alto TAC verified the same as well.
Best regards,
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
it is not Route Based VPN for sure, but domain based.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I dont think that really matters in this context much.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When looking at a negotiation in IKEView, the "arrow" indicates who initiated.
==> means the local GW initiated
<== means the peer initiated
When looking at "vpn tu tlist", you'll sometimes see "No outbound SA" when IPSec negotiations have failed, but IKE succeeded. "vpn tu tlist" shows the outbound SA we use to encrypt traffic to the peer - it doesn't care which side initiated the negotiation.
Considering the peer is rejecting a proposal for the public IP of your gateway to their internal network, there is most likely have a Hide NAT configured on your internal network, and the peer is not configured to accept proposals from your public IP.
If this is an Automatic NAT (NAT configured on a host/network object directly), you can use the "Disable NAT inside the VPN community" setting under the "Advanced" settings of your VPN community. If you're using manual hide NAT rules, you'll need a no-NAT rule above your hide NAT rule.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
NAT is used only for Direct access, the Tunnel is standard - local Net | our VPN --- remote VPN | remote Net
But looks like one server tries something different and Remote VPN doesn't accept it. Maybe it uses NAT, thanks for idea, I wil lcheck it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I found in the FW Settings in Gaia, that the FW try to reach remote DNS and uses their external IP, which also presented in the debug. I've removed the DNS, but this traffic still going out... Are there any other places for DNS settings?
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 25 | |
| 11 | |
| 10 | |
| 10 | |
| 9 | |
| 8 | |
| 7 | |
| 5 | |
| 4 | |
| 4 |
Upcoming Events
Fri 10 Jan 2025 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 32: Infinity External Risk Management (CyberInt)Fri 10 Jan 2025 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 32: Infinity External Risk Management (CyberInt)About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter