- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Call For Papers
Your Expertise, Our Stage
Ink Dragon: A Major Nation-State Campaign
March 11th @ 5pm CET / 12pm EDT
AI Security Masters E4:
Introducing Cyata - Securing the Agenic AI Era
The Great Exposure Reset
AI Security Masters E3:
AI-Generated Malware
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Hybrid Mesh
- :
- Firewall and Security Management
- :
- Proxy ARP on GAIA
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Proxy ARP on GAIA
Hi community, I've tried to google the topic but didn't find the answer.
The question is why it is required to add the entries to the Proxy ARP on GAIA to make the NAT work? Is there a possibility to enable dynamic arp so that no configuration is required to make an public IP reachable?
Thanks, Harpreet S.
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you use Automatic NAT rules, the Proxy ARPs will be created for you.
Manual NAT rules still require proxy ARPs to be created.
In R80.x, automatic ARPs for Manual Source NAT rules can be created but this is not enabled by default.
See: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
Manual NAT rules still require proxy ARPs to be created.
In R80.x, automatic ARPs for Manual Source NAT rules can be created but this is not enabled by default.
See: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
17 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you use Automatic NAT rules, the Proxy ARPs will be created for you.
Manual NAT rules still require proxy ARPs to be created.
In R80.x, automatic ARPs for Manual Source NAT rules can be created but this is not enabled by default.
See: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
Manual NAT rules still require proxy ARPs to be created.
In R80.x, automatic ARPs for Manual Source NAT rules can be created but this is not enabled by default.
See: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you. sk114395 answer's what I was after.
Why the feature is not enable by default? For more security?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's a change from the default behavior which people are accustomed to, thus why it is not the default.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Harpreet,
ther's another way to add a proxy arp entry to a gateway without configuring via the GAiA portal.
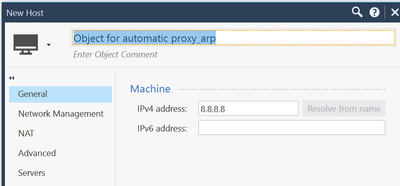
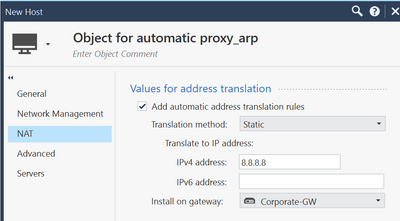
Add a host object with your external IP to your rulebase and configure automatic NAT (static). As NAT-IP use the same external IP, add the relevant gateway and do a policy install. With this host object the gateway adds an proxy arp entry to the the gateway.
Wolfgang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We create the specific NAT rules but trying to configure the object will be interesting. Thank you Wolfgang!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Wolfgang,
How do i validate the proxy arp has been created successfully after the below steps has been ?
Thanks
Nirvs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
On the cli of the gateway type: fw clt arp
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Wolfgang,
Will it work when Gateway external IP and NATED IP are from a different pool ??? I have tried to add the Proxy ARP entries as well but still unable to access the NATTEd server IP.
Please suggest.
Thanks,
CSR
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If they are from a different Pool/Subnet you would need to create a route that points to the firewall. ARP is not enough in this case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No -
You cant arp for a subnet that isnt attached to the actual interface. How would it route?
What are you trying to do?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Let say you real external interface IP is 10.10.10.2
Mac address of external interface is 00:AC:00:AC:00:AC
You are trying to use 20.20.20.2 a NAT IP for one of internal hosts.
So your local.arp should look like :
20.20.20.2 00:AC:00:AC:00:AC 10.10.10.2
In GAiA web UI you have a way to configure that
To validate run fw ctl arp
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I know this is an old post, but personally, I see LOTS of customers using manual static nats and we never had to do proxy arp either in clish or web GUI. Its possible this was more needed pre R80, but I dont see if often any more.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It depends on where the NAT IP address for manual static NAT comes from.
If they are "plucked" from an directly attached network adjacent to the firewall (such as the "dirty" segment between the firewall's external interface and the Internet perimeter router), a manual static proxy ARP must be created on the firewall. If however the NAT address is taken from a separate subnet that is explicitly routed to the firewall over a transit network (such as the dirty segment) then proxy ARP is not required, as the Internet perimeter router must already have a static route for that separate NAT subnet and will send traffic bound for it directly to the firewall as the next hop.
New Book: "Max Power 2026" Coming Soon
Check Point Firewall Performance Optimization
Check Point Firewall Performance Optimization
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Honestly, I never see people having to do this regardless where traffic comes from. Many times, even TAC is confused whether it should be done or not...
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think I need some help as to 'if' a static ARP is going to be needed, after reading this.
Here's my scenario (IP's and interfaces are made up)
I have a site to site VPN with traffic being both source and destination natted. The destination device 10.100.100.1 is on a valid network segment routed on the inside of the firewall on interface ETH1.
Source device 202.15.15.1 this is source natted to 10.200.200.1
Destination 202.16.16.1 which is destination natted to 10.100.100.1
Traffic arrives to the cluster on interface ETH0. (207.195.233.1 cluster with .4 and .5 for the cluster members. The point to point VPN is operational and traffic is flowing - most of the time.
My actual issue relates to the VPN not re-establishing when the cluster fails over to the secondary member. It has been suggested that proxy ARP entries are created as it might help.
So my configuration would be:
add arp proxy ipv4-address 10.100.100.1 interface ETH0 real ipv4-address 207.195.233.4 (on member 1, and .5 on member 2).
Two questions then.
1) do I have the configuration line correct in terms of the IP addresses to achieve the desired result, adding the natted destination address?
2) As the 10.100.100.1 network is valid and routed is the proxy arp actually needed?
Thanks Matt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ARP (proxy or otherwise) can only be configured for IP addresses on the same subnet.
Therefore, you can only do a proxy arp (meaning the gateway will respond to ARP requests for this IP address) if the address in question is on the same subnet as one of the firewall interfaces.
Also, proxy arps in general are created automatically by the gateway when NAT rules are created.
One almost never has to actually create these anymore.
What you're describing sounds like an issue where other devices on the same subnet don't know which member currently has the VIP.
That sounds like issues related to gratuitous ARP: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
We send these by default on failover, but it sounds like other things on the network aren't updating their ARP tables in response (as they should).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for that most excellent response! I do think the issue is tied to GARP, though have been looking into all suggestions. I think I shall proceed through resolving the GARP issue first as opposed to doing both.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 31 | |
| 19 | |
| 13 | |
| 11 | |
| 9 | |
| 8 | |
| 6 | |
| 6 | |
| 5 | |
| 5 |
Upcoming Events
Tue 03 Mar 2026 @ 04:00 PM (CET)
Maestro Masters EMEA: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 03:00 PM (EST)
Maestro Masters Americas: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 04:00 PM (CET)
Maestro Masters EMEA: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 03:00 PM (EST)
Maestro Masters Americas: Introduction to Maestro Hyperscale FirewallsFri 06 Mar 2026 @ 08:00 AM (COT)
Check Point R82 Hands‑On Bootcamp – Comunidad DOJO PanamáTue 24 Mar 2026 @ 06:00 PM (COT)
San Pedro Sula: Spark Firewall y AI-Powered Security ManagementAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter