- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Planning to deploy a backup center firewall
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Planning to deploy a backup center firewall
Hello,
My customer is planning to deploy a backup center firewall.
The customer wants to manage two firewalls from one management server.
But these two firewalls have the same IP address.
These firewalls use 5 interfaces each and the IP addresses of 4 interfaces are identical (only the mgmt port IP addresses are different).
Firewall A is the main center firewall and Firewall B is the backup center firewall.
The customer wants this configuration to completely synchronize the security policies of the two firewalls.
Is there any problem if I configure it like this?
(Central management of two firewalls with the same IP address)
14 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think it can work as long as you specify the unique IPs as the main IPs on each gateway. You won't be able to do VPNs though.
It's not a recommended configuration, and you may run into issues caused by this that are not resolvable.
The gateways won't synchronise anything but you don't need gateways to have the same IPs on their interfaces to install the same policy on both of them.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you very much for your reply.
The reason two gateways have the same IP address is because of the customer's network environment. (I don't want this configuration.)
I plan to place one management server in the main center and one management server in the backup center and configure HA for these two management servers.
And this HA management server tries to manage the firewalls deployed in each center (main center, backup center). But these two firewalls have the same IP address. The goal is to install the same daily updated security policy on each firewall of both centers.
Each firewall in these two centers will always have the same security policy.
Therefore, even if a failure occurs in the main center, the backup center firewall will be able to enforce the latest security policy.
This is the configuration my customers want.
Are there any other configuration options that could solve the customer's needs?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It depends. It sounds like the DCs are reusing all the same subnets, but they are not stretched between them? We need to better understand why there is a requirement to use the same interface IP addresses on both sides.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
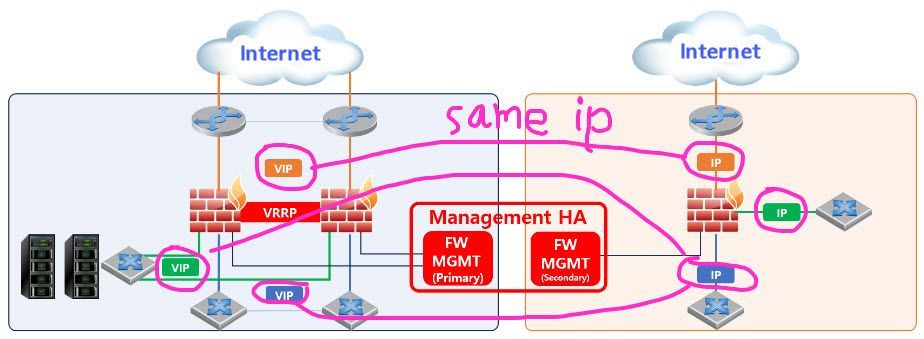
Why not use Cluster XL in the supported configuration ? This is HA and syncs all connections, having the same policy and a common VIP on all the IFs. https://sc1.checkpoint.com/documents/R81.10/WebAdminGuides/EN/CP_R81.10_ClusterXL_AdminGuide/Topics-...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My customer has been using Check Point firewalls for a very long time. They have been using the VRRP configuration for a long time and have experience with its stability.
My guess is that they probably don't want to change the network configuration for this reason. But I can change their minds if necessary.
Currently, there are no problems with VRRP settings.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have a few questions, almost none of which involve Check Point:
- Your primary site appears to have a cluster and the backup has a single gateway...do I understand this correctly?
- Is there a non-Internet connection between the two datacenters?
- What mechanism will be used to ensure the relevant IP is routed to the correct datacenter? BGP?
I recommend engaging with your local Check Point SE with more specifics to validate the proposed configuration, which I suspect will be very problematic.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Your primary site appears to have a cluster and the backup has a single gateway...do I understand this correctly?
That's correct. The main center has two firewalls configured with VRRP. The backup center is a single firewall, and we will set the VIP of the main center firewall to be the same as the real IP of the backup center single firewall. - Is there a non-Internet connection between the two datacenters?
This part of the network information is currently being designed.
Normally, traffic will only pass through the main center's firewall.
If a problem occurs at the main center, traffic will be routed to the backup center. - What mechanism will be used to ensure the relevant IP is routed to the correct datacenter? BGP?
I'm planning to talk to the customer's network administrator about this.We are in discussions with Check Point Local SE.
If the customer selects Palo Alto, it is said that this issue can be clearly resolved by using panorama.
We need to get answers to our customers as quickly as possible.Since they are already using Check Point products, it is likely that Check Point will be selected at this time. But we cannot rest assured.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Im not expert in Palo Alto by any means, been some time since I worked on it, but how can Panorama solve the routing issue you mentioned? Panorama is Palo Alto's version of CP management server, does not really do any routing, its simply there for managing palo alto firewalls and pushing changes to the same.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Panorama can manage two firewalls with the same IP configuration.
Routing issues will be designed by a network designer to ensure that there are no problems.
Is there any problem with the CheckPoint management server managing two firewalls with the same IP configuration?
A long time ago, in the old version, I saw an SK case where unexpected problems occurred when managing two firewalls with the same IP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If thats true, thats news to me for Panorama, never heard of it before. Can it be done with Check Point? I have no clue, as I never tested myself. Logically, I dont see how that would work.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CP can do it (with some caveats, such s VPN issues I mentioned before), if they have different Mgmt IPs, but there's still no good reason for it. If it's just a routing change, there's still no need to reuse the same IPs on the backup site. If the VLANs are stretched between the two sites, you can have a 3-node ClusterXL cluster. If the sites are isolated, sharing IP addressing between the two is just making life hard for yourself.
Also the recommended clustering tech from Check Point is ClusterXL, VRRP is considered legacy. In R82 we will be introducing a new clustering tech, ElasticXL.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
From a management perspective, each managed gateway needs to have a unique IP; specifically the Main IP in the General tab of the relevant object.
For ClusterXL/VRRP clusters members, management pushes policy to each cluster member independently using the member objects Main IPs.
Assuming you use the Management IP for the backup DC gateway (which is unique), that would mean all three gateways can be managed using unique IPs.
That should work, but I would thoroughly test this in the lab first.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you all.
I received a reply from Local SE that this configuration is possible.
thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Definitely keep us posted if you make it work and how it was done.
Best,
Andy
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 10 | |
| 10 | |
| 9 | |
| 7 | |
| 5 | |
| 5 | |
| 4 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter