- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- OSPF Not Coming Up - Showing Auth Error
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OSPF Not Coming Up - Showing Auth Error
I am working to bring the ospf, Look like it is throwing Auth error all the time. I doubt at the checkpoint side I am missing something.
What could be the issue ? It is a new setup and there are no SmartDash Board Server Installed at the moment. Plan was to make the OSPF Connectivity. At the moment there are no initial rules at this Firewall. So accepting all traffic.
Debug log from cisco Side ( which is other side of the ospf neighbor ).
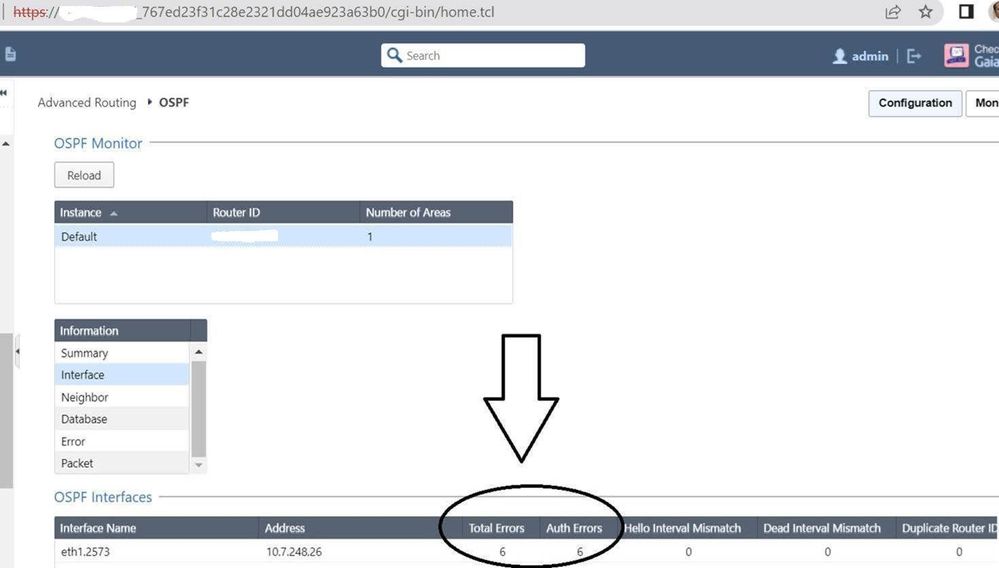
Jun 23 10:52:42.860 AST-Sum: OSPF-1 ADJ Vl2573: Rcv pkt from 10.7.248.26 : Mismatched Authentication key - ID 3.
Cisco Side OSPF Config
interface Vlan2573
description XXXXXXXXXXXXXX
ip address 10.7.248.25 255.255.255.252
ip ospf authentication message-digest
ip ospf message-digest-key 3 md5 7 XXXXXXXX
11 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If there are no initial rules on the firewall, you are actually dropping all traffic, including OSPF:
From Admin Guide: "Until the Security Gateway administrator installs the Security Policy on the Security Gateway for the first time, security is enforced by an Initial Policy.
The Initial Policy operates by adding the predefined implied rules to the Default Filter policy.
These implied rules forbid most communication, yet allow the communication needed for the installation of the Security Policy. The Initial Policy also protects the Security Gateway during Check Point product upgrades, when a SIC certificate is reset on the Security Gateway, or in the case of a Check Point product license expiration."
To allow OSPF until policy is configured and installed:
Execute "fw unloadlocal" in expert mode on this gateway, IF IT IS NOT in production, to actually remove the default policy.
If you need for routing to work while in wide-open state, execute "echo 1 > /proc/sys/net/ipv4/ip_forward"
That last one is actually courtesy of @Timothy_Hall .
To properly configure your policy for OSPF, see sk39960.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Vladimir is 100% right. You NEED rules to allow ospf, period.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thank you for your reply.
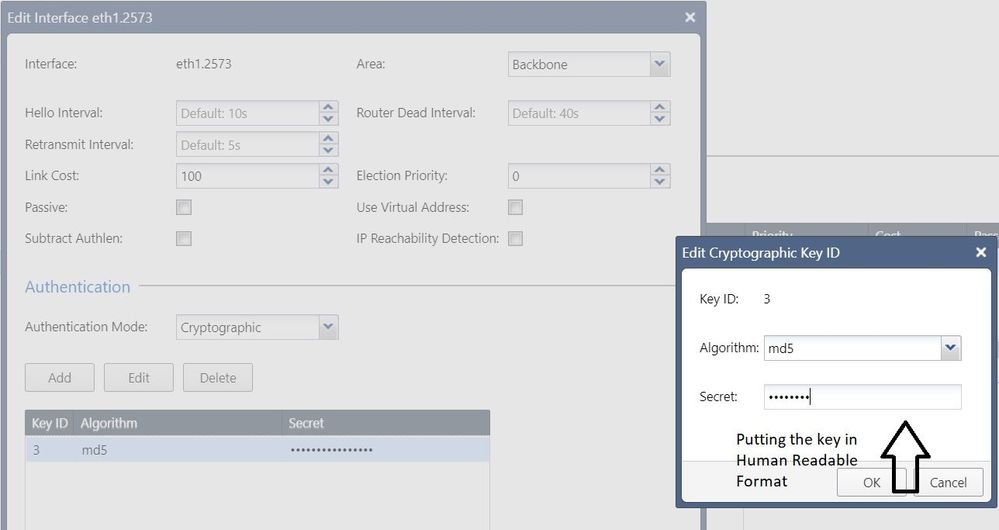
I used "fw unloadlocal" so I dont think OSPF is getting blocked. As I shared earlier it is throwing Auth Error. ( image attached before )
FW# cpstat -f policy fw
Product name: Firewall
Policy name:
Policy install time:
Num. connections: 0
Peak num. connections: 0
Connections capacity limit: 0
Total accepted packets: 0
Total dropped packets: 0
Total rejected packets: 0
Total accepted bytes: 0
Total dropped bytes: 0
Total rejected bytes: 0
Total logged: 0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hmm...
I'm a bit surprised to see the packet counters at 0.
That said, there used to be issue in R77.30 days specific to OSPF auth due to mtu missmatch, sk109092.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hello @Vladimir
My version is R80.40. Will check to see if enabling Subtract Authlen resolves the issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Which version & jumbo is this Gateway installed with?
(Note OSPF network type point-to-point isn't supported if set on the Cisco side).
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Chris,
Cisco side is not P2P OSPF.
Cisco Side OSPF Config
interface Vlan2573
description XXXXXXXXXXXXXX
ip address XX.XX.XX.XX 255.255.255.252
ip ospf authentication message-digest
ip ospf message-digest-key 3 md5 7 XXXXXXXX
CP Version is 80.40 and Build is 309
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To clarify you already have the latest GA jumbo installed (JHF T158)?
What's the password complexity like, have you experimented with something simple?
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @Chris_Atkinson
After setting key with a 16 character one it got resolved. 8)
To clarify you already have the latest GA jumbo installed (JHF T158)? -- I do not know how to check this. Can you suggest ?
Thanks for your intention to constantly trying to help me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you need to check anything, I got working ospf/bgp in the lab on latest R81.10 jumbo 61 version, so happy to show you.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Glad it's resolved.
From the CLI in Expert mode on the Gateway: "cpinfo -y all"
This should output the currently installed hotfix level information.
CCSM R77/R80/ELITE
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 12 | |
| 11 | |
| 10 | |
| 7 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 4 | |
| 3 |
Upcoming Events
Fri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter