- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: IPsec VPN [NATting intresting traffic] config ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
IPsec VPN [NATting intresting traffic] config help
I hope you all are doing well. After googling stuffs and reading blogs this is the first time i am configuring IPSec VPN on CP. But couldn't succeed. I want to establish IPSec VPN between CP and Palo Alto. I have all configs in place on PA and have same P1 & P2 algorithms setting on both FW. But my tunnel is not coming up.
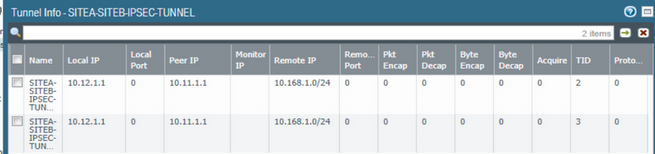
On CP side: Original IP is 192.168.1.10 --> static NAT to 10.168.1.1 when it goes over tunnel to PA side.
CP eth1 IP is : 10.11.1.1
PA eth1/2 IP is :10.12.1.1
My underlay routing has no issues. Though i cannot ping from PA eth1/2 interface but i can ping from R12 e6/2 interface to CP eth1 interface. I have disabled address spoofing and allowed ping.
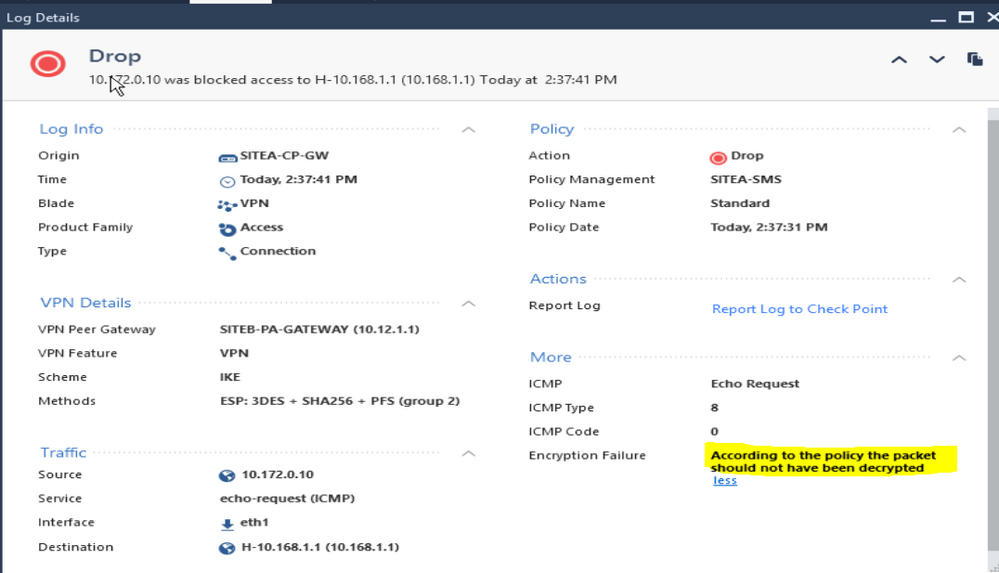
While pinging from PA, CP logs shows as "Clear text packet should be encrypted"
Could some one please help me with config i am missing here ?
BELOW URL HAS TOPOLOGY DIAGRAM:

 https://imgurupload.org/files/DFB83F1F-9386-43C0-9D6E-4FCB45D7F95F.jpeg
https://imgurupload.org/files/DFB83F1F-9386-43C0-9D6E-4FCB45D7F95F.jpeg
CONFIG SNAP:
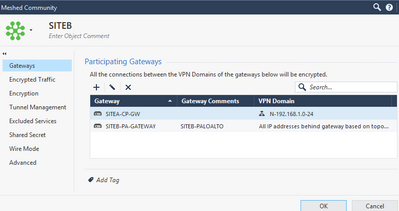
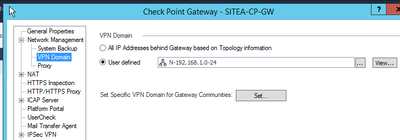

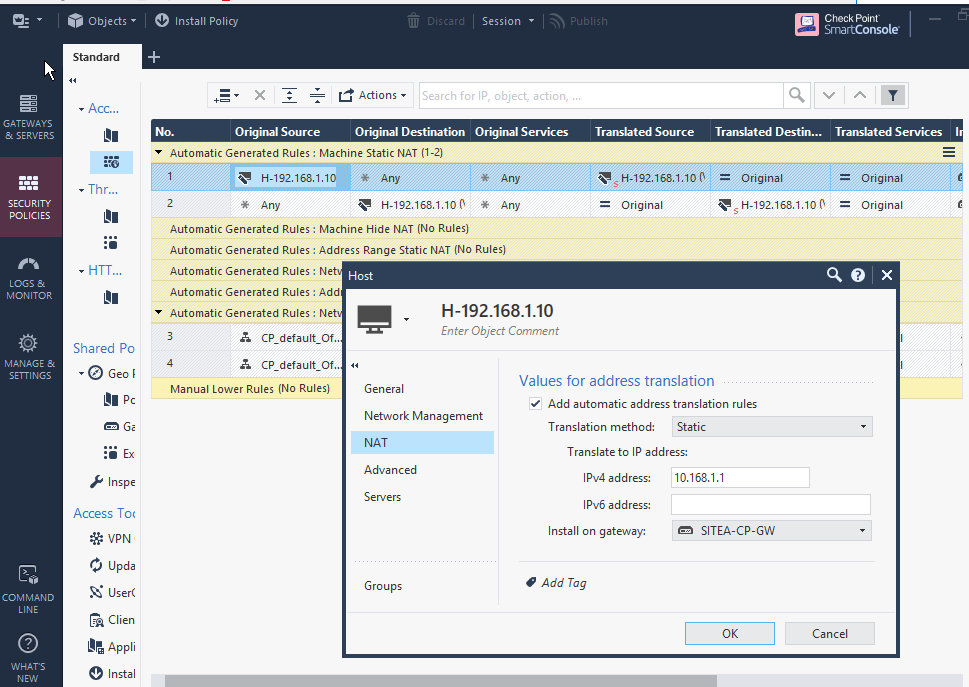
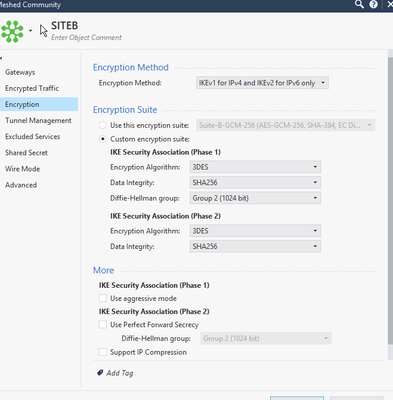
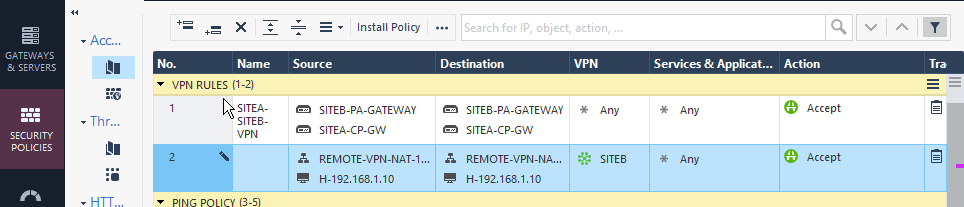
Thanks in advance
Labels
- Labels:
-
Site to Site VPN
14 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The reason you’re getting the clear text packet should be encrypted is Scenario 3 here: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
When you say the tunnel is not coming up, what precisely do you see or don’t see?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@PhoneBoy Thankyou for taking out your precious time and replying. I have made a .docx file. Please find it attached here. It contain all screenshot . I have been troubleshooting this since 2 days now, but couldn't figure figure out the missing/incorrect thing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Remove the blackhole routes you've configured.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@PhoneBoy Blackhole route removed
From PA i initiated tunnel , below are the logs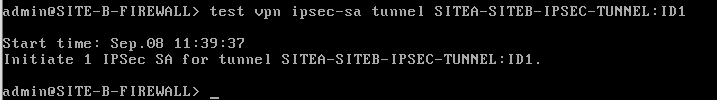
.
ON CP (below output is when i initiated tunnel from PA)
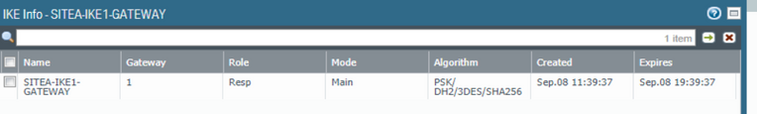
SITEA-GW> vpn tu
********** Select Option **********
(1) List all IKE SAs
(2) * List all IPsec SAs
(3) List all IKE SAs for a given peer (GW) or user (Client)
(4) * List all IPsec SAs for a given peer (GW) or user (Client)
(5) Delete all IPsec SAs for a given peer (GW)
(6) Delete all IPsec SAs for a given User (Client)
(7) Delete all IPsec+IKE SAs for a given peer (GW)
(8) Delete all IPsec+IKE SAs for a given User (Client)
(9) Delete all IPsec SAs for ALL peers and users
(0) Delete all IPsec+IKE SAs for ALL peers and users
* To list data for a specific CoreXL instance, append "-i <instance number>" to your selection.
(Q) Quit
*******************************************
1
Peer 10.12.1.1 , SITEB-PA-GATEWAY SAs:
IKE SA <3b9a97149bc884dd,edfb6f9b1501ee78>
2
SAs of all instances:
Peer 10.12.1.1 , SITEB-PA-GATEWAY SAs:
IKE SA <1586026f8eeeba33,bdafb0a3bbc94399>
(No IPSec SAs)
But ping didn't work from either end.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
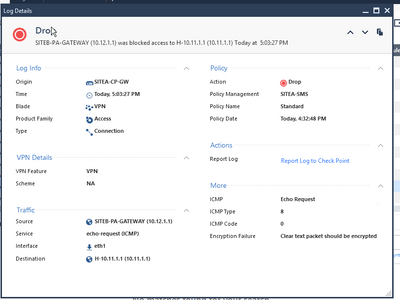
I am almost close to achieve this task.
Now i am getting below log
I found below code on CP community and i ran it, below is the output.
[Expert@SITEA-GW:0]# if [[ `$CPDIR/bin/cpprod_util FwIsFirewallModule 2>/dev/nul l` != *'1'* ]]; then echo; tput bold; tput setab 1; echo ' Not a firewall gatewa y! '; tput sgr0; echo; else if [[ `grep R80.40 /etc/cp-release | wc -l` != 0 ]]; then echo; tput bold; tput setab 1; echo -n ' Info: VPN Domain for Gateway Comm unities are currently not displayed correctly by this tool! '; tput sgr0; echo; fi; fw tab -t vpn_routing -u | awk 'NR>3 {$0=substr($0,2,28); gsub(", ", ""); gs ub("; ", ""); gsub("..", "0x& "); print}' | xargs printf "%d.%d.%d.%d %d.%d.%d.% d %d.%d.%d.%d\n" | awk '{print $3"."$1" - "$2}' | sort -t . -k 1,1n -k 2,2n -k 3,3n -k 4,4n -k 5,5n -k 6,6n -k 7,7n -k 8,8n | sed 's/^/x/' | sed 's/\./\n\t/4' | awk '!x[$0]++' | sed '/x/s/$/\n\tEncryption domain/' | sed 's/x/\nVPN Gateway > /' | if [[ $(cat /etc/cp-release) != *"Embedded"* ]]; then egrep -C 9999 --col or=auto $'VPN Gateway|Encryption domain'; else cat $1 | sed 's/^\t//'; fi; echo; fi; if [[ `grep R80.40 /etc/cp-release | wc -l` != 0 ]]; then tput bold; tput s etab 1; echo -n ' Info: VPN Domain for Gateway Communities are currently not dis played correctly by this tool! '; tput sgr0; echo; echo; fi
Info: VPN Domain for Gateway Communities are currently not displayed correctly by this tool!
VPN Gateway > 10.12.1.1
Encryption domain
10.12.1.1 - 10.12.1.1
10.172.0.0 - 10.172.0.255
VPN Gateway > 192.168.1.1
Encryption domain
10.11.1.0 - 10.11.1.0
10.11.1.1 - 10.11.1.1
10.11.1.2 - 10.11.1.63
192.168.0.253 - 192.168.0.253
192.168.1.0 - 192.168.1.0
192.168.1.1 - 192.168.1.1
192.168.1.2 - 192.168.1.255
Info: VPN Domain for Gateway Communities are currently not displayed correctly by this tool!
[Expert@SITEA-GW:0]#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You usually get this error with mismatches in encryption domains(interesting traffic). In your VPN Community I can see that you have defined the EncDom for Palo Alto as "All IP Adresses behind this gateway according to topology". What does the topology look like? If the 10.172.0.10 is not within the topology of the Palo Alto GW on CheckPoint side, your CP will not see it as part of the encryption domain/interesting traffic.
What I would do: Create a Network Group, put the Subnets from PA that you want to be part of the tunnel into the network group and set the Network group as your encryption domain for the PA gateway.
I am also not sure if you are missing the CP NAT Subnet in the encryption domain on the CP side. As I can see, you have 192.168.1.0/24 defined as your encryption domain - but since you NAT it, the interesting traffic will actually be the NATed Subnet. Not sure if the NAT Subnet suffices in the encryption domain or if you need the 192.168.1.0/24 aswell.
Hope this helps!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@796570686578 i currently have this. Is it possible to add multiple subnet in encryption domain? i will try adding original and natted subnet and see if it works. PFA for encryption domain
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, yes exactly you can add multiple subnet in the Encryption domain by creating a Network Group object, adding subnets to that network group and then setting the network group object as the encryption domain!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Nick_Shah is 100% right and also, I will throw in what I find to be config that usually works. As Nick said, add a group with all the networks you want participating in VPN and also, as far as NAT, if its supposed to take place within VPN, make sure option is checked within VPN community and also, ensure that if there are networks where nat is not supposed to take place among them, create manual nat rule to reflect that.
Hope that helps.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Indeed !! that worked, i added original and natted subnet (192.168.1.0 & 10.168.1.0/24 under object group and added that group in encryption domain. Checkpoint is bit tricky to understand/troubleshoot.
@the_rock @796570686578 @PhoneBoy Thankyou everyone for your contribution, it really helped me to understand the ipsec with nat on CP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thats what so great about websites like this. No matter the issue, there is always going to be someone that can help you and give suggestions. Glad it worked! But yes, CP can be a bit tricky, specially for someone new, as many things can involve modifications you might not be accustomed to when working with other vendors. Personally, I would say thats mostly due to the fact that everything is mostly controlled by management server, where with other vendors, thats not necessarily the case.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@the_rock I am very sorry to bother you again. Though ping from PA to CP is working fine, but CP to PA is failing. NAT and Security policies are correctly configured. I tried deleting phase 1 and 2 and reinitiated tunnel from CP. Phase 1 came up but phase 2 shows below
2
SAs of all instances:
Peer 10.12.1.1 , SITEB-PA-GATEWAY SAs:
IKE SA <fef1591def15bc75,e45b67b52d88ed60>
(No IPSec SAs)
other troubleshooting snaps attached
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
K, message me privately, we can do remote in the morning if that works? Im in EST time zone
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The sk phoneboy mentioned honestly, is by far, your article number 1 when troubleshooting any sort of VPN issue with Check Point. Scenario 3 definitely matches your description.
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 17 | |
| 13 | |
| 8 | |
| 7 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter