Hi,
We deployed a relatively simple Check Point vSec security gateway as the perimeter firewall for a VoIP provider utilising SIP. Public IPs are routed directly to the servers so the only NAT rules apply to VPN clients.
We have an ongoing case with TAC regarding SecureXL not forwarding traffic on kernel 3.10, hence the gateway being R80.30 kernel 2.16.18. We have Jumbo Hotfix Accumulator take 50 installed, as the most recent GA release.
Architecture:
- VoIP server in VLAN with gateway pointing at Check Point security gateway
- Check Point security gateway has eth0 as internet upstream and eth1 in VoIP server VLAN
- vSec gateway managed by external MDS environment is non-publicly routed subnet (management via eth0)
What we've done thus far:
- Changed protocol objects to not reference SIP, disabling protocol inspection.
- Firewall blade policy set to use custom udp service object, rule 8.3
- Application and URL filtering blade policy set to allow all inbound (rule 1) and all outbound traffic originating from VoIP servers using custom udp service object, rule 8.1
- Threat Prevention policy exceptions have been defined
- Disabled Hyper Threading on the VM host and pinned guest VM cores to reserved physical cores, on CPU1 (attached to network interfaces)
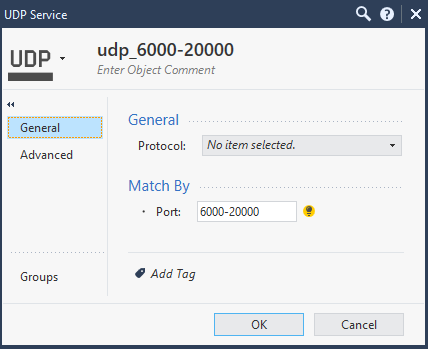
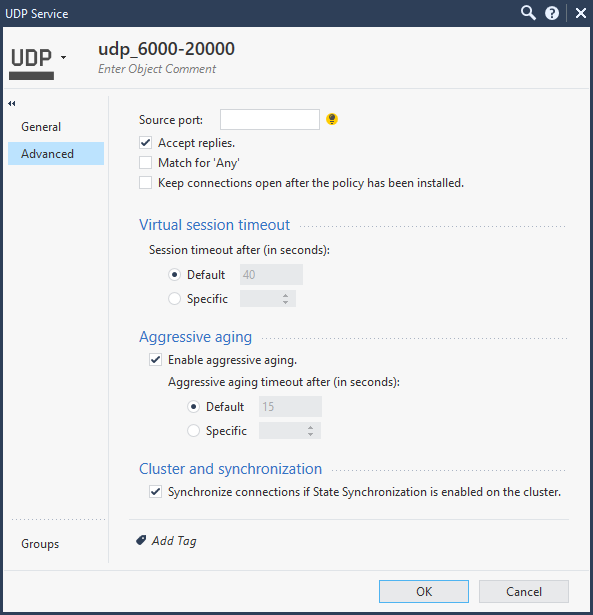
SIP RTP media udp service object details:
Network (Firewall) blade policy layer:
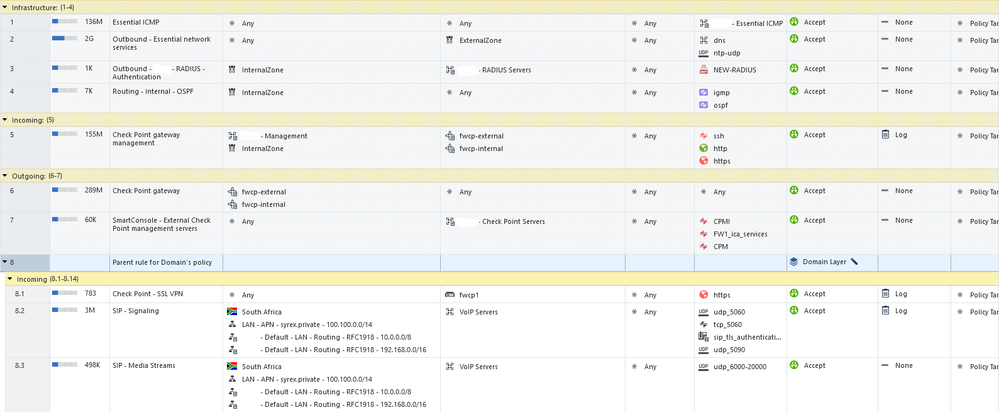
Application (Applications & URL Filtering) blade policy layer:
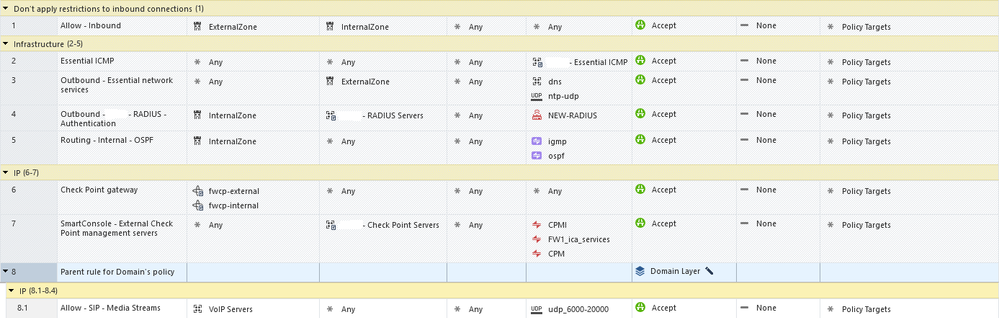
Threat Prevention - Exceptions blade policy layer:
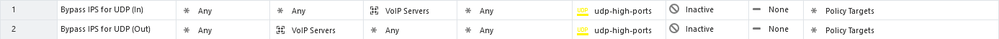
SecureXL stats:
[Expert@fwcp1:0]# fwaccel stat
+-----------------------------------------------------------------------------+
|Id|Name |Status |Interfaces |Features |
+-----------------------------------------------------------------------------+
|0 |SND |enabled |eth0,eth1 |Acceleration,Cryptography |
| | | | |Crypto: Tunnel,UDPEncap,MD5, |
| | | | |SHA1,NULL,3DES,DES,CAST, |
| | | | |CAST-40,AES-128,AES-256,ESP, |
| | | | |LinkSelection,DynamicVPN, |
| | | | |NatTraversal,AES-XCBC,SHA256 |
+-----------------------------------------------------------------------------+
Accept Templates : enabled
Drop Templates : enabled
NAT Templates : enabled
[Expert@fwcp1:0]# fwaccel stats -s
Accelerated conns/Total conns : 10/1882 (0%)
Accelerated pkts/Total pkts : 2199407627/4400568146 (49%)
F2Fed pkts/Total pkts : 6510799/4400568146 (0%)
F2V pkts/Total pkts : 3514127/4400568146 (0%)
CPASXL pkts/Total pkts : 0/4400568146 (0%)
PSLXL pkts/Total pkts : 2194649720/4400568146 (49%)
QOS inbound pkts/Total pkts : 0/4400568146 (0%)
QOS outbound pkts/Total pkts : 0/4400568146 (0%)
Corrected pkts/Total pkts : 0/4400568146 (0%)
[Expert@fwcp1:0]# fwaccel stats
Name Value Name Value
---------------------------- ------------ ---------------------------- ------------
Accelerated Path
--------------------------------------------------------------------------------------
accel packets 2199474632 accel bytes 255604723479
outbound packets 2199468895 outbound bytes 255661260470
conns created 3331162 conns deleted 3329257
C total conns 1905 C TCP conns 29
C non TCP conns 1876 nat conns 0
dropped packets 26624 dropped bytes 2028392
fragments received 1280 fragments transmit 4
fragments dropped 0 fragments expired 0
IP options stripped 63 IP options restored 63
IP options dropped 0 corrs created 0
corrs deleted 0 C corrections 0
corrected packets 0 corrected bytes 0
Accelerated VPN Path
--------------------------------------------------------------------------------------
C crypt conns 0 enc bytes 0
dec bytes 0 ESP enc pkts 0
ESP enc err 0 ESP dec pkts 0
ESP dec err 0 ESP other err 0
espudp enc pkts 0 espudp enc err 0
espudp dec pkts 0 espudp dec err 0
espudp other err 0
Medium Streaming Path
--------------------------------------------------------------------------------------
CPASXL packets 0 PSLXL packets 2194716725
CPASXL async packets 0 PSLXL async packets 2194691770
CPASXL bytes 0 PSLXL bytes 253353244667
C CPASXL conns 0 C PSLXL conns 1895
CPASXL conns created 0 PSLXL conns created 3330706
PXL FF conns 0 PXL FF packets 0
PXL FF bytes 0 PXL FF acks 0
PXL no conn drops 0
Inline Streaming Path
--------------------------------------------------------------------------------------
PSL Inline packets 0 PSL Inline bytes 0
CPAS Inline packets 0 CPAS Inline bytes 0
QoS Paths
--------------------------------------------------------------------------------------
QoS General Information:
------------------------
Total QoS Conns 0 QoS Classify Conns 0
QoS Classify flow 0 Reclassify QoS policy 0
FireWall QoS Path:
------------------
Enqueued IN packets 0 Enqueued OUT packets 0
Dequeued IN packets 0 Dequeued OUT packets 0
Enqueued IN bytes 0 Enqueued OUT bytes 0
Dequeued IN bytes 0 Dequeued OUT bytes 0
Accelerated QoS Path:
---------------------
Enqueued IN packets 0 Enqueued OUT packets 0
Dequeued IN packets 0 Dequeued OUT packets 0
Enqueued IN bytes 0 Enqueued OUT bytes 0
Dequeued IN bytes 0 Dequeued OUT bytes 0
Firewall Path
--------------------------------------------------------------------------------------
F2F packets 6510843 F2F bytes 4112863976
TCP violations 9 F2V conn match pkts 13981
F2V packets 3514178 F2V bytes 1410988147
GTP
--------------------------------------------------------------------------------------
gtp tunnels created 0 gtp tunnels 0
gtp accel pkts 0 gtp f2f pkts 0
gtp spoofed pkts 0 gtp in gtp pkts 0
gtp signaling pkts 0 gtp tcpopt pkts 0
gtp apn err pkts 0
General
--------------------------------------------------------------------------------------
memory used 792 C tcp handshake conns 0
C tcp established conns 25 C tcp closed conns 4
C tcp pxl handshake conns 0 C tcp pxl established conns 25
C tcp pxl closed conns 4 outbound cpasxl packets 0
outbound pslxl packets 0 outbound cpasxl bytes 0
outbound pslxl bytes 0 DNS DoR stats 0
(*) Statistics marked with C refer to current value, others refer to total value
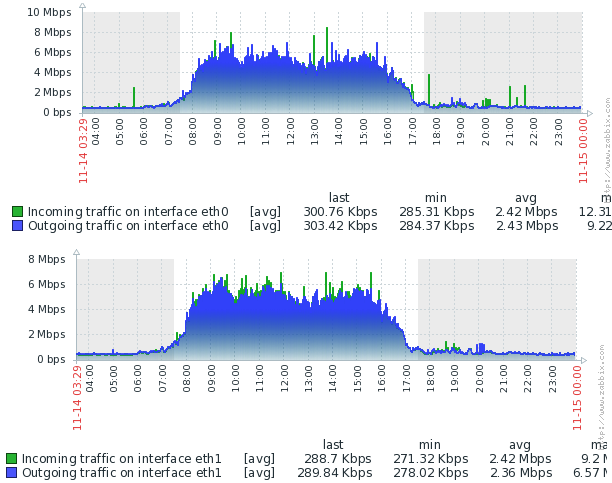
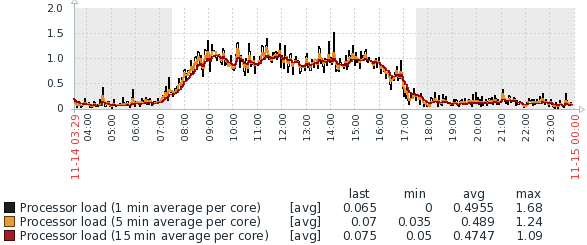
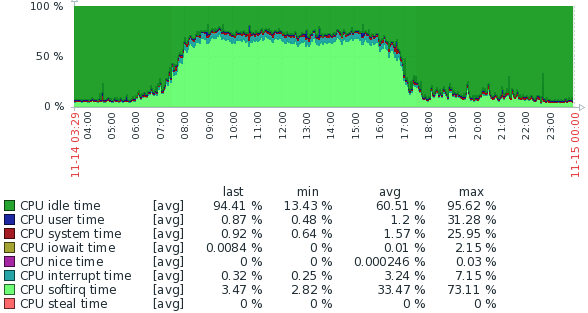
Resource utilisation is very high, with two CoreXL instances and only 6 Mbps traffic:
|------------------------------------------------------------------------------|
| CPVIEW.Overview 15Nov2019 9:42:49 |
|------------------------------------------------------------------------------|
| Overview SysInfo Network CPU I/O Software-blades Hardware-Health Advanced |
|------------------------------------------------------------------------------|
| CPU: |
| |
| Num of CPUs: 2 |
| |
| CPU Used |
| 0 93% |
| 1 58% |
| ---------------------------------------------------------------------------- |
| Memory: |
| |
| Total MB Used MB Free MB |
| Physical 3,815 1,842 1,973 |
| FW Kernel 3,052 785 2,267 |
| Swap 4,095 0 4,095 |
| ---------------------------------------------------------------------------- |
| Network: |
| |
| Bits/sec 8,950K |
| Packets/sec 15,889 |
| Connections/sec 17 |
| Concurrent connections 1,931 |
| ---------------------------------------------------------------------------- |
| Disk space (top 3 used partitions): |
| |
| Partition Total MB Used MB Free MB |
| / 15,558 6,323 8,521 |
| /boot 288 23 250 |
| /var/log 19,806 876 17,908 |
| ---------------------------------------------------------------------------- |
| Events: |
| |
| # of monitored daemons crashes since last cpstart 0 |
| |
|------------------------------------------------------------------------------|
Load average:
CPU utilisation:
Network throughput: