- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- How to configure External interface in Clusterxl
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to configure External interface in Clusterxl
Please help to understand how to configure internet facing interface in #Clusterxl and also Clusterxl with ISP redundancy
Scenario 1: Clusterxl high availability 14 Public IP from ISP
Scenario 2 : Clusterxl high availability 14 Public IP from 2 separate ISP ( #ISP_Redundancy )
10 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Assuming your ISP allocated you a /28 (14 addresses after you exclude the network and broadcast), you're going to need 3 IP addresses: one for each cluster member, and one for the VIP for ClusterXL.
I presume the ISP's default router will also take one of those IP addresses (as the default route).
Both cluster members will be configured to use that default route.
In any case, this along with the ISP Redundancy requirement should be a fairly standard configuration covered by the Product Documentation: ClusterXL R80.10 (Part of Check Point Infinity)
If you have specific questions after reading the docs and can provide more details about your proposed configuration, feel free to ask.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Dameon ,
I have followed your instruction but not sure about default gateway and static NAT . Also, I am confused about the ISP redundancy faileover , The faileover will happen in the same Firewall or faileover to standby firewall ?
Default Gateway :
For each member what default gateway should configure? (ClusterXL mode)
NAT :
For static NAT to a web server ( static NAT to one of the IP of /28 NOT firewall IP ) do I need to create alias for each IP address and assign to Firewall external address ?
How should I configure static NAT for clusterxl in ISP redundancy ?
Thanks in advance for your help .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ISP Redundancy is local to the specific gateway.
In a cluster it should be configured on both members.
The default route should be your primary ISPs next hop IP (again, configured on both members).
For NAT, you do not need to create that static IP as an alias, you merely need to make a rule in the NAT rulebase.
You can have multiple public IPs (for the different ISP links) for your webserver.
This specific example is covered in the documentation: How To Configure ISP Redundancy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for your reply .
if Default gateway configured as primary and primary Internet failed how firewall will handle the secondary ISP route ?
(in cluster object I have enabled the USO redundancy as primary/backup mode with next hop IP address but not sure I have to add default gateway or not in gui static route or not )
Also,The static NAT to my web server is not working without creating an aliases !!!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you very much Dameon .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hello
I configured cluster in R80.10 distributed configuration. our ISP switch port is trunk mode. how will i configure trunk in external interface. i read if i add vlan 10 in eth1 . trunk is automatic added in eth1. my problem isn't working in external trunk port interface. how will i configure trunk in cluster external interfaces ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Basically you treat each VLAN as if it were a physical interface.
This means:
- In Gaia, after adding the relevant VLANs to eth1, configure the networking for each VLAN as appropriate.
- Note it's generally not best practice for the physical (non VLAN) interface to have an IP once you start using VLANs on a given physical interface.
- In SmartConsole, gateway and cluster objects, you will see each VLAN show up as an independent interface when you do a Get Topology. Configure each VLAN as appropriate. Ensure each VLAN has a cluster IP.
Note also about the following limitation when using VLANs with ClusterXL: Monitoring of VLAN interfaces in ClusterXL
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
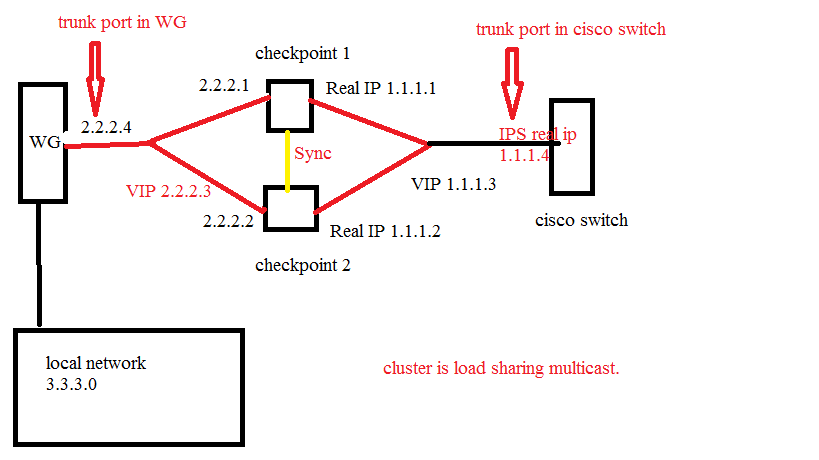
Thanks for answer. This is my topology. i need configure trunk in checkpoint. below is what i did.
1. Assign VLAN on both checkpoint eth1.
2. Put default gateway to ISP 1.1.1.4
3. did Get topology and configured network to external in eth1.
4. WG is watchguard firewall.
problem is: could not ping from Checkpoint to WG and ISP.
is my topology correct for this cluster?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A VLAN trunk only works if both ends are configured the same way.
If you plug the WatchGuard interface with a Trunk into a switch port, then that switch port must:
- Support VLANs
- Be configured as a trunk with the same VLANs as the WatchGuard
Same with both Check Point devices, both on the WatchGuard side of things and on the Cisco side of things.
Also, on the gateway topology, the interface that should be marked as external is eth1.10 (the VLAN interface) not eth1 (the physical one).
On a separate note, load sharing configurations (while supported) are generally not advised.
If the cluster members exceed 50% utilization and one node fails, the other member will become overloaded (which may cause a complete outage).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thanks for answer. I understood from your answer that trunk port is work. maybe i missed some configuration . can you say me some check list configuration for this topology ? can you give phone number ? i have a some question cluster in checkpoint R80.10 ? is it possible ?
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 13 | |
| 11 | |
| 11 | |
| 8 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 4 | |
| 3 |
Upcoming Events
Fri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


