- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
CheckMates Fest 2025!
Join the Biggest Event of the Year!
Simplifying Zero Trust Security
with Infinity Identity!
Operational Health Monitoring
Help us with the Short-Term Roadmap
CheckMates Go:
Recently on CheckMates
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Security Gateways
- :
- Re: How to block traffic coming from known malicio...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to block traffic coming from known malicious IP addresses R81.10
Hi everyone.
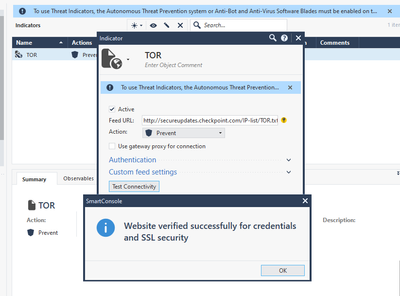
After spending some time trying to configure (via SmartConsole R81.10) the blocking of IP addresses known as malicious, based on sk103154, I finally managed to make it work.
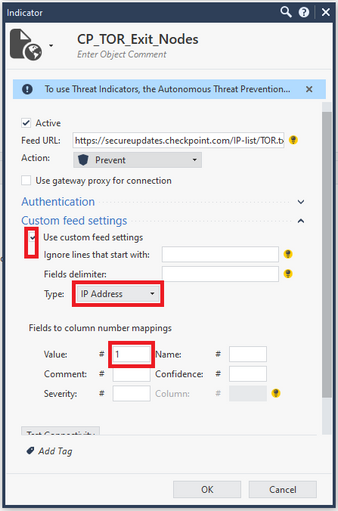
I was using the Check Point list (https://secureupdates.checkpoint.com/IP-list/TOR.txt) and whenever I looked at the logs I got the error "Feed format problem. Feed format not supported".
The problem is that we are not declaring a file in .csv format.
To solve this problem, just select "IP Address" in the type field, and enter "1" in the "Value" field of the custom feed settings.
Good luck to everyone.
27 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Well done sir, thank you for sharing this. Happy holidays!
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, we were recently exploring the feature/function to block IP using custom IOC as sk132193 described. Most of time the issue we ran into with the feed is format. Since different feed come in different format, each IOC feed need to have the format defined correctly. (In your example, type is IP address, and Value is located on 1st column). In some feed column 1 is name and column 2 is value (IP address).
Do you have any luck with Threat Intel feed that require API key access?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's exactly it.
I haven't tested it with API key yet.
I'm researching it and as soon as I get something I'll post it here.
If you can get something post it here too, please.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Rodrigo
Do you get output form this command?
- Printing existing feeds
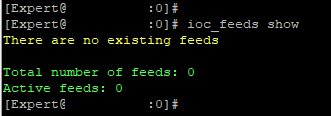
[Expert@HostName:0]# ioc_feeds show
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @DDiaz
I noticed that feeds added via SmartConsole only appear in SmartConcole, and the same is true for feeds added via cli.
I didn't find this limitation in the documentation.
On sk132193 you can find the list of cli commands.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Exactly that is my point, i would like to know how to check the feeds are working properly if I use smart console. I had a case with the TAC and told me is a must to run the CLI commands to make it work
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
First check if the updates are ok.
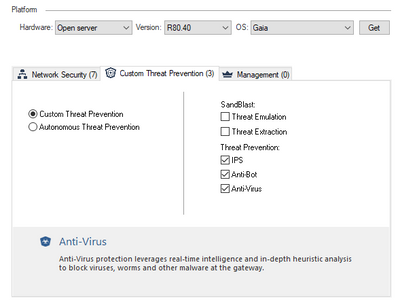
You can check this by filtering the logs through the Anti-Bot and Anti-Virus blades.
blade:(Anti-Bot OR Anti-Virus).
If everything is fine, you will see the Prevents in the logs on those same blades.
In my environment, I only see outgoing traffic being prevented.
My expectation was that all traffic originating from IPs known to be malicious would be blocked.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I can not find this logs in my environment, even if i curls the Urls meaning they are being downloading properly. I would appreciate if CP edit the SK with more details. Is not clear the steps on this. I had all this questions and TAC told us we must to run the cli commands. I can see in your environment works in another way
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I agree with you. SK could definitely be edited with more details.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For what it's worth, you will also need to be on at least R81 to drop incoming traffic.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Rodrigo
Which JHF version are you using?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R81.10
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@DDiaz , there is a troubleshooting section all the way at the bottom of sk132193. It includes many commands you can use to narrow down the issue.
First have to make sure the feed is pulling correctly, then have to make sure in read/ingest/interpret correctly by Check Point Gateway.
In my experience, the first issue was feed not pulling correctly since I put http instead of https; 2nd issue was the format which I corrected it like @Rodrigo_Silva screenshot show us.
Note that another issue I ran into is: if you are not pulling a remote feed and are importing a csv file locally from smart console, the csv file need to follow exact format as sk132193 describe under the section "CSV (*.csv) format", which contain 7 fields: UNIQ-NAME,VALUE,TYPE,CONFIDENCE,SEVERITY,PRODUCT,COMMENT
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I am running R81.10 in the SMS.
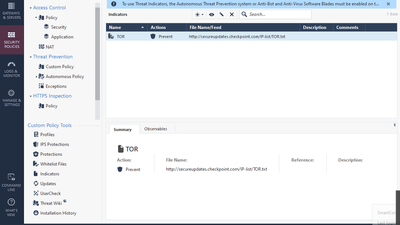
URLS used for feed (or https). http://secureupdates.checkpoint.com/IP-list/TOR.txt
Custom feed settings
Value 1 and type IP Address
Enabled Blades: Full Threat Prevention
curl_cli -v http://secureupdates.checkpoint.com/IP-list/TOR.txt for SMS, GW Successfully
I am able to download properly the txt from the PC running Smart Console
I am not able to see the state of the Fetches by filtering the logs through the Anti-Bot and Anti-Virus blades.
blade:(Anti-Bot OR Anti-Virus).
Do i missing something?
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For my experience, the feed I added through smart console are added to all gateway managed by the smart management server (which is what I want).
Since your feed is Tor Exit node, it make sense to observe it in outgoing traffic not incoming traffic.
If you want to see something for incoming traffic, try the Talos feed or AlienVault feed, you will see some external IP probing the firewall and prevented by the IPS/IOC feed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you very much @Cyber_Serge . Will try that ASAP. Will post my results
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
TOR exit node IPs are relevant for both ingress and egress blocking, See https://www.cisa.gov/uscert/ncas/alerts/aa20-183a for an analysis.
An operationally viable approach for ingesting IOC feeds into Check Point enforcement points is provided by Infinity NDR. The feeds are managed centrally, and the individual IOCs can be seen and managed in the NDR application. They can then be selectively delivered via NDR "data sets", which are compatible with sk132193.
Note: inbound blocking (as well as IPv6 indicators) are supported starting from R81.
User guide: https://community.checkpoint.com/t5/CloudGuard-NDR/Infinity-NDR-Intel-User-Guide/m-p/131434
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Guys
What is the output of this command in your environment?
cat $FWDIR/conf/ioc_feeder.conf
{
"external_ioc": "on",
"interval": "300",
"ioc_bundle": "/database/ca_bundle.pem",
"feeds": {
}
}
[Expert@FW-MGMT-UY:0]#
The interval does not change even if you modify it from:
To change the fetching interval, go to Manage & Settings > Blades > Threat Prevention > Advanced Settings, go to External Feed, and select the applicable interval.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Disclaimer that I'm still on R81 but here I can see the difference between something configured locally and something from the GUI...
Cheers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Which command was used [Expert@HostName:0]# ioc_feeds show ?
I just have output using CLI IOC feeds. If smart console method is used nothing show
There is a lot off different things regarding this issue. SK must be updated, is very confusing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
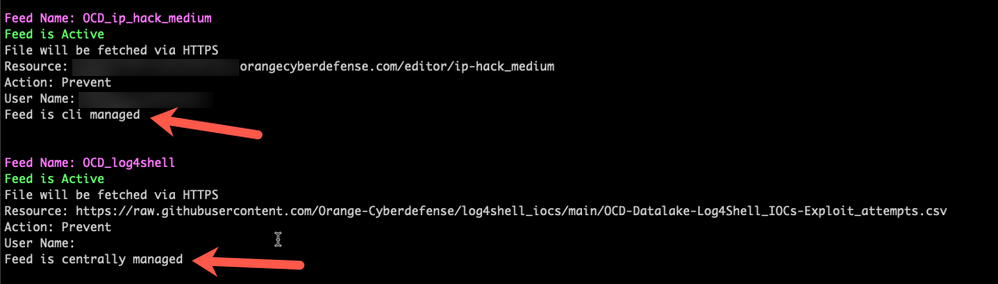
Yes, thats from ioc_feeds show...
I have 7 feeds configured so there was too much to blur out to get it all in one screenshot 😀
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you use the Smart Console Method?
Which version of SMS and FW do you have.
I am not able to make it work via Smart console, just CLI way
Followed all the recommendations possible and no luck
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, the once that are marked "centrally managed" are done through the GUI.
R81 JHF44.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Team
I will make a brief summary about this issue and the results of the case with the TAC.
Smart Console External IOC Feeds works properly if the GWs are in R81 and above. After long sessions with the TAC, labs, Escalation Team, that was the conclusion. Maybe somebody had luck with different versions, but we could not. We had 4 different environments with SMS in R81.10 and GWS R80.40
It is clear in documentation the SMS must be in R81 and higher (Smart Console Feature), but not the GWs
From SK this part is confuse
Installation
The feature is integrated in version R80.30 and above.
Note: To import external Custom Intelligence Feeds using SmartConsole in versions R81 and higher, refer to: Threat Prevention R81 Administration Guide > Configuring Advanced Threat Prevention Settings > Configuring Threat Indicators > Importing External Custom Intelligence Feeds > Importing External Custom Intelligence Feeds in SmartConsole.
In some way they must to include the Smart console feature ¨ works properly¨ in GWs with R81 and higher. Was suggested to the TAC to edit the sk132193 and add some captures, Logs queries for verifications as is posted in CHECKMATES threads.
We tested the CLI way and works perfect in the versions they mentioned, but not the Smart console External IOC feeds.
We also realized in all the environment we tested this file could not be found when you troubleshoot
$FWDIR/log/ext_ioc_push.elg
I think with all the tests we made, there is a lot of information from the case we had to edit the SK and help the community.
Cheers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Follows your steps, but I get the error "Checkpoint_TorExitNodes: Feed format problem. Feed format not supported" when i check AV blade logs. Can you please help.
Regards,
MD
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi guys
i'm on R81.10 MDS with Take 45 and some test gateway with 80.40 Take 139 and Take 156.
i've followed the SK and this thread..but it doesn't work as expected.
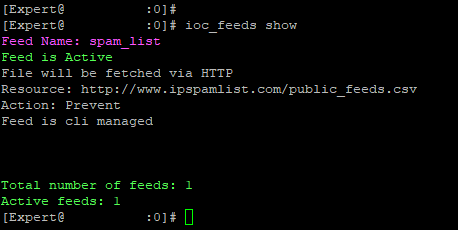
feed are imported and fetched correctly ( using cli ) (i've tried two differents feeds )
ioc_feeds show
Feed Name: CPtorIP
Feed is Active
File will be fetched via HTTPS
Resource: https://secureupdates.checkpoint.com/IP-list/TOR.txt
Action: Prevent
Feed type: custom_csv
Feed Name: reputation
Feed is Active
File will be fetched via HTTP
Resource: http://reputation.alienvault.com/reputation.data
Action: Prevent
Feed type: custom_csv
Total number of feeds: 2
Active feeds: 2
( and from smartconsole log,blade Antivirus I don't see any error )
but if I try to generate some traffic from the firewall TO some of that ip addresses...it simply pass...without being prevented.
is it normal?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
If you have bersion R81, you could try the sollution suggested here:
"select "IP Address" in the type field, and enter "1" in the "Value" field of the custom feed settings."
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 26 | |
| 11 | |
| 10 | |
| 8 | |
| 8 | |
| 7 | |
| 5 | |
| 4 | |
| 3 | |
| 3 |
Upcoming Events
Tue 28 Jan 2025 @ 10:00 AM (CET)
EMEA - Securing the Future: A Technical Introduction to Practical IoT HackingTue 28 Jan 2025 @ 05:00 PM (CET)
Americas - Securing the Future: A Technical Introduction to Practical IoT HackingThu 30 Jan 2025 @ 03:00 PM (CET)
EMEA - Enhance Your Azure Environment with Check Point Industry-Leading Threat PreventionThu 30 Jan 2025 @ 02:00 PM (EST)
AMERICAS - Enhance Your Azure Environment with Check Point Industry-Leading Threat PreventionThu 13 Feb 2025 @ 03:00 AM (CET)
Navigating the Cyber Frontier: A Check Point Executive Briefing - APACThu 13 Feb 2025 @ 03:00 PM (CET)
Navigating the Cyber Frontier: A Check Point Executive Briefing - EMEATue 28 Jan 2025 @ 05:00 PM (CET)
Americas - Securing the Future: A Technical Introduction to Practical IoT HackingThu 30 Jan 2025 @ 03:00 PM (CET)
EMEA - Enhance Your Azure Environment with Check Point Industry-Leading Threat PreventionThu 30 Jan 2025 @ 02:00 PM (EST)
AMERICAS - Enhance Your Azure Environment with Check Point Industry-Leading Threat PreventionThu 13 Feb 2025 @ 03:00 AM (CET)
Navigating the Cyber Frontier: A Check Point Executive Briefing - APACThu 13 Feb 2025 @ 03:00 PM (CET)
Navigating the Cyber Frontier: A Check Point Executive Briefing - EMEAThu 13 Feb 2025 @ 02:00 PM (EST)
Navigating the Cyber Frontier: A Check Point Executive Briefing - AmericasAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter