- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
Quantum SD-WAN Monitoring
Watch NowCheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Geolocation in access rules
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Geolocation in access rules
Hi,
We're on R81.10 and planning on migrating our old Geolocation policy, under the IPS, to the new version under the access rules.
I have a question regarding how to implement exceptions.
1. The block rule is with destination "any" and in the beginning of the policy. In order to bypass the block rule I need to put the allow rule above it, but since the destination is "any", it will actually bypass the entire policy for these IPs.
How do I make the policy bypass these IPs only in the context of the geopolicy rule?
2. First of all, I guess there's no way around of creating objects for every IP we want to bypass?
Thanks
- Tags:
- geolocation
- r81.10
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For this to work the way you want, I believe you will need a separate, ordered layer for your GeoProtection rules.
When ordered layers are used, an allowed packet must match an Accept rule in each layer.
This means you could create a bypass rule for specific IPs in your GeoProtection layer.
Traffic would still have to match an Aceept rule in your other, ordered layer.
Whether the GeoProtection layer is first or second, it shouldn’t matter, but having it second might be better because of how things are logged.
See also: https://community.checkpoint.com/t5/Management/Rule-set-with-track-none-but-still-logging-2/m-p/1277...
11 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
See sk126172: Configuring Geo Policy using Updatable Objects in R80.20 and higher
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi G_W_Albrecht,
The SK doesn't mention bypassing issues at all.
The other article talk about inline layers which I'm not familiar with, but if I understand correctly that's exactly what I need.
Just create my geolocation rules inside an inline layer at the beginning of the policy, with the block rule as "cleanup rule".
IP address which we bypass will only bypass the geopolicy rule, but will still be processed by the rest of the rulebase?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please explain the bypass - usually we have accept or drop. Geo Policy is a pre-selection of possible connections, so why bypass ?
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK, so say we want to block all traffic coming from a set of countries, EXCEPT from specific IPs of our clients abroad which are situated in these countries.
So I want to bypass only the geolocation block rule for these IPs.
But I still need these IPs to be processed by the rest of the rulebase.
Hope it's clearer
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, if you know the IPs you can let it pass in the rulebase.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
But here lies my problem/question -
I must put all the geolocation related rules in an inline layer in order for the IPs bypass to only relate to the geolocation?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I do not see that you must do that - just define appropriate rules to handle the IPs you know should be accepted.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Surely I'm missing out on something here...
I have a huge rulebase with many rules for traffic coming from the internet to resources in our network.
Up until now, the GEO policy was handled seperately, meaning that traffic would first be checked by the GEO policy and then by the rulebase.
Now, if I put the GEO rules at the top of my access policy in the format of let's say:
Source: USA
Destination: ANY
Action: Block
and I'll bypass some specific IPs from USA, they would just bypass the ENTIRE rulebase and won't be assessed anymore. isn't that so?
I mean, I DO want them not to be blocked by the GEO rules, but I still want them to be assesed and blocked/allow by the rest of the rulebase
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For this to work the way you want, I believe you will need a separate, ordered layer for your GeoProtection rules.
When ordered layers are used, an allowed packet must match an Accept rule in each layer.
This means you could create a bypass rule for specific IPs in your GeoProtection layer.
Traffic would still have to match an Aceept rule in your other, ordered layer.
Whether the GeoProtection layer is first or second, it shouldn’t matter, but having it second might be better because of how things are logged.
See also: https://community.checkpoint.com/t5/Management/Rule-set-with-track-none-but-still-logging-2/m-p/1277...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi PhoneBoy,
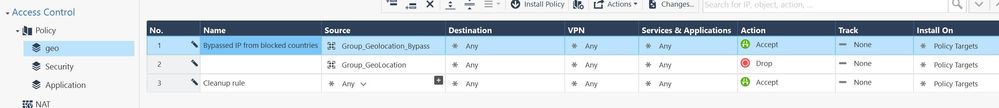
So just to see I understand your suggestion, I would create something like this?:
This would block all countries in rule 2, but still allow certain IPs from these countries, based on rule 1. and after all that will go on to continue assessing the main rule base in the "Security" layer?
Regarding the order, you said it's better to put the "Geo" layer second. But doesn't that mean the traffic would first be assessed by the "Security" layer and traffic won't be blocked geographically?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, you've got it.
Based on the the layers shown, traffic must hit an Accept rule in the geo, Security, and Application layers.
If a drop rule is matched in any of the layers, traffic will be blocked.
To understand how rulebase matching works, see: https://community.checkpoint.com/t5/Management/Unified-Policy-Column-based-Rule-Matching/m-p/9888#M1...
You could put the geo layer last and it would still work the same.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 37 | |
| 24 | |
| 11 | |
| 10 | |
| 8 | |
| 7 | |
| 6 | |
| 5 | |
| 5 | |
| 4 |
Upcoming Events
Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 19 Feb 2026 @ 03:00 PM (EST)
Americas Deep Dive: Check Point Management API Best PracticesTue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 19 Feb 2026 @ 03:00 PM (EST)
Americas Deep Dive: Check Point Management API Best PracticesTue 24 Feb 2026 @ 11:00 AM (EST)
Under The Hood: CloudGuard Network Security for Azure Virtual WANAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter