- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Gateways Loose Internet Connection After Policies ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Gateways Loose Internet Connection After Policies Intallation
Hello Mates!
I'm having a strange problem in a client's environment. It's a Cluster in HA R81.10 Take 94.
When I install policies, the gateways lose communication with the internet, there's no ping to the outside, but the machines behind the gateway navigate normally.
When I apply an fwunloadlocal to the gateways, they start responding to ping from the internet again, but the machines stop browsing.
No drops are shown in zdebug, the policies rules seems to be ok too.
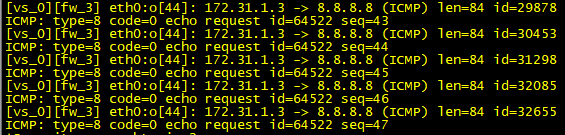
fw monitor show like this when I try to ping external address:
the IP 172.31.1.3 is the gateway interface. I just see the request, not reply
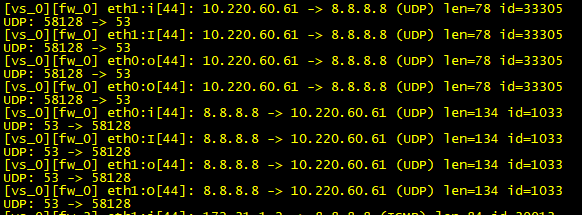
In the same moment that a machine behind the gateway shown me request/reply normally:
What could be causing this?
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello friends @the_rock @Blason_R
Thank you very much for all your help and dedication so far!
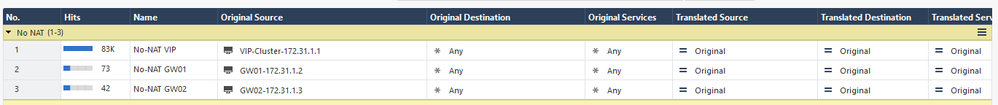
The problem has been solved with a NO NAT rule on the Check Point.
As I mentioned before, this Check Point appliance didn't perform NAT, the NATs were configured on the F5, and it has worked like this since deployment.
I believe something was changed on the F5, and out of curiosity, I created rules for the members' IPs and the cluster's VIP, and after creating the rules, the appliances navigated normally.
However, I didn't understand why it worked without the policies. Was there something implicit that made it work?
Do you have any idea of what could have made the appliances' navigation work without the policies installed?
Thank you all!
14 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I had this happen with customers before and 9 times out of 10, either its something with topology (anti spoofing) and/or routing/nat.
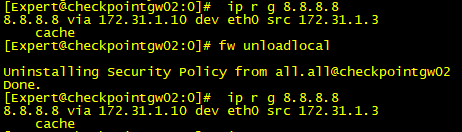
Here is an easy thing to try...in both situations, run ip r g 8.8.8.8 from gateway and compare the output, that should give a clue.
HTH @Bernardes
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hello @the_rock !
This was the result before and after fw unloadlocal:
I try to disable anti-spoofing, but it doesn't work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Any changes in Implied rules? Did you disable anything?
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @Blason_R ! The implied rules are default, no changes.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok so what does fw stat shows if policy push is successful?
Do you get ping to 8.8.8.8 or 9.9.9.9
Do you get arp of your default gateway (arp -an | grep <DG_IP_Address>)
What is cphaprob -a if says?
cphaprob stat shows any PNOTES?
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
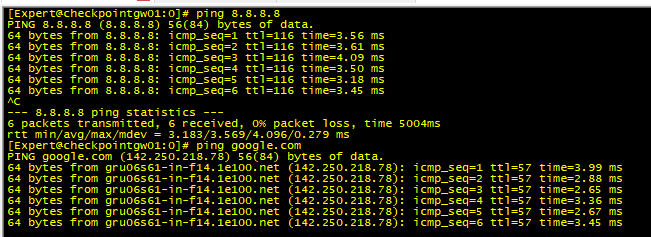
@Blason_Rlook at the output results for these commands:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
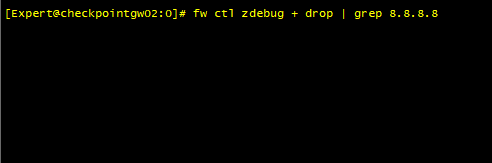
Ok, so thats the same...can you tell if nat takes place when issue occurs? What does zdebug show?
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@the_rockthe NAT occurs on an F5 appliance in front of Check Point. This Security Gateway is not doing NAT in this case.
In zdebug output not is showing nothing fot this traffic, apparently theres no drop
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Bernardes Since I like to think about anything in life the logical way, lets recap this situation.
Sooo...IF you do fw unloadlocal and everything works fine, that tells me logically that SOMETHING in the policy is causing the problem. Can you do zdebug BEFORE you unload the policy and see if it gives anything?
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@the_rockThis zdebug output above is when the policies were applied, but after the fw unloadlocal the result is the same, aparently there's no drops before or after the policies are applied.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok...if you are 100% sure and you have verified routing/natting, then only other thing I could think of is anti-spoofing. Please ensure thats accurate, because if wrong, it can definitely cause issues like this one.
Take care.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello friends @the_rock @Blason_R
Thank you very much for all your help and dedication so far!
The problem has been solved with a NO NAT rule on the Check Point.
As I mentioned before, this Check Point appliance didn't perform NAT, the NATs were configured on the F5, and it has worked like this since deployment.
I believe something was changed on the F5, and out of curiosity, I created rules for the members' IPs and the cluster's VIP, and after creating the rules, the appliances navigated normally.
However, I didn't understand why it worked without the policies. Was there something implicit that made it work?
Do you have any idea of what could have made the appliances' navigation work without the policies installed?
Thank you all!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That nice to know that but still looks odd to be honest. The traffic originating from gateway does get hide or folded behind VIP and shouldn't matter if those are natted or not provided what is the sequence kept in global properties for "Traffic originating from Gateway" <LAST|First| Before LASt>
And without policy the appliance does not route the connection or no connection can traverse through the appliance for security reason else it will perform just like normal server.
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I tend to agree with @Blason_R . Good job by the way in doing those rules, since F5 is handling the NAT. But, having said that, by default, CP firewall will not do any nat, as out of the box, nat is not enabled and plus, there is no default nat rule inside the policy that would nat all outgoing traffic, so one either need to be created OR you can check option to nat all internal networks behind the firewall external IP.
Andy
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 20 | |
| 19 | |
| 18 | |
| 8 | |
| 7 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter