- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Firewall Antispoofing
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Firewall Antispoofing
Hello!!
I find a problem deploying a new gateway in R81.20 (open server), and i hope someone could help me.
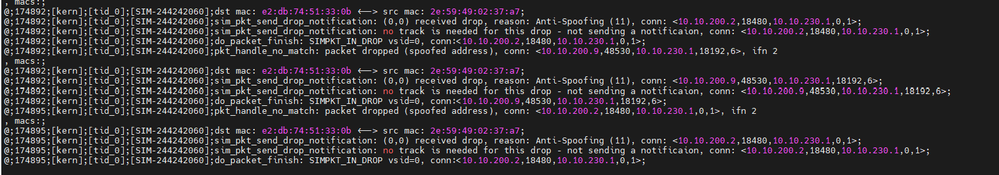
The management and the firewall are in different subnets. I have permormed a fw unloadlocal in the gateway before the SIC initialization process, but I have notice every traffic from remote networks are dropped by antispoofing even when the routes are well configured and I have dissabled the policy in the firewall.
Anybody knows if there is any way to disable this antispoofing protection?
Best regards!
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, i double checked it on my R81.20 GW now,
try the following commands by this order:
fwaccel off
fw ctl set int fw_antispoofing_enabled 0
fwaccel on
verify it set to 0 by:
fw ctl get int fw_antispoofing_enabled
try to initiate SIC now
P.s fw unloadlocal don't unload the antispoofing configuration
13 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, but dont do that, UNLESS its Check Point in Azure, then it has to be disabled. This is where you modify it, make sure its set per route setting, as that automatically updates it, OR as long as group defined is correct.
Best,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
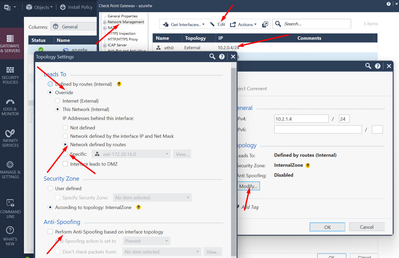
To disable Anti-Spoofing either completely or partly just edit the relevant interface in SmartConsole:
- In SmartConsole, from the left navigation panel, click Gateways & Servers.
- Open the Security Gateway / Cluster object.
- From the left, click Network Management.
- Right-click on the interface and click Edit.
- From the left, click the General page.
- In the Topology section, click Modify.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good reference
Interface - Topology Settings (checkpoint.com)
Understanding Topology
An interface can be defined as being External (leading to the Internet) or Internal (leading to the LAN).
The type of network that the interface Leads To:
-
Internet (External) or This Network (Internal) - This is the default setting. It is automatically calculated from the topology of the gateway. To update the topology of an internal network after changes to static routes, click Network Management > Get Interfaces in the General Properties window of the gateway.
-
Override - Override the default setting.
If you Override the default setting:
-
Internet (External) - All external/Internet addresses
-
This Network (Internal) -
-
Not Defined - All IP addresses behind this interface are considered a part of the internal network that connects to this interface
-
Network defined by the interface IP and Net Mask - Only the network that directly connects to this internal interface
-
Network defined by routes - The gateway dynamically calculates the topology behind this interface. If the network changes, there is no need to click "Get Interfaces" and install a policy.
-
Specific - A specific network object (a network, a host, an address range, or a network group) behind this internal interface
-
Interface leads to DMZ - The DMZ that directly connects to this internal interface
-
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If your issue is that you can't initiate SIC or install the policy because of Anti spoofing drop and you can't change your antispoofing configuration and push policy because of that, and you want to disable it on the fly from cli temporaty
Try:
fw ctl set int fw_antispoofing_enabled 0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
EXCELLENT idea!
Best,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is exactly my issue! But I tried to do that follow the sk117618, But it didnt works!
The version metioned in these SK is from R77.20 to R80.40. Maybe this is the issue. I dont know in the newest version there is another way to perform this action.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
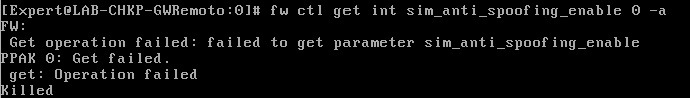
So you ran: fw ctl set int sim_anti_spoofing_enabled 0 -a
And turn off and on fwaccel As well?
If you reset SIC in the Gw side after the cprestart do you still have drops?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I try to execute this command, but it dont work
I havent reset the sic because i didnt perform the SIC in the first place. I dont know if the antispoofing is something configured in smartconsole why is affected the traffic if the firewall hasnt policy installed...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes its configured in gw object in smart dashboard. Are you saying it's fresh installed gw that never had sic or policy installed before, and still drop traffic on anti spoofing?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
mm not really. I need to change the interface configuration of this firewall. So I perform the following steps
1. Clear the trust between Management and firewall (Because the new trust will be initialized in other interface)
2. cpconfig and restablish SIC password in the gateway.
3. Change the network interface and routing configuration. (An new router is added between Management and firewall)
4. I perform a fw unloadlocal (In this point I think i dont have to be worried about antispoofing) But for any not understandeble reason, it still affected traffic.
5. Try to ininitalize again the SIC.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, i double checked it on my R81.20 GW now,
try the following commands by this order:
fwaccel off
fw ctl set int fw_antispoofing_enabled 0
fwaccel on
verify it set to 0 by:
fw ctl get int fw_antispoofing_enabled
try to initiate SIC now
P.s fw unloadlocal don't unload the antispoofing configuration
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks!! Maybe I didnt perform the commands in the correct order! 😄
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Technically, turning off securexl would not have anything to do with anti-spoofing. I would double check you have it set correctly if its in production.
Best,
Andy
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 15 | |
| 13 | |
| 10 | |
| 8 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 2 | |
| 2 |
Upcoming Events
Thu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter