Enable SandBlast ICAP server
Login to export mode and start the ICAP server on the TEX appliance or security gateway.
[Expert@cp-fw-01:0]# icap_server start
cpwd_admin: Process CICAP started successfully (pid=31792)
[Expert@cp-fw-01:0]#
Check if the ICAP processes are running.
[Expert@cp-fw-01:0]# ps -def |grep icap admin
31792 4631 0 19:19 ? 00:00:00 c-icap -N -f /opt/CPsuite-R77/fw1/c-icap/etc/c-icap.conf admin
31813 31792 0 19:19 ? 00:00:00 c-icap -N -f /opt/CPsuite-R77/fw1/c-icap/etc/c-icap.conf admin
31820 31792 0 19:19 ? 00:00:00 c-icap -N -f /opt/CPsuite-R77/fw1/c-icap/etc/c-icap.conf admin
31826 31792 0 19:19 ? 00:00:00 c-icap -N -f /opt/CPsuite-R77/fw1/c-icap/etc/c-icap.conf admin
31931 31651 0 19:20 pts/1 00:00:00 grep icap
[Expert@cp-fw-01:0]#
Enable ICAP logging.
[Expert@cp-fw-01:0]# tecli advanced remote emulator logs enable
remote emulator logs set to enabled successfully
[Expert@cp-fw-01:0]#
Also make sure that your firewall rules allow access to the ICAP server port 1344/TCP on the TEX appliance or security gateway.
Please note that Jumbo Hotfix Accumulator Take_286 or higher for R77.30 should be used.
More information can be found in sk111306: Check Point support for Internet Content Adaptation Protocol (ICAP) server
Prepare the F5 BIG-IP
Download the f5.checkpoint_sandblast_icap iApp template from the link below. This is an iApp template that creates ICAP related elements (nodes, pool, internal virtual server, profiles). The newly created request and response adapt profiles can be used by standard virtual servers so they can interact with a Check Point SandBlast ICAP Server.
GitHub - nvansluis/f5.checkpoint_sandblast_icap: iApp template to integrate F5 BIG-IP with Check Poi...
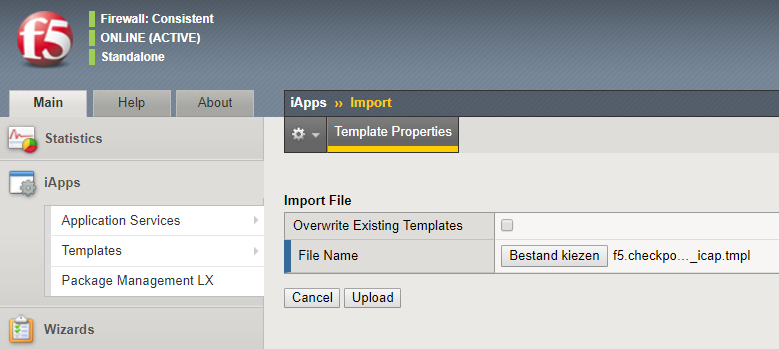
- Login to the Configuration Utility and Import the iApp template: iApps > Templates > Import.
- Deploy a new application by using the iApp: iApps > Application Services > Applications > Create.
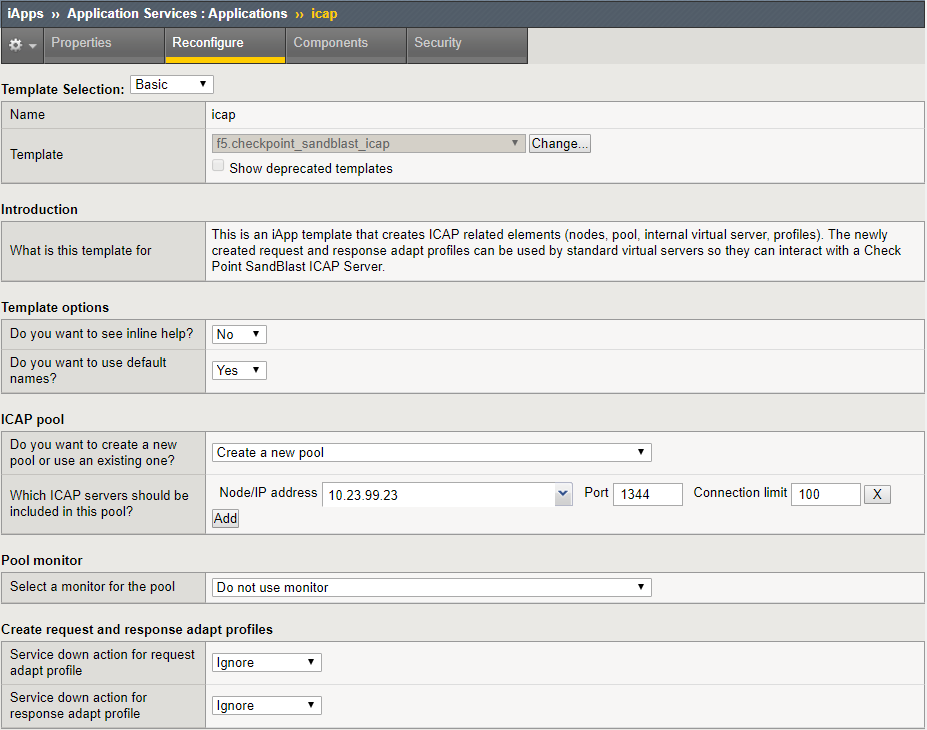
- Click Finished to deploy the iApp. You will see the components that have been configured.

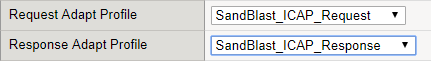
- You can now use the newly created Request and Response Adapt profiles and attach them to a Virtual Server that has been configured with a HTTP profile.
Testing Check Point SandBlast
Below you'll see some screenshots of what happens when a user attempts to upload or download malicous files.
Malicious uploads
- Upload a file that triggers Threat Emulation (Zero-Day Protection).
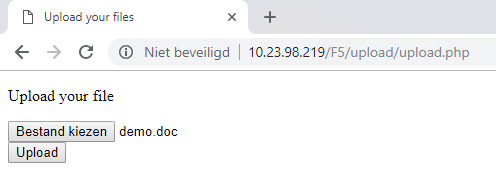
- The upload of this malicious file is prevented by Check Point SandBlast.

- Here you can see the log message that is created by Check Point.
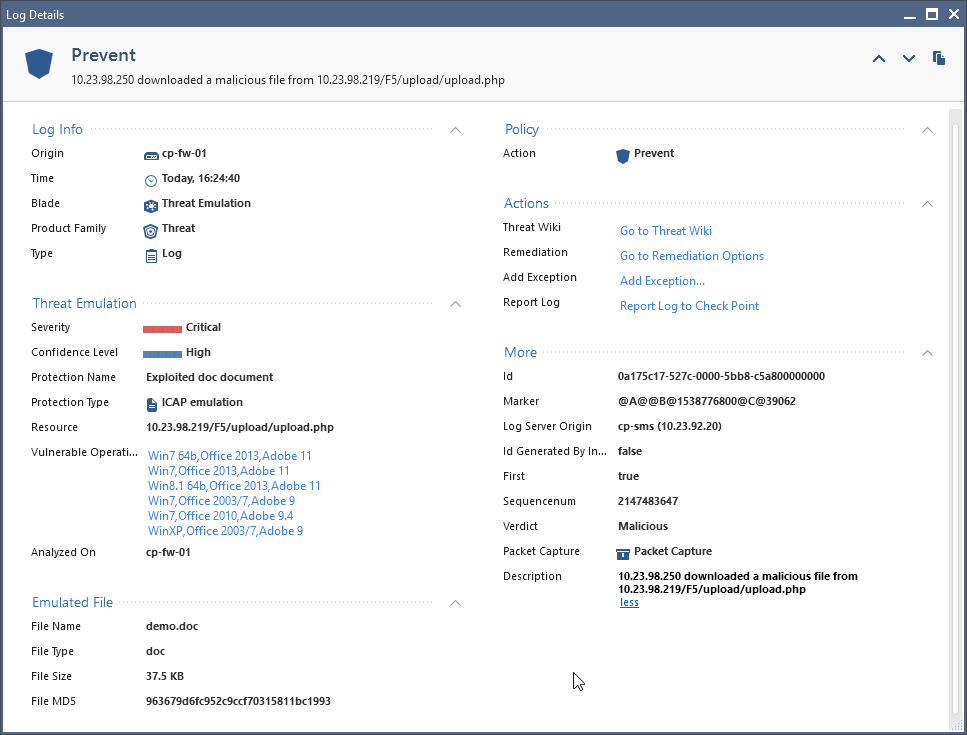
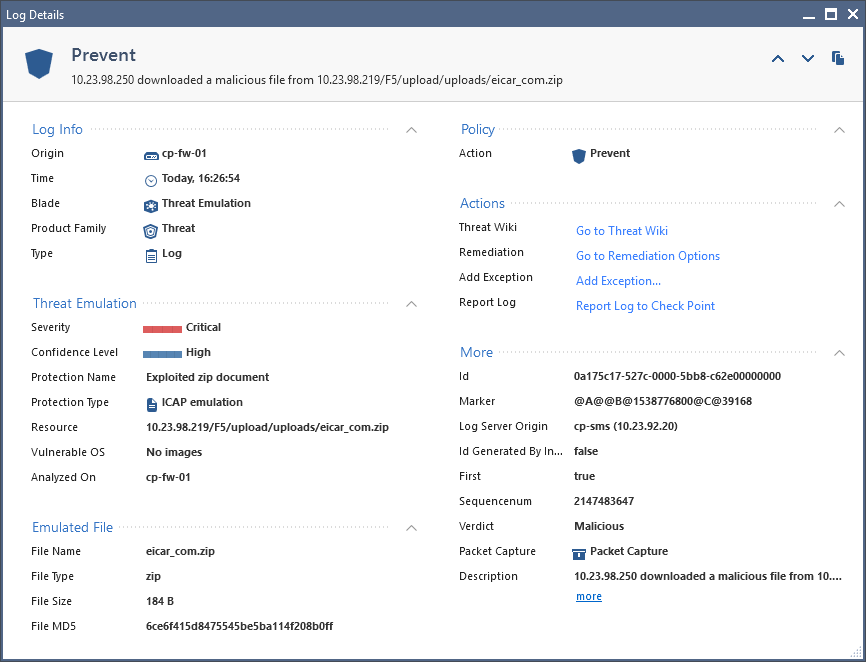
Malicious downloads
- A user tries to download a malicious file.
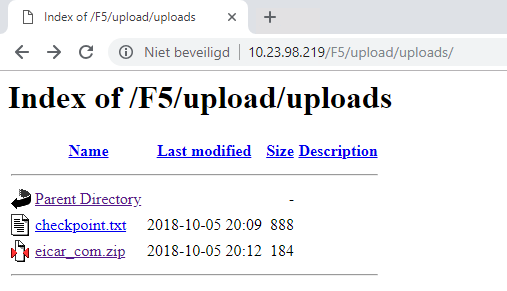
- The download of a malicious file is prevented by Check Point SandBlast.
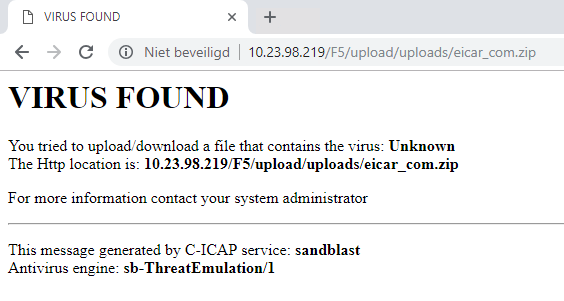
- Below of an example what log message is created by Check Point.