We see this on an R81.10 gateway:
| Error: 'URL Filtering' is not responding. Verify that 'URL Filtering' is installed on the gateway. If 'URL Filtering' should not be installed verify that it is not selected in the Products List of the gateway (SmartDashboard > Gateway > General Properties > Check Point Products List). This error may occur if the Security Cluster is in Multi-Version Cluster mode. After upgrading all the cluster members to the same version, this error should disappear. |
| Error: 'Identity Awareness' is not responding. Verify that 'Identity Awareness' is installed on the gateway. If 'Identity Awareness' should not be installed verify that it is not selected in the Products List of the gateway (SmartDashboard > Gateway > General Properties > Check Point Products List). This error may occur if the Security Cluster is in Multi-Version Cluster mode. After upgrading all the cluster members to the same version, this error should disappear. |
| Error: 'Application Control' is not responding. Verify that 'Application Control' is installed on the gateway. If 'Application Control' should not be installed verify that it is not selected in the Products List of the gateway (SmartDashboard > Gateway > General Properties > Check Point Products List). This error may occur if the Security Cluster is in Multi-Version Cluster mode. After upgrading all the cluster members to the same version, this error should disappear. |
Output from 'fw stat' and 'enabled_blades':
[Expert@gateway:0]# fw stat
HOST POLICY DATE
localhost Perimeter 7Feb2024 16:06:12 : [>eth0] [<eth0] [>eth1] [<eth1] [>vpnt200] [<vpnt200] [>vpnt201] [<vpnt201] [>vpnt100] [<vpnt100] [>vpnt101] [<vpnt101]
[Expert@gateway:0]# enabled_blades
fw vpn urlf av appi ips identityServer SSL_INSPECT anti_bot content_awareness mon
We see logs for all three blades on this gateway:
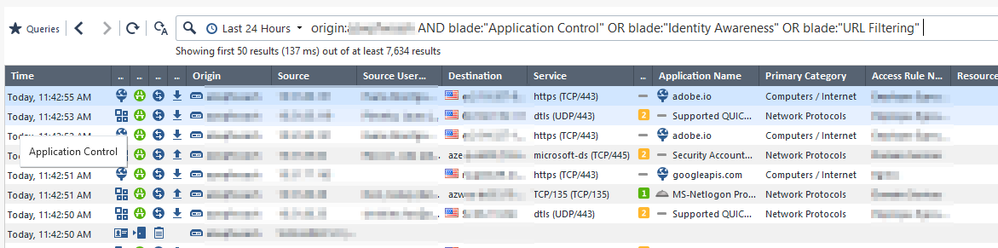
So I'm thinking this is cosmetic but the OCD in me doesn't like seeing the splats on the overview page. Also, this survives a reboot.
Anyone have any helpful suggestions?



