- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Connection with gateway cluster is lost from the p...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
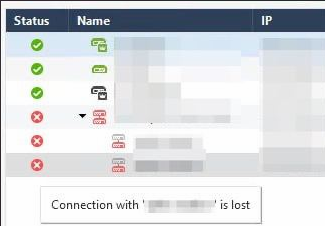
Connection with gateway cluster is lost from the primary Management Server
Hi everyone!
The current infrastructure has a following build-up (R80.40): two management servers in the HA pair, two clustered gateways (6000 appliances; active & standby), and a standalone gateway. Previously, the HQ SMS suffered a failover to the DR SMS. We had to create a fresh instance of the HQ SMS, enable the HA pair again (sync was made from the DR to the new HQ), and switch back the places of the primary and secondary SMS (HQ -> to primary; DR -> to secondary).
As of now, HQ SMS tries to communicate with the cluster through the direct IP of the cluster member and has the following issue:
DR SMS (secondary) does not have any connectivity issues and speaks to the cluster member through a management IP (e.g, 192.168.2.1) configured under the Network Management tab:
SIC is working properly (Trust Established for the HQ SMS). The logs keep coming from the cluster to the HQ SMS on port 257. Whenever the SIC status is tested, policy is being pushed or interfaces are being fetched, the SmartConsole goes idle and throws errors, specifying that there is no connection between the SMS and the cluster (e.g., on port 18191).
Taking into consideration that the Network Management is identical between the HQ and DR, is there a way to specify from the HQ SMS side the management IP (same as on DR side) as the proper IP address to establish the communication with the cluster?
9 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The correct IP to use should be pushed as part of a successful policy install.
If for some reason this isn't working correctly, you may need to unload the policy on the gateway (using fw unloadlocal), then push policy.
As this will unload the security policy and likely drop traffic, this will need to be done during a maintenance window.
Otherwise, I recommend engaging the TAC: https://help.checkpoint.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for the feedback! We previously pushed a policy from the newly created HQ SMS to the cluster, but that didn't help. Maybe, as you mentioned, the overall policy unload from the cluster might be the case.
JFYI, the cluster members have the IPs set to 10.0.0.1 and 10.0.0.2. Both of them contain a set of identical interfaces configured under the Network Management tab. One of those interfaces is the management interface with the IPs set to 192.168.1.1 (for node-1) and 192.168.1.2 (for node-2). The HQ is now trying to communicate directly to the 10.0.0.1 and 10.0.0.2, while the DR SMS is using the 192.168.1.1 and 192.168.1.2 for connection. Now, in order to perform any policy push activity, we have to open a direct route to the 10.0.0.1 and 10.0.0.2, which was previously never done since both of the SMS were communicating through that management interface. Now it's only DR that follows the desired approach, while HQ is trying to connect through the direct IP address of the cluster.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Curious why having the routes there is an issue, especially if it resolves the issue?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I assume because the owner of the infrastructure was using that dedicated management IP on the cluster before the HQ failover. Now, they do not want to alter the networking part and open a direct route to the cluster members for the HQ SMS only, since the DR SMS is still communicating through the cluster management IP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It could also be an intermediary firewall or similar that's blocking access.
Have you done a tcpdump to see if the traffic is sent/received correctly on port 18191 on the source and target?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I agree with @PhoneBoy .Please run tcpdump and fw monitor and follow the packet flow. If you need help with filters, let us know and I can send you some good examples.
You can also refer to this website that my colleague made ages ago to help with captures on various vendor firewalls -> https://www.tcpdump101.com
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In my experience, 9 times out of 10, this could be wrong route problem. Maybe do basic route check on both cluster members, say ip r g 8.8.8.8 or ip r g mgmt_Ip_address and make sure its correct.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for the advice, but we checked the low-level routing configurations on both DR and HQ SMS (they are identical and were previously synced from the DR to HQ) and didn't find any drawbacks. The ip route contains all the necessary details, plus since the logs are being pushed from the cluster to the HQ SMS, I think there is at least some connectivity between the appliances established.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do you fixed this yet? I've got the same error and still find solution. Thanks
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 18 | |
| 12 | |
| 8 | |
| 5 | |
| 4 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter