- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
The Great Exposure Reset
24 February 2026 @ 5pm CET / 11am EST
CheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Checkpoint Advanced OSPF Capability
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Checkpoint Advanced OSPF Capability
Hello, we would like to move some features we are running today from a Cisco router to the Checkpoint firewall. I have several questions about this. Currently we are redistributing our Checkpoint default route into our OSPF domain which works fine. However, we are preparing to implement a second Internet ISP connection and want to redistribute the Checkpoint default route based on conditions. In the Cisco world, we do this using IP SLA^s. We setup an IP SLA to monitor upstream IP^s addresses, for example 8.8.8.8. If the IP SLA cannot ping 8.8.8.8 the default route will not be redistributed.
Does Checkpoint have the ability to redistribute its default route based on this condition?
Also, can I create permanent static routes in Checkpoint? I would want to redistribute a permanent static route into our OSPF domain so our IP SLA cannot reach 8.8.8.8 via the second Internet ISP.
23 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As far as I know, there isn't a way to redistribute a route based on reachability of a specific IP.
You can, of course, create static routes in Gaia, and you can use route filters to determine which routes do not go to a specific domain.
Refer to: How to configure route redistribution and inbound route filters in Gaia Portal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
While IP SLA is not available, you can still monitor the state of the upstream device using ping and disable default route redistribution if it fails.
Below is the example of similar settings for BGP on Gaia, but I recall doing the same for OSPF:
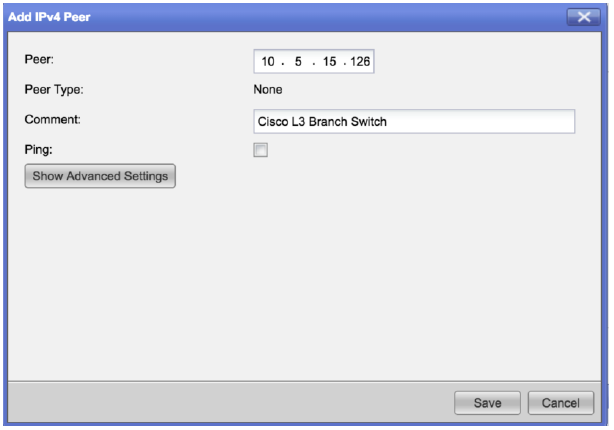
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R&D reminded me of this yesterday. ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It would actually be nice if CP can implement the option similar to IP SLA.
The ping gets us to recognize the next hop's availability, but if the problem is upstream of it, it is difficult to manipulate route distribution based on route integrity.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Additional capabilities in this area are planned.
If you have an immediate need, I recommend engaging with your Check Point SE.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, a function similar to Cisco IP SLA's where we could monitor further upstream would be nice. Thx Dameon.
Also, either of you know the answer to this?
R1--->CPfw--->R2
I have a single default route on R1, using an IP SLA. If the track is down, R1 will remove the default route. I want to redistribute R1's default route into my OSPF domain. Will the checkpoint firewall OSPF process pass R1's default route into R2's OSPF process?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am a bit rusty, but this is what I recall:
If you have a static default route on CPfw, it will take precedence over the one received from upstream router via OSPF.
Not having static 0.0.0.0 on CPfw is a bad idea.
If you have a static 0.0.0.0/0 on CPfw, you can forego "redistribute connected" and allow OSPF propagation into the zone, but then you'll have to define static routes to the networks behind CPfw on the downstream router.
Otherwise, once 0.0.0.0/0 stops propagating due to the loss of connectivity by the upstream router, the traffic will not be aware of the destination.
Check if there is a possibility to select particular connected routes for redistribution. I recall that option being available in IPSO, but am not sure about Gaia.
Do take these statements with the grain of salt: It's been a while since I've done BGP and OSPF work with Check Point.
Regards,
Vladimir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
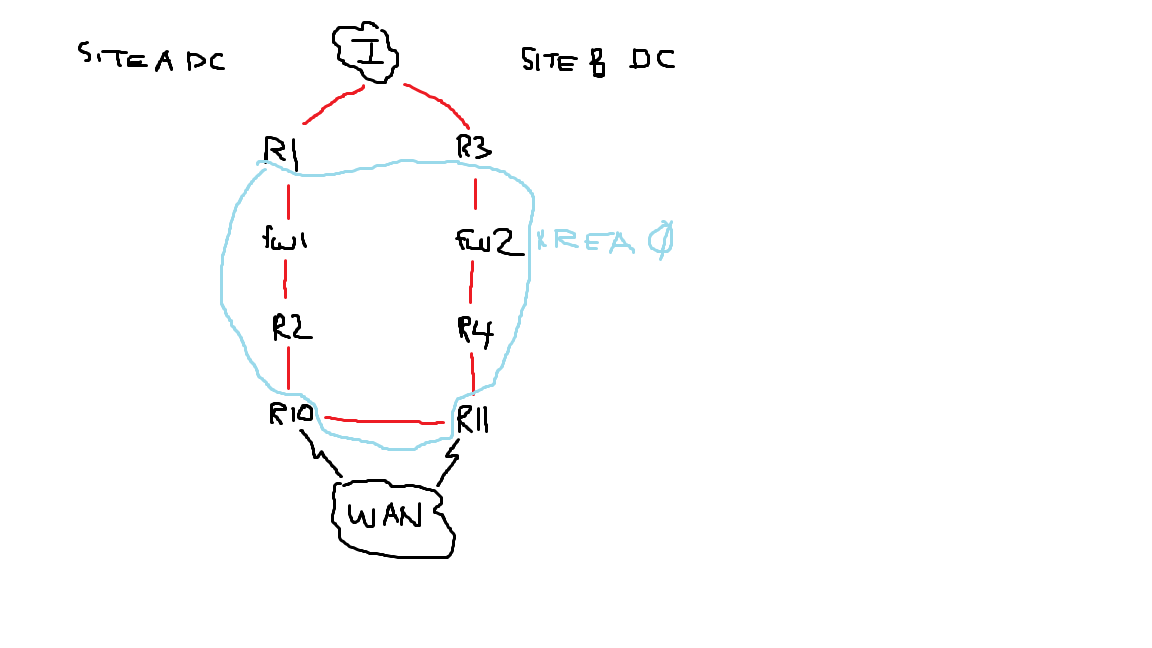
I'll let you know after tomorrow night. I do not want a static route on our Checkpoint firewall (border FW). We have dual providers terminating their service in two diff physical locations. If locationA internet is down, I want the other Internet routers default route to propagate through the OSPF domain.
R1---CPfw1---R2
\
/ OSPF Network
R3---CPfw2---R4
R1 (ISP1) and R3 (ISP3) will be redistributing their default routes. I just want to make sure the CPfw's pass the default-information originate command through. ????
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Well,
You can run IPSLA to outside world on your internal routers and keep the route 0 cost reversed on each side. This way, hosts on the inside of Check Point will be able to get out through any available ISP.
Networks located on DMZ(s) could keep propagating normally.
Inbound traffic to your hosts (i.e. mail, web, etc..) may be a bit trickier, since you’ll have to create conditional NAT rules that will take under consideration where the traffic destined to those is coming from.
Another issue will be the antispoofing for hosts in DMZ: Under normal circumstances, fw is aware of the interface leading to the Internet.
During failover, depending on topology, route 0 may end-up behind internal interface.
If you have class C public addresses, you can run cross-site BGP on the outside of your firewalls to prevent the scenario described above.
Vladimir Yakovlev
973.558.2738
<mailto:vlad@eversecgroup.com> vlad@eversecgroup.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Vlad sorry to bump up an older post can you show me where you can add that control for ospf? was searching in advanced routing settings without luck.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Marco,
Can you restate the question with some specifics?
I'ts been a while since I've looked at this thread and I'll have to get my bearings again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
was looking for a way to monitor ospf neighborship state with gaia os so it look like that for bgp you can monitor your peer state with the screenshot that you took but can be possible too in ospf?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Marco,
I am presently out of the country and do not have an access to my lab.
Please ping me after 16th of October and I'll look into it.
There were also some changes in R80++ versions that should allow for SNMP OSPF neighbor state change monitoring, but I am not sure if you can use that feature, nor have I seen MIBs for that.
Dameon Welch-Abernathy, you have mention a while ago that there were plans to address a detection of upstream connectivity changes other than pinging adjacent devices. Please advise if anything has materialized.
Regards,
Vladimir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Vladimir no worries catch you soon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
With R80.20, BFD (Bidirectional Forwarding Detection) is an option.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If it's not too much trouble, can you drop a link here to the description of that feature?
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is little mention of BFD support in the R80.20 except in the release notes.
There's a hotfix on R80.10 that adds it: Advanced Routing and Clustering Enhancements Hotfix for R80.10
The documentation that comes with that hotfix has a little more about it: R80.10 Advanced Routing Accumulated Hotfix for use with JHF Take 91
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In case anyone runs across this down the road. We finally got this working. Nothing magic, quite simple though. We have 2 ISP's terminating in 2 separate data centers. Our objective was to redistribute the default routes into our OSPF domain from those two Cisco Internet routers. Those default routes are dictated by an IPSLA. If the IPSLA is down, the default route is removed. That all works just fine. The issue was this. The default routes were be redistributed throughout our OSPF domain, but the Checkpoint firewalls never learned them. After hours and hours of CP support we couldn't figure it out. I did not want static default routes on the firewalls. The key to getting this to work was to redistribute the default routes from Cisco into OSPF as type-1. Type-2, checkpoint does not like. I never did get an answer as to why...and I am leaving it at that for now.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Matt,
Can you tell me how you've dealt with the anti-spoofing now that you have 0 routes on multiple interfaces?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Vladimir, all of our interfaces on our firewalls are being redistributed into OSPF. We aren't running into any anti-spoofing problems. This didn't change the direction of any routes, just how we route. Instead of a static default route, the CP's are learning their default route from our Internet router. Does that answer your question?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry, it is not clear to me how this could be possible.
If your topology looks like this:
Internet---R1---(External)-CPfw1-(Internal)---R2----R4---(Internal)-CPfw2-(External)---R3---Internet
And the idea was to get route 0 dynamically from either site, should the primary fails, than the secondary route0 will be behind internal interface of the firewall and thus the antispoofing will not work.
The only exceptions that I can think of is if your site-to-site routing between external interfaces of the firewalls.
But according to your diagram:
R1---CPfw1---R2
\
/ OSPF Network
R3---CPfw2---R4
Do the CPfw1---R2 and CPfw2---R4 signify secondary external interfaces of the firewalls?
Thank you,
Vladimir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Vladimir, everything internal is in the same OSPF domain, including the "internal interfaces" of the internet routers. There is no site to site via the Internet.
Our network is now basically divided in half. The "left" side routes out internet router R1 and the "right" side routes out internet router R3. So any site closer to R1 (OSPF cost wise) routes out the "left" and sites closer to R3 route out the "right" side.
When R1 fails, the "left" side will begin learning the only other default route in our network from R3. Assuming that ISP from R1 is down, incoming traffic is down (no BGP peering with ISP's, for now), but the outbound will route out R3 for our entire campus. Everything heading towards CpFw2 will be from a defined internal networks. Our Internet Fw's are in the same cluster so we have a single rule base we manage. No packets are traversing the CpFw1 external interface if R1 is not distributing its default route. There are no internal networks off R1 or R3.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK. thanks for taking time to describe your deployment scenario.
I see that so long as you do not have anything else connected to your firewalls, this will work.
My doubts were caused by the mistaken assumption that you will have a DMZ(s) defined on each firewall.
If that would have been the case, and the fw1, in your example, would learn alternate route 0 from R2, the topology of fw1 would change. Same goes for fw2.
In the absence of DMZs, the only route of significance is 0 and you'll be completely ignoring the firewall that does not receive it from adjacent ISP router.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 37 | |
| 27 | |
| 11 | |
| 10 | |
| 7 | |
| 7 | |
| 6 | |
| 5 | |
| 5 | |
| 4 |
Upcoming Events
Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 19 Feb 2026 @ 03:00 PM (EST)
Americas Deep Dive: Check Point Management API Best PracticesTue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 19 Feb 2026 @ 03:00 PM (EST)
Americas Deep Dive: Check Point Management API Best PracticesAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


