- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- CheckPoint bridge mode is not working between the ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
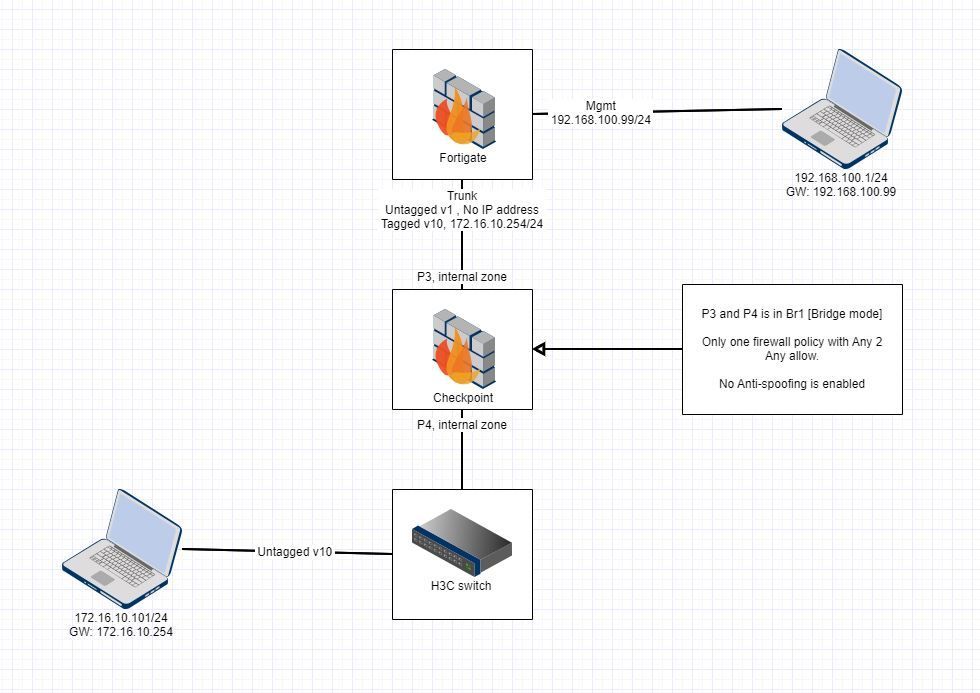
CheckPoint bridge mode is not working between the Fortigate and H3C switch
-------
17/2/2020
-------
Add screen capture on the below reply for further troubleshooting.
-------
16/2/2020
-------
HI all,
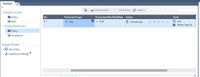
I just have a Checkpoint as bridge mode and have a scanning over the Trunk link.
Both Fortigate and H3C has a Trunk link up already before. Vlan 10 is tagged with untagged VLAN 1.
All my users are in Vlan 10.
They need to have both CP and FG scanning while visiting the internet.
Then we set up port 3 and 4 as br1 on the Check point.
FortiGate connects to p3 while h3c switch uplink to p4.
Both p3 and p4 are in the Internal zone with anti-spoofing disabled.
CP Firewall policy just has the clean up one with any to any accepted.
From the debug flow on FortiGate, I can not find the traffic to the internet, let says the dst. is "1.1.1.1"
Nevertheless, both 192.168.100.1 and 172.16.10.101 can ping mutually and have the debug log result from Fortigate.
I think this proves the CP policy working well?
Interestingly, both Firewall traffic Logging reveal the traffic is accepted if to the internet.
Only no outcome from the debug log result from Fortigate if the dst. is to internet or "1.1.1.1"
I swear to god that FortiGate original settings are good.
As we use it before and everything just normal.
Please someone helps.
Below is the lab topology after the deployment.
22 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do you see the traffic forwarded on Check Point through the bridge? Simple "fw monitor" would answer this question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
From the Firewall policy, I can find the traffic is passed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So is Fortigate side, I can find the traffic is passed.
But no idea why the traffic debug flow can not find the related traffic.
But no idea why the traffic debug flow can not find the related traffic.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
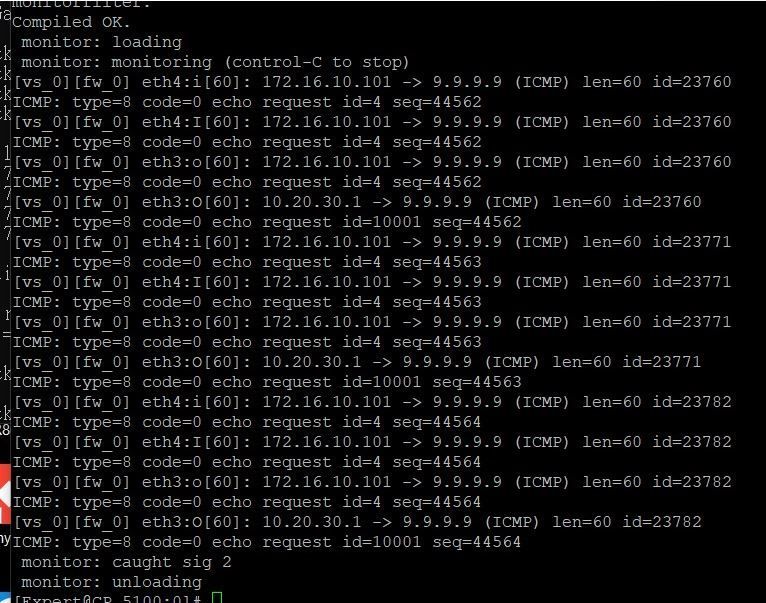
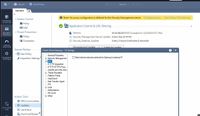
Screen for your referencing:
No output from fw ctl zdebug drop.
And Ping result if to 9.9.9.9:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It is showing Check Point FW is not a problem here. Look outside for some external failure
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The Big O is not appearing from 172.16.10.101 I think?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Uh, I was looking at interface names and did not look at IPs.
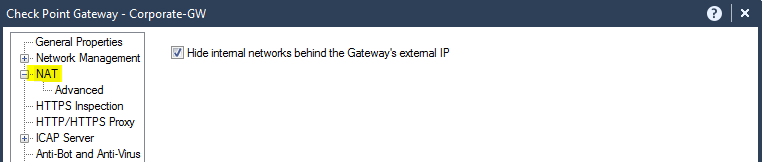
You are correct, it seems FW is NAT-ing the connections, which should not happen on the bridge in the first place. Check your NAT policies.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please have a look at the latest reply.
I have the NAT screen for it.
I even try manually have one to force everything translated as original ...
Well, still the same.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10.20.30.1 - who's this IP belonging to?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That is Checkpoint Br1 ip address before.
I use that for Vlan 1 and mgt ip for UTM update.
Interestingly, 10.20.30.1 is good to passthrough Fortigate over the trunk and access internet
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
and by the way, do you have _another_bridge_ on Check Point for VLAN10?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
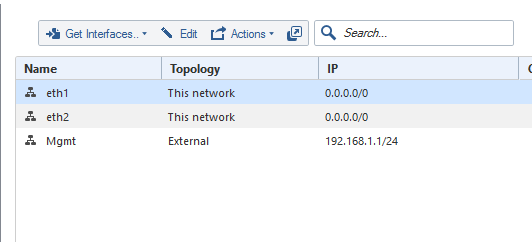
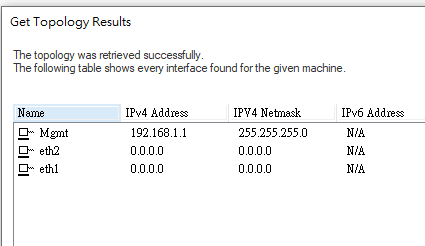
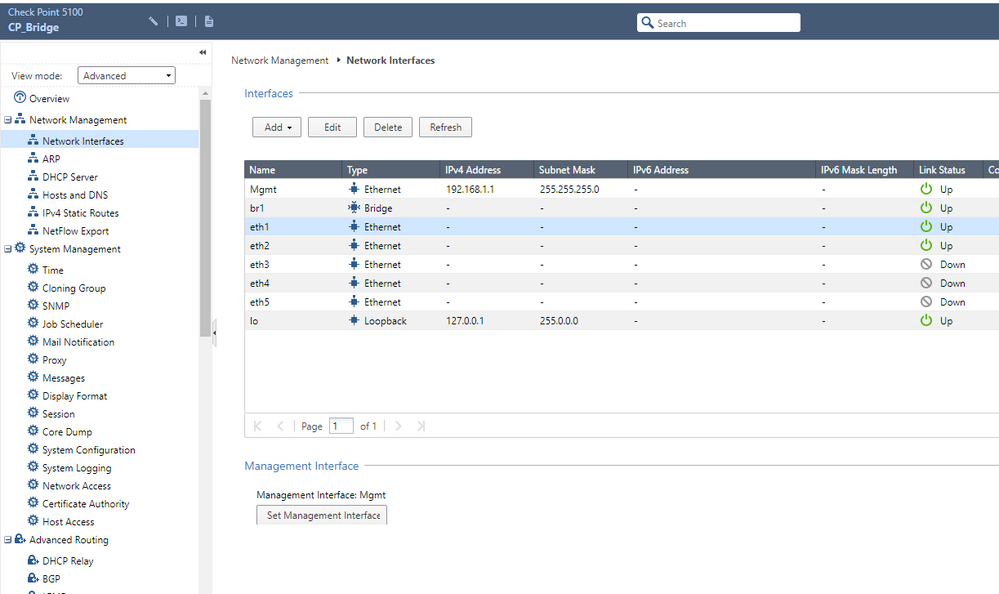
Only Br1 is on the Checkpoint.
I even try no both tag vlan 10 and tagged Vlan 10 to Br1 also.
I even try no both tag vlan 10 and tagged Vlan 10 to Br1 also.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I assume NAT is disabled on the Check Point gateway, what other controls are active?
(Refer also sk101371,sk106319)
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, NAT is disabled on the Check Point gateway level already.
Only the general UTM blades like AntiVirus, IPS, Web filter.
Only the general UTM blades like AntiVirus, IPS, Web filter.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is your firewall and URLF/AppC policy consolidated or in separate layers currently?
Regarding the destination, is it always specified as "Any" versus "Internet" in _all_ applicable rules...
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
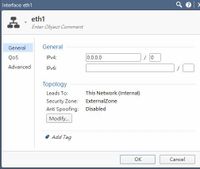
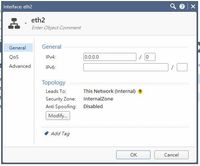
Take a quick look at it:
I try to rebuild the Br1 into Port1 and 2, downgrade to R80.10 and replace the H3C to Cisco 2960 now.
Still no luck.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Per Val's comment, please double check the NAT options/settings on the Gateway object itself.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Bro, I check it more than 10 times really.
No box in NAT of the gateway was checked.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
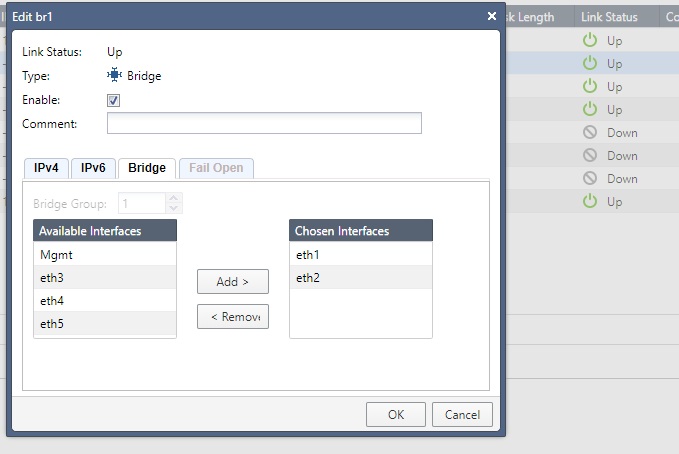
can you please post Bridge config from Gaia and also the GW topology tab?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
All seems to be in order. Yet, after policy push and FW reboot, do you still have ping NAT-ed on the bridge?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi all,
We no longer waste our valued time on it now.
This issue is due to:
1. My test LAN 172.16.10.X/24 just conflicts with the CP built-in SSLVPN subnet. And this causes the default NAT triggered also.
2. DNAT allocation needs to be enabled on CP if you decide to change the CP built-in SSLVPN subnet to others.
Thanks to the TAC finally..... What the ... Great CP we have got. >_>
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 15 | |
| 13 | |
| 10 | |
| 8 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 2 | |
| 2 |
Upcoming Events
Thu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter